Routing and Remote Access is a network service in Microsoft Windows Server 2008, Windows Server 2003, and Windows 2000 Server that can provides Network address translator (NAT) for connecting a private network to the Internet. An example network topology is as below:
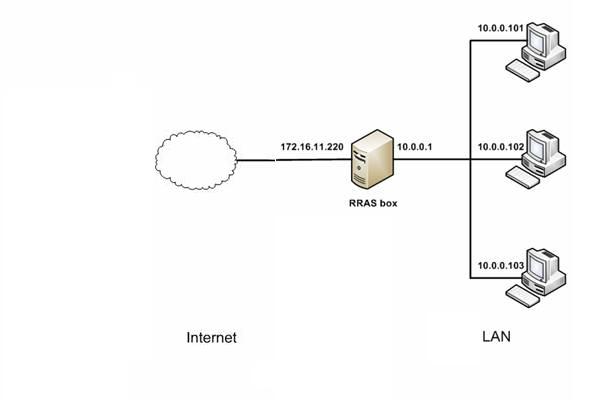
Since all internet traffic goes through the RRAS server, it’s very simple for you to monitor and filter internet activities: “just install WFilter in this server.”
The RRAS server has two adapters: the internal NIC and external NIC, you shall be able to see two adapters in the “monitoring adapter settings” of “System Settings”->”Monitoring Settings”.
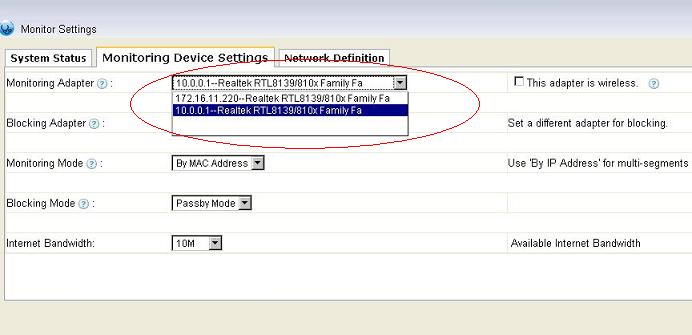
We recommend you to choose the internal NIC as the monitoring and blocking adapter, because you will be able to monitor, block and report on individual network computers.
However, if you choose the external NIC as the monitoring and blocking adapter, WFilter will treat the whole network as one computer, because the RRAS server will translate all subnet ip addresses to its public ip address.
We have noticed that some users prefer to monitor on the internal NIC to save license number, because you only need ONE 1-user license to monitor the public ip address. However, we recommend you not to do it, because this is not WFilter designed to work, and there might have an over-blocking issue for some p2p protocols.
More information, please check “WFilter Enterprise”.
Other related links:
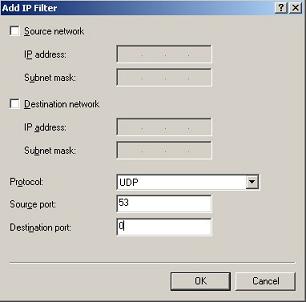
How to block UDP ports in RRAS windows server 2003?
How to block internet downloading?
How to monitor internet usage on company network?
Internet monitoring software for business
How to filter web surfing?
How to block websites and restrict internet access?
How to block HTTPS websites on my network?