1. Add a “block facebook” policy.

2. New a website black list.

3. Define ip ranges to be blocked.

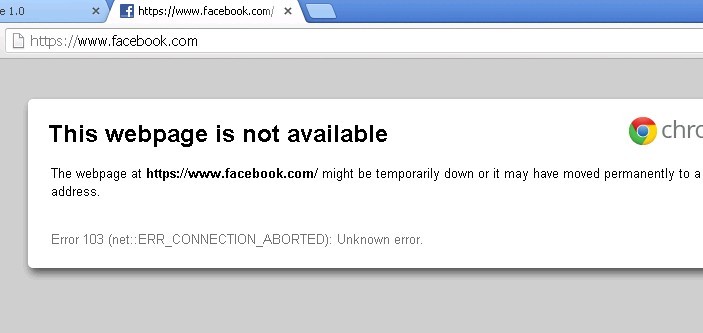
4. Visit facebook to check.

Https facebook is also blocked.
1. Add a “block facebook” policy.

2. New a website black list.

3. Define ip ranges to be blocked.

4. Visit facebook to check.

Https facebook is also blocked.

Gargoyle is an OpenWrt distribution which aims to be easy to use through a simplified Web interface. Gargoyle can extend your wireless router into a powerful Linux system. even if your router hardware does not support “port mirroring” function, you can also enable traffic mirroring by software mirroring.
This blog will guide you to install “port-mirroring” program in your Gargoyle router and deploy WFilter for internet monitoring and filtering. We assume you already has an Gargoyle router, if not, please check Gargoyle homepage to get the latest firmware.
Port-mirroring is an open source project sponsored by IMFirewall Software, it is designed to mirror network traffic on linux systems.
For detailed installation guide, please check Port-mirroring open source packet mirroring. In this guide, let’s take linksys wrt54g router as an example.
Steps:
a). opkg update.
b). opkg install http://port-mirroring.googlecode.com/files/port-mirroring_1.3-1_12.09_brcm47xx.ipk
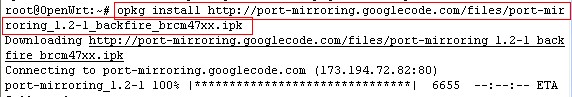
Because gargoyle is based on openwrt attitude adjustment 12.09 branch, we need to install the build for openwrt 12.09.
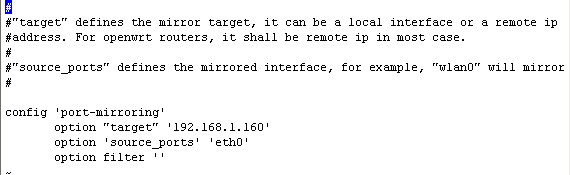
You need to edit /etc/config/port-mirroring to set the mirroring target and mirrored source interfaces.
In this example, we choose “eth0″ wireless adapter as the mirrored source interface.
/etc/init.d/port-mirroring start
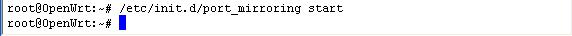
Now WFilter shall be able to monitor client computers.
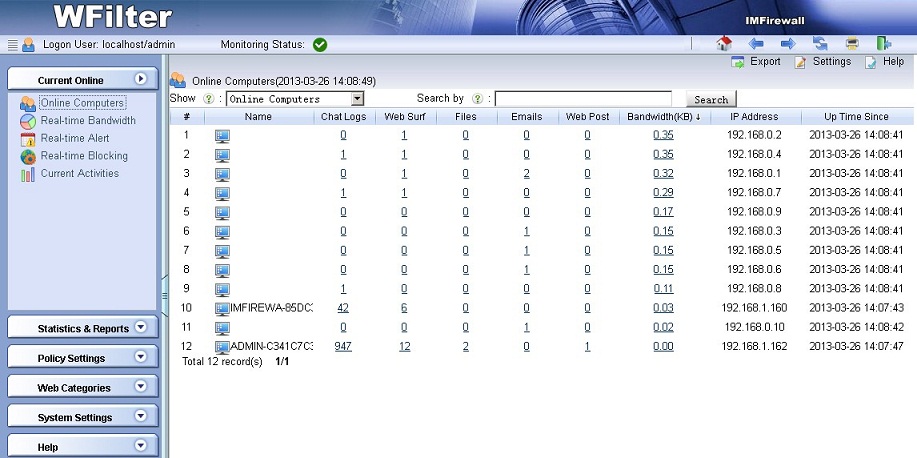
The “–tee” option of iptables can mirror network packets to a target ip address. With this feature, you can deploy monitoring easily when you have an embed Linux router.
In this tutorial, we will guide you to deploy WFilter using a Tomato router(firmware version: v1.28).
Enable “SSH Daemon” in “Administration” – “Admin Access”.
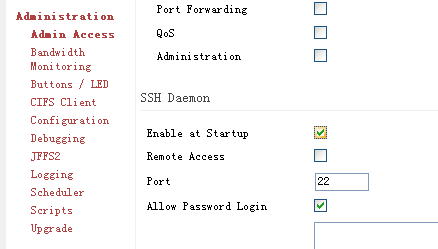
Login into your Tomato router using any ssh client.
For “–tee” option to work, you need to enable the “ipt_ROUTE” module, which is not enabled by default.
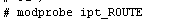
In this example, we forward packets to “192.168.1.100″.
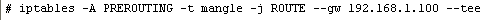
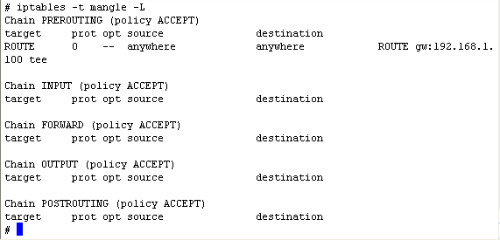
You can list your iptables rules to check whether this rule is successfully added.
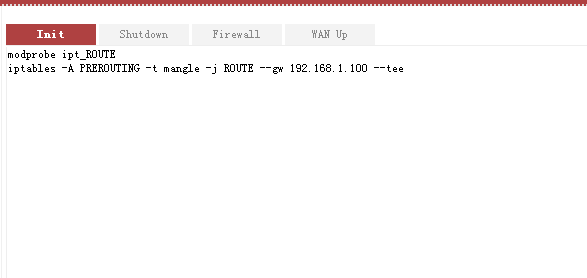
If you want this rule to exist after router rebooting, you need to add these two commands into the startup scripts in “Administration – Scripts”.
modprobe ipt_ROUTE
iptables -A PREROUTING -t mangle -j ROUTE –gw 192.168.1.100 –tee
Please notice, “iptables” will not forward original mac addresses of packets. Therefore, you can not use “by mac address” monitoring mode of WFilter, use “by ip address” instead.
Done.