Online audio/video streaming can consume most of your bandwidth. To save your bandwidth, you might want to block online steaming traffic on your network.
Generally speaking, online streaming can run on different protocols:
1. Video websites, like youtube. You can watch video directly on the webpages.
2. Standard Real Time Streaming Protocol(RTSP).
3. P2P based streaming products, like pplive, ppstream.
4. Video downloading websites.
Therefore, for complete blocking of video streaming, you need to block all above video traffic.
First, block “streaming” category websites:
Second, block downloading of video files:
Third, blocking RTSP and other online streaming protocols:
More information, please check “protocols supported by WFilter”.
Other related links:
How to block internet downloading?
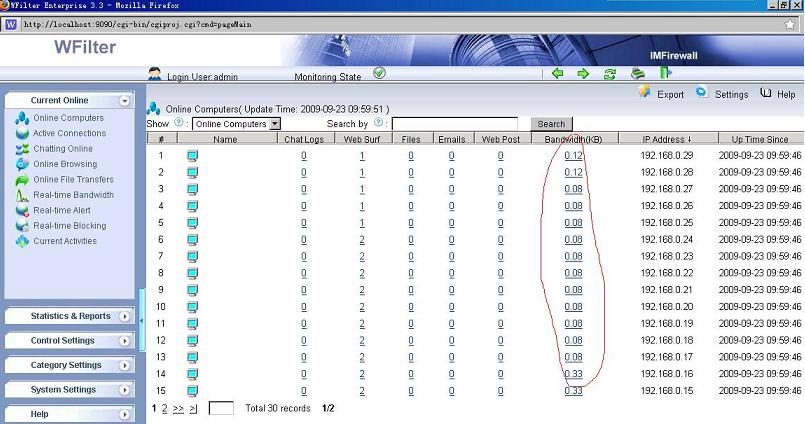
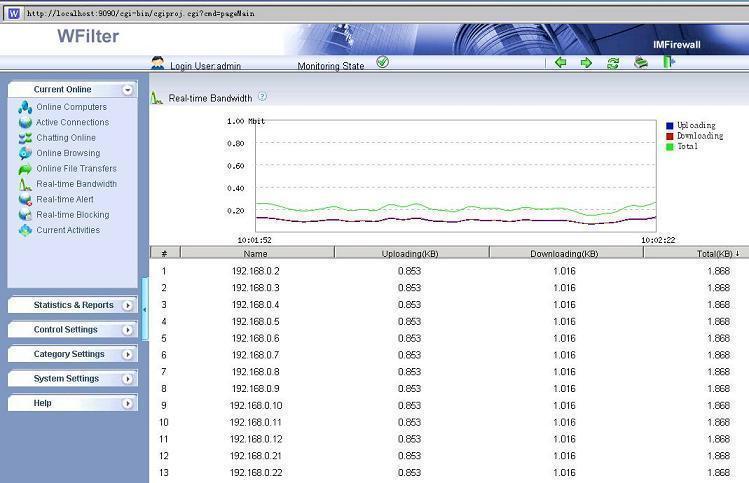
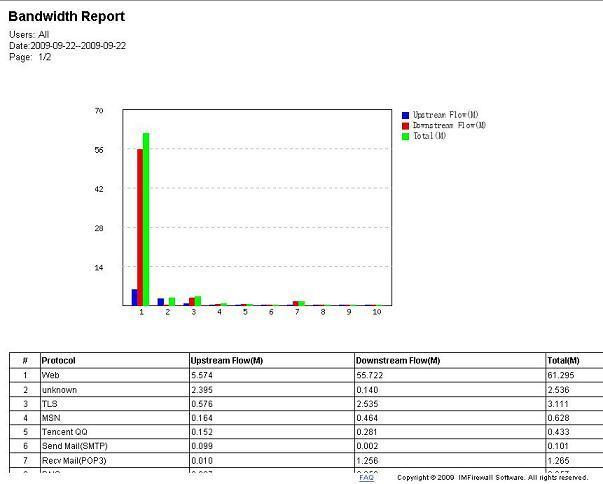
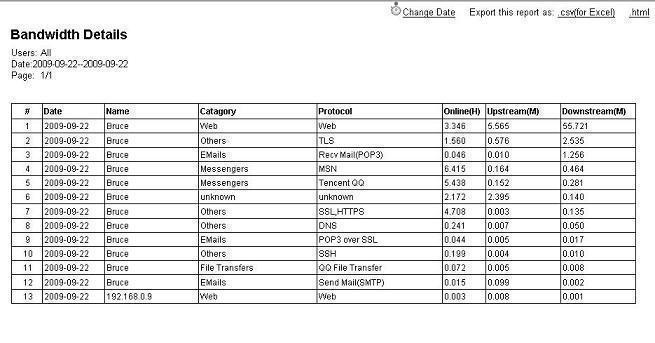
How to monitor internet bandwidth?
How to monitor internet usage on company network?
Internet monitoring software for business
How to filter web surfing?
How to block websites and restrict internet access?
How to Block Bittorrent and bitcomet?
How to block msn file transfer?
How to block certain websites to save your productivity?
How to block AIM using WFilter