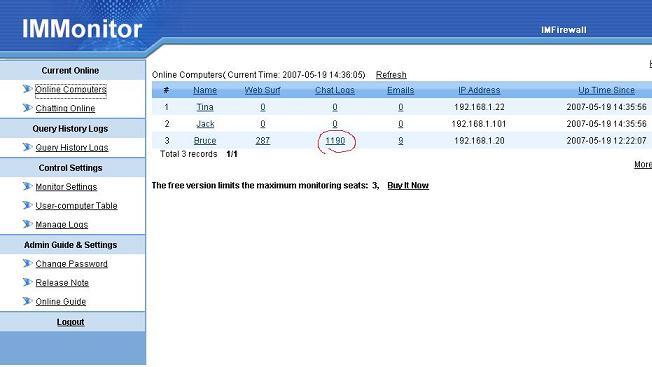
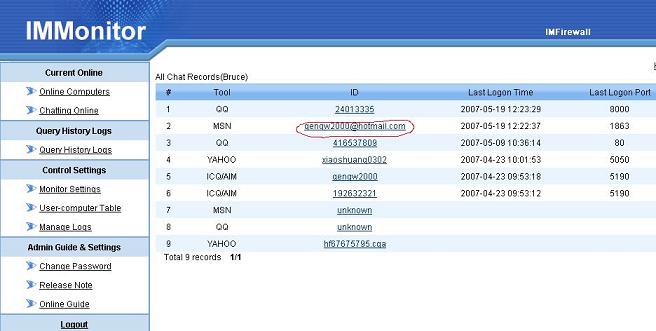
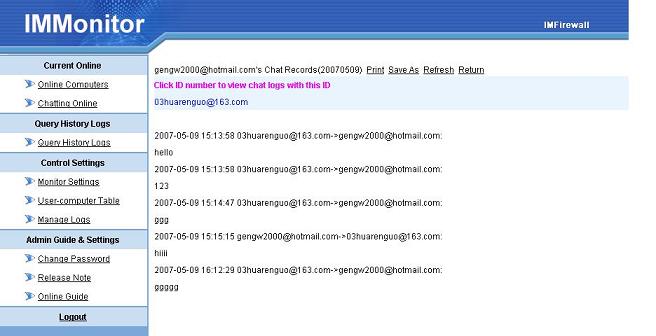
WFilter Deployment
—- CISCO2950 + ISA2004
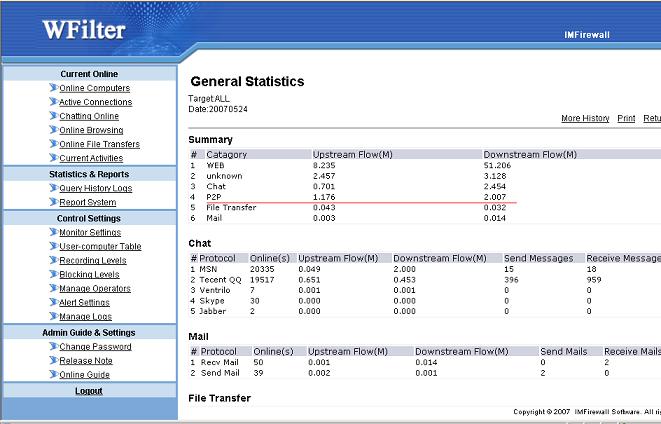
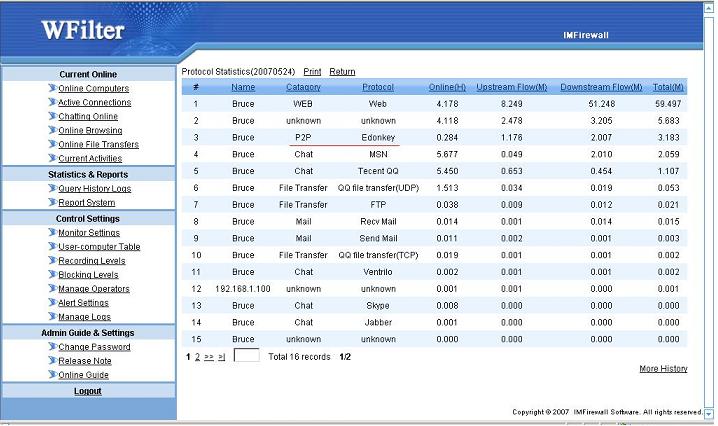
Company A use ISA server 2004 as the proxy server, a cisco 2950 switch as the central switch.
The topology diagram:
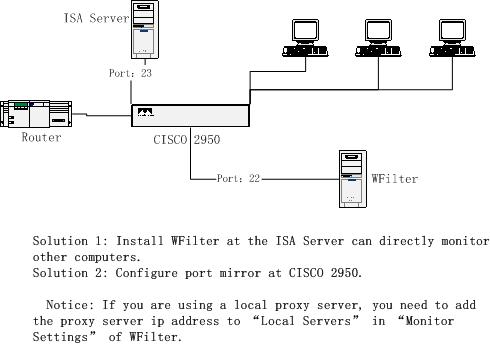
For this kind of topology, we have two solutions:
Solution 1: Install WFilter at the ISA server computer can directly monitor all computers.
Solution 2: Install WFilter at another computer and configure port mirror at cisco 2950.
Notice: By default, WFilter only analysis traffic between local network and the internet. So if you are using a local proxy server, WFilter will not analysis the traffic between the proxy server and the client computers by default. You need to add the proxy server ip address to “Local Servers” in “Monitor Settings” of WFilter to make WFilter work.
How to configure port mirror of CISCO 2950?
As indicated in the above diagram, the ISA server is connected to port 23 of the switch and WFilter is connected to port 22. To make WFilter work, you only need to mirror port 23′s traffic to port 22.
Syntax:
monitor session session_number {destination {interface interface-id [, | -] [encapsulation {dot1q}] [ingress vlan vlan id] | remote vlan vlan-id reflector-port interface-id} | {source {interface interface-id [, | -] [both | rx | tx] | remote vlan vlan-id}}
In this example:
1. Set port 23 as the source mirror port
monitor session 1 source interface Fa0/23
2. Set port 22 as the destination port
monitor session 1 destination interface Fa0/22 ingress vlan 1
Notice: By default, the mirror port of cisco 2950 is recv-only. However, WFilter shall be able to send packages to implement block features. So in this example, we add “ingress vlan 1″ to enable send of port 22.
Some cisco switch do not support ingress syntax, if your switch does not support ingress, you can set a different “blocking adaptor”. Please follow below steps:
1. Set port 23 as the source mirror port.
monitor session 1 source interface Fa0/23
2. Set port 22 as the target mirror port(recv-only)
monitor session 1 destination interface Fa0/22
3. Add a network card in the computer with WFilter install on, connected to a normal port of the switch.
4. Change the “blocking adatpor” to the new added adaptor in “Monitor Settings” of WFilter.
WFilter related features:
Chat Monitor, Monitor employees, internet monitor, msn chat monitor, aim monitor, yahoo monitor, block p2p, block msn, block aim, block yahoo, block messenger, filter internet.