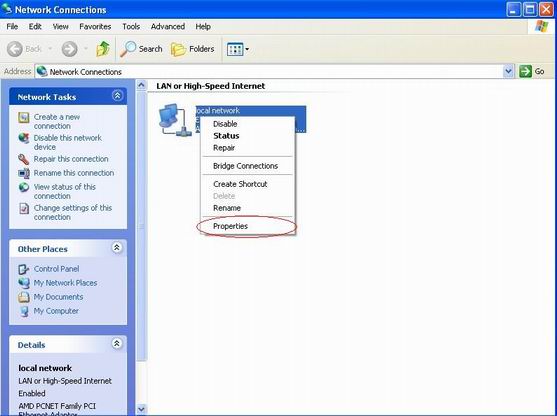
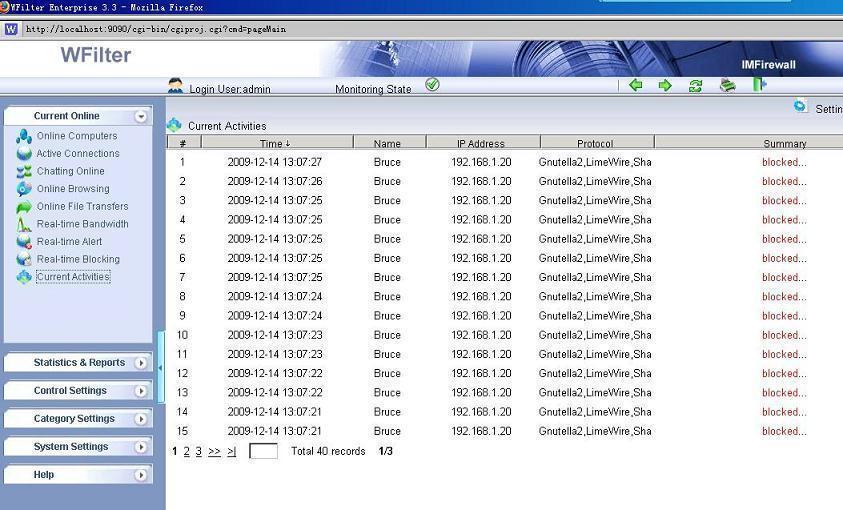
Some switches does not allow outgoing traffic on a mirroring port. In this case, WFilter needs a separate blocking adapter to send blocking packets. And if you’re monitoring and filtering more than 100 computers, we recommend you to use a different blocking adapter as the monitoring adapter.
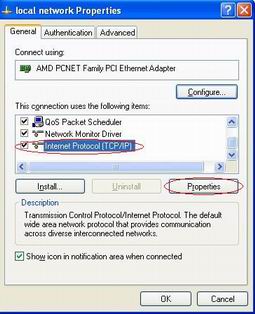
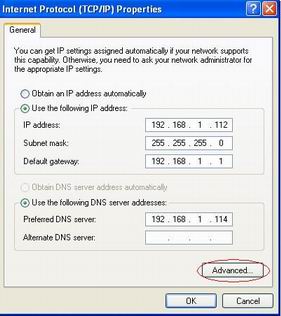
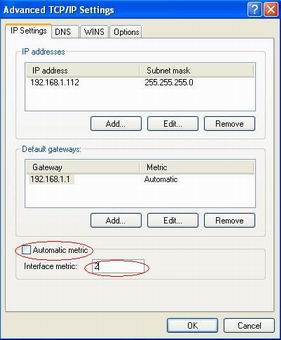
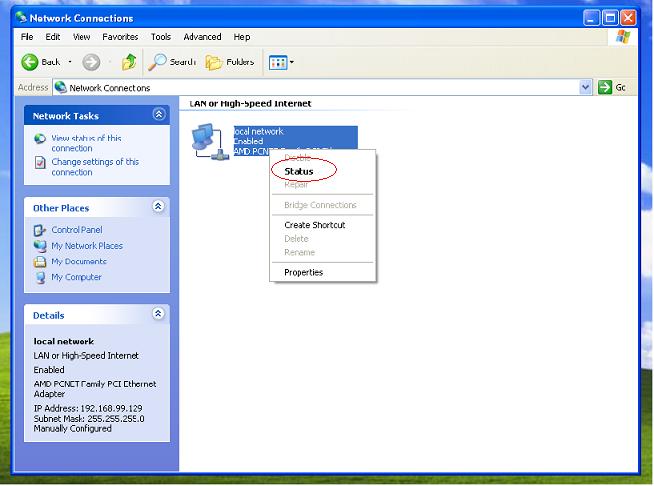
When the two network cards are installed, we will want the Windows system to use the blocking adapter to access your network. However, sometime the Windows system might pick up the monitoring adapter and fails to connect to your network. This problem can be resolved by the “Automatic Metric” setting in Windows.
A metric is a value that is assigned to an IP route for a particular
network interface that identifies the cost that is associated with
using that route. The Automatic Metric feature is configured independently for each network interface in the network. This feature is useful in situations where you have more than one
network interface of the same speed, for example, when each network
interface has been assigned a default gateway. In this situation, you
may want to manually configure the metric on one network interface, and
enable the Automatic Metric feature to configure the metric of the
other network interface. This setup can enable you to control the
network interface that is used first in the routing of IP traffic.
In our case, the “Automatic Metric” of the blocking adapter shall be smaller than the monitoring adapter. So by setting “Automatic Metric” of the blocking adapter to “1″, and the monitoring adapter to “2″, Windows system will use the blocking adapter to access your network.