How WFilter works to monitor and archive internet activities?
WFilter is an enterprise Internet filtering software program. A business or
organization can implement its Internet communication policy into
WFilter and let it perform the work.
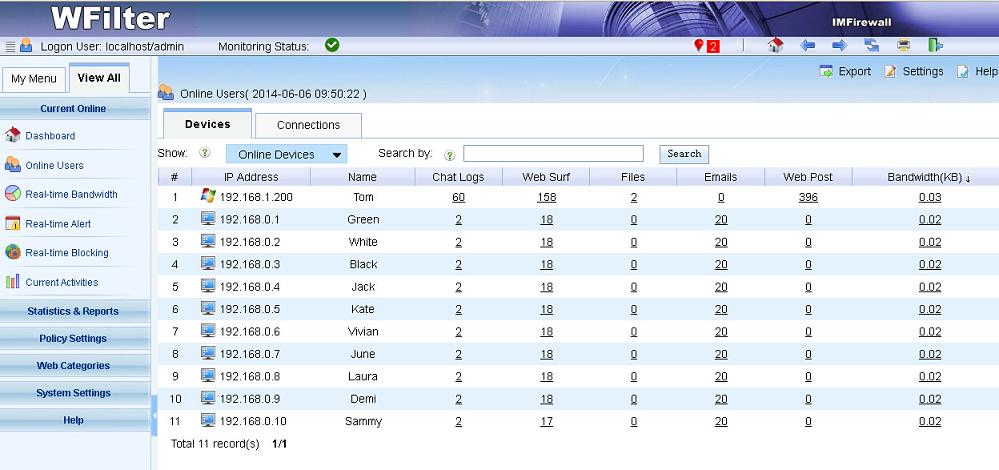
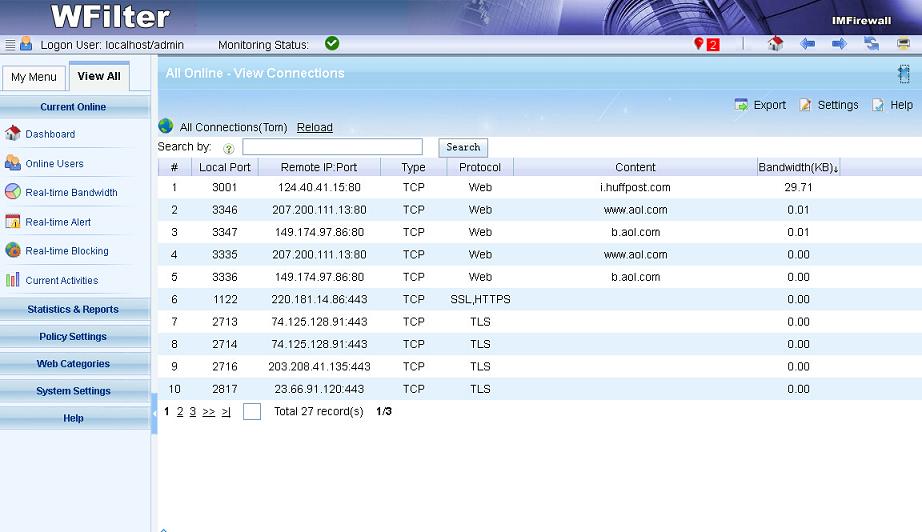
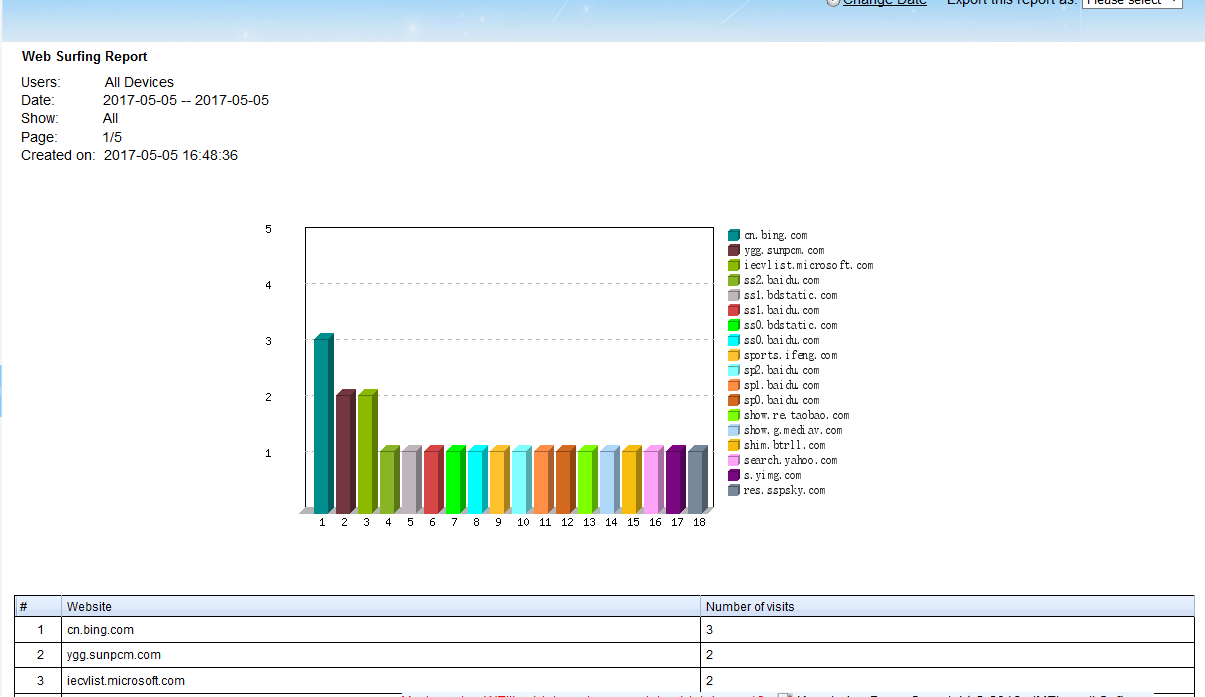
