Online storage solutions provide client applications and webpages for uploading and downloading files to and from their service. To stop business sensitive data being uploaded, you may want to block file storage websites and certain kind of applications.
In this post, I will try to explain the detailed steps with WFilter Enterprise.
First you need to install WFilter and make a correct deployment. Then you can add blocking policies.
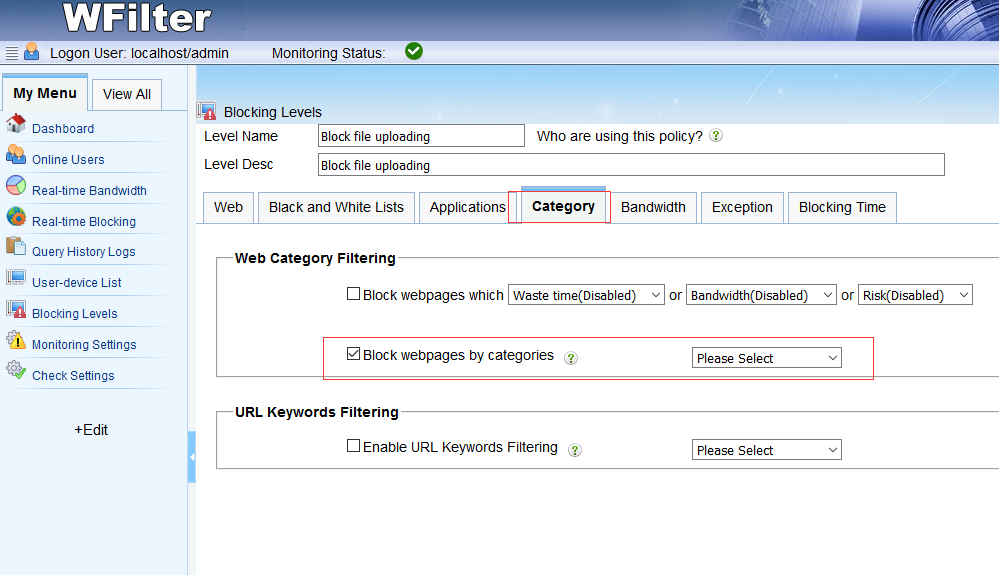
1. Block online storage websites.
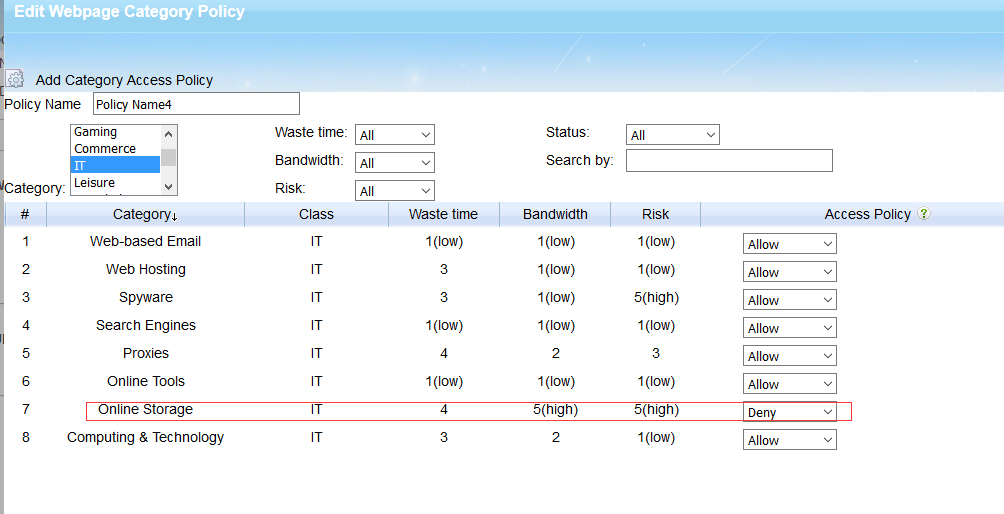
To block websites by categories, you need to enable “Block webpages by categories” and click “New…” in the dropdown list to create a category filtering rule. Then set “online storage” to “Deny”.
This option enables you to block most online storage websites, including both http and https sites.(ie: wetransfer.com)
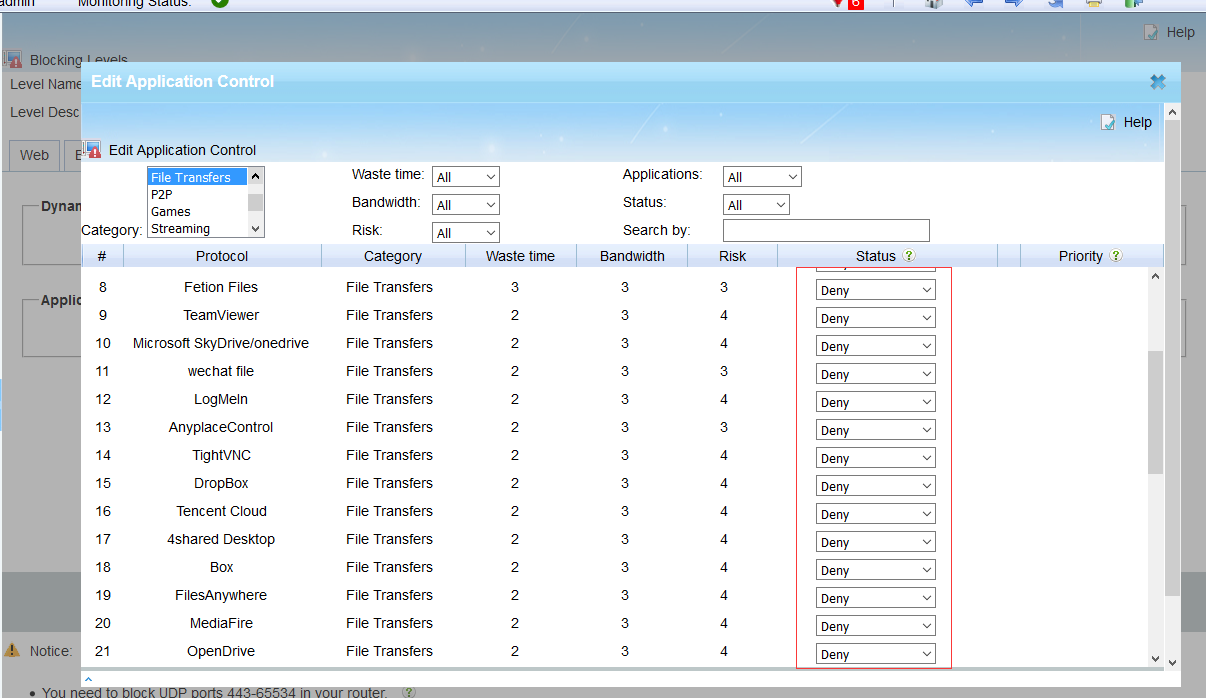
2. Block file transfer applications.
To block file transfer applications, please click “edit” in “Applications” of your blocking policy. Then set certain protocols in “File transfers” to “Deny”. This option blocks pc and mobile applications clients. A supported protocol list can be found at WFilter supported protocols list.
Please note that the supported protocols and websites of WFilter can not cover all file transfer types. If you want to block an application not in the supported list, please feel free to contact us. We will add it for you by free.
Also, for complete blocking of file transfers, you’re recommended to enable “website whitelist” of WFilter, so only work related websites can be accessed. And you also need to forbid usb and bluetooth devices.