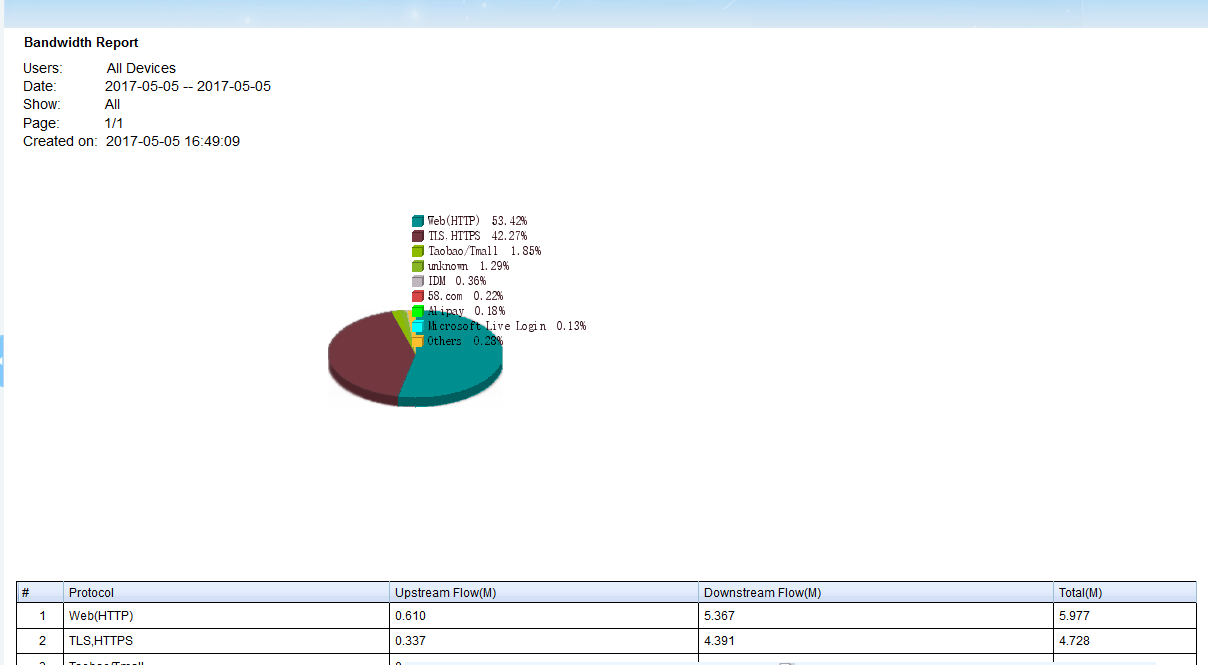
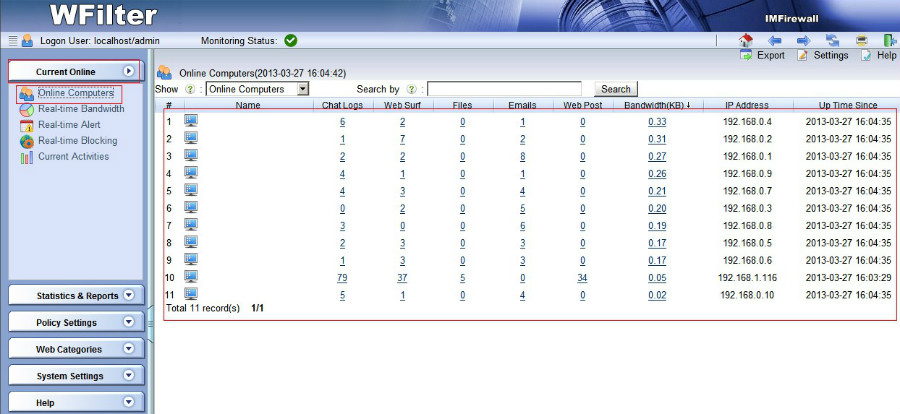
WFilter intercepts, records and monitors Internet behaviors of users
on a network, for the purpose of ensuring policy compliance, or
measurement on job performance in an organization.
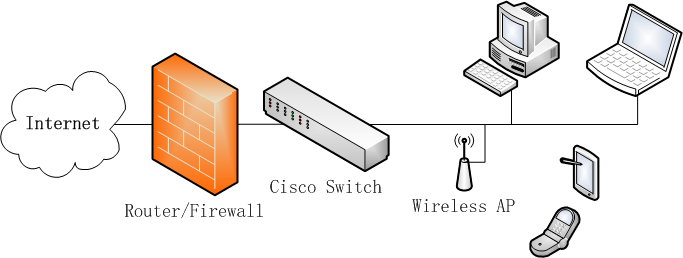
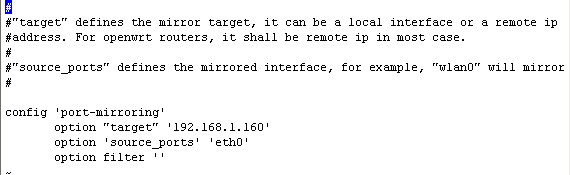
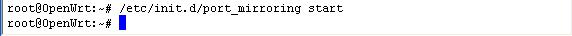
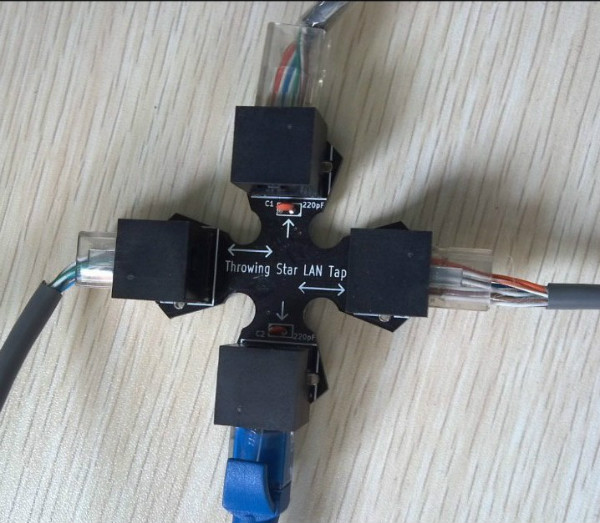
A mirroring port replicates the data from other ports or VLAN’s. To monitor all internet activity, WFilter needs to be connected to a mirroring port of your switch. And the mirroring port shall be configured to mirror your internet traffic.
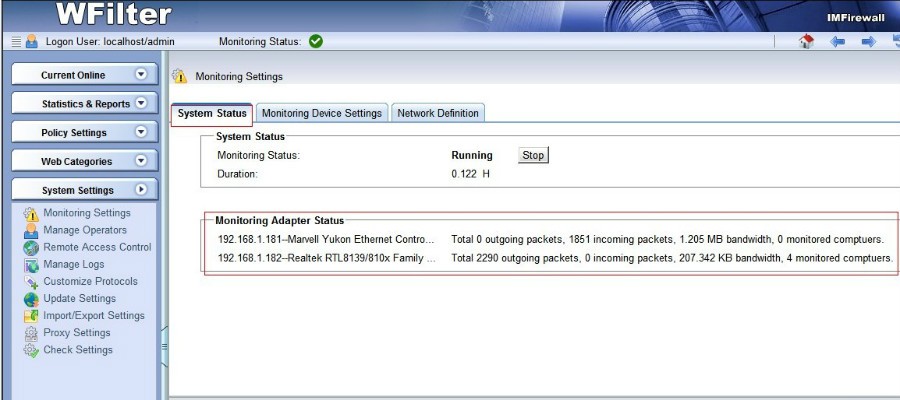
When connected to a mirroring port, WFilter gets packet copies of all internet traffic, then decodes and saves them into log files. This is how WFilter works to monitor internet usage.
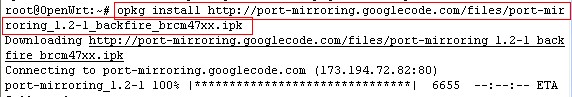
For more information about how to setup port mirroring, please check: WFilter Deployment Examples.
To check whether your port mirroring is properly configured, please check: How to check whether port mirroring is properly configured?
If you don’t have a manageable switch, you need to setup a windows gateway or proxy server to do monitoring, please check: How to monitor internet usage without a manageable switch?
How WFilter works to block internet connections?
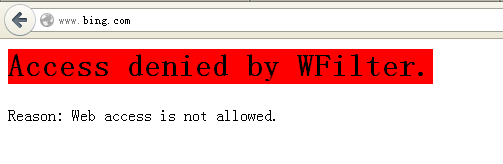
Many users had asked: “Since WFilter only handles packet copies and the original packets don’t pass through WFilter machine, how WFilter works to block internet connections?”
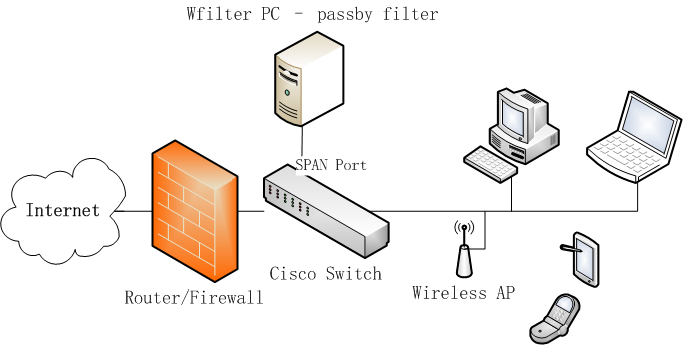
Actually, there are two filtering technology: pass-through filtering and pass-by filtering.
With a pass-through filtering solution, packets shall pass through the filtering product; if a packet needs to be blocked, the filtering product just drop it.
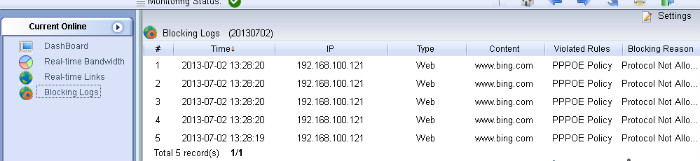
However, a pass-by filtering product only handles copies of network packets, it can not hold the original packets. Therefore, it sends RST packets to terminate TCP connections. This is how WFilter works to block connections.
Please notice:
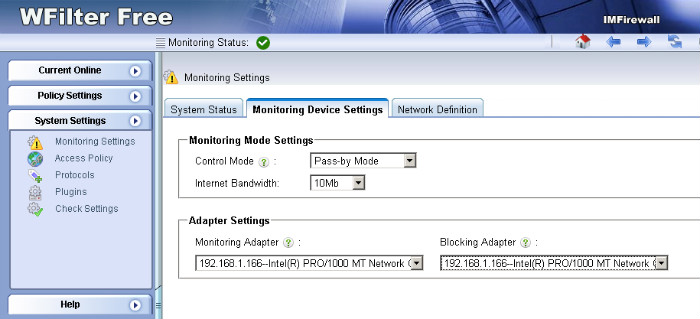
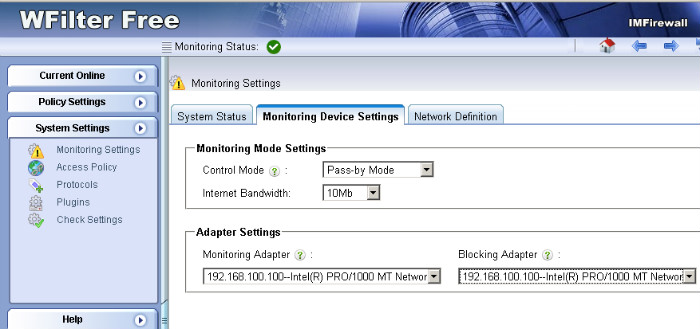
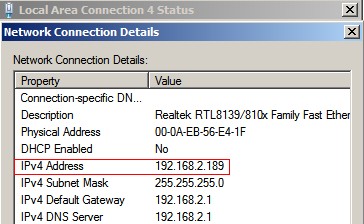
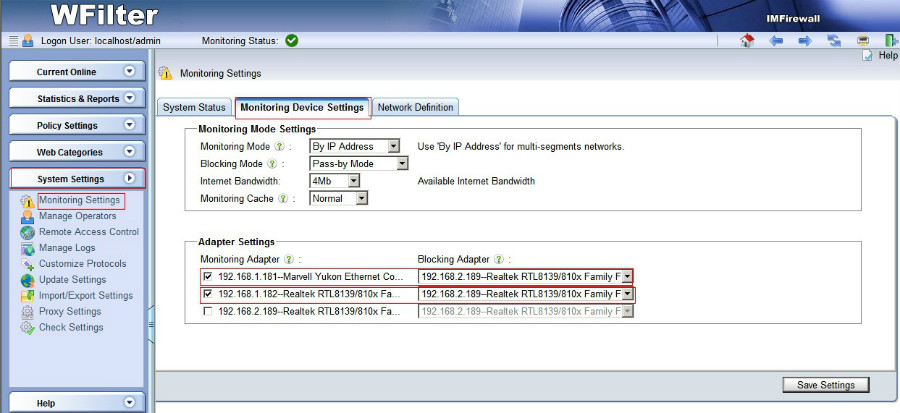
1. Since WFilter needs to send RST packets to block a connection, the “blocking adapter” of WFilter shall be able to access your network. The blocking adapter shall be configured in “System Settings”->”Monitoring Settings” of WFilter.
2. Some switches do not allow outgoing traffic on the mirroring port, if so, you need to setup a separate NIC as the blocking adapter. Even outgoing traffic is allowed on the mirroring port, we recommend you to use a secondary NIC for blocking when you’re managing over 100 computers. Otherwise, the monitoring adapter will be overloaded.
3. If you have multiple VLANs, the blocking adapter shall belong to a VLAN which can communicate with other VLANs.
4. Sometimes you might need to set “Automatic Metric” of the blocking adapter for windows to recognize this adapter as the primary adapter. Please check this blog topic: Blocking adapter doesn’t work when using two network cards with WFilter.
For more information about difference of the two filtering solutions, please check: What’s the difference between Pass-by filtering and Pass-through filtering?
More details about WFilter filtering technology, please check: WFilter Technologies and Security