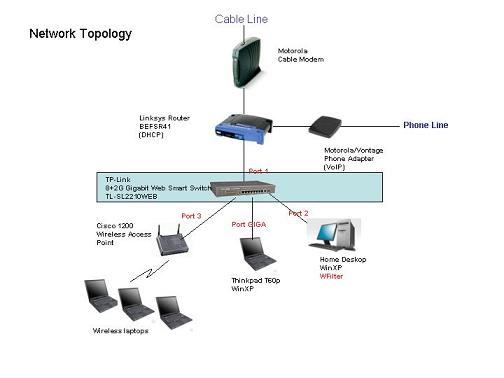
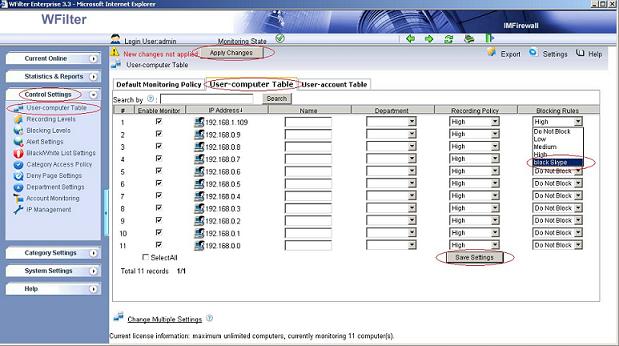
WFilter blocking denial page presents a blocking message to blocked users when a web page is blocked. Sometimes, you may want to add your logo image into WFilter blocking denial page.
This tutorial will guide you to add a logo image with “WFilter Enterprise 3.3″.
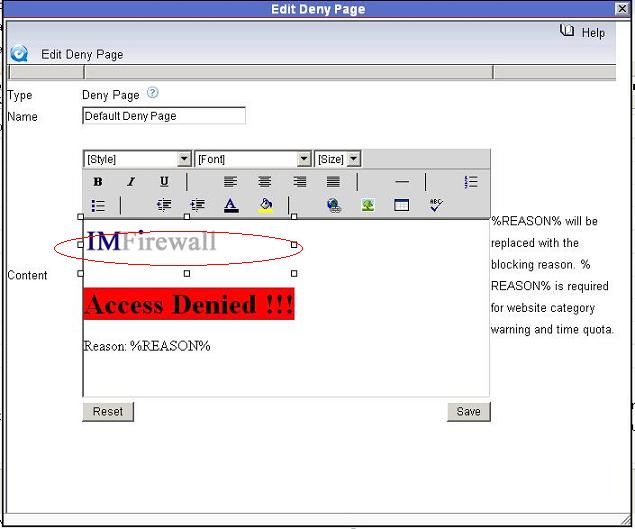
1. It is simple to add your logo when you have a website with this image. As you can see in below figures, just click “Add image” and input your logo url when editing a denial page.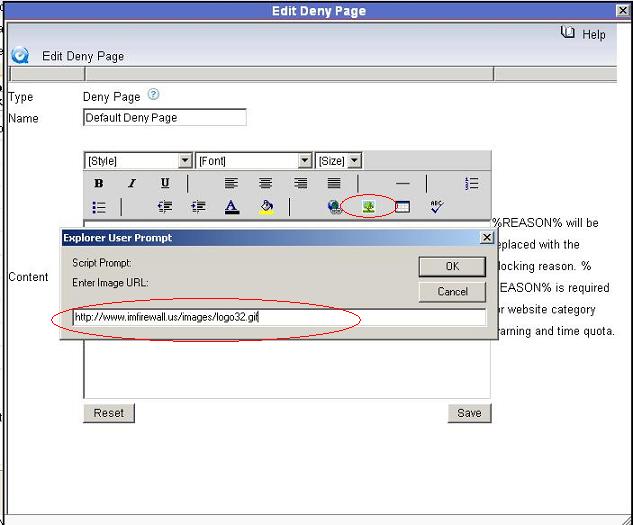
2. However, if you don’t have an available website, you need to upload your image file to WFilter “image” directory for WFilter to find it. Please follow below steps:
1). Copy your image file to “www/image” directory of WFilter.
2). Click “Add image” in certain denial page, please notice you need to input full url address of your logo here. For example, if the IP address of WFilter computer is “192.168.1.20″, you need to input “http://192.168.1.20:9090/image/yourlogo” here. Do not use “http://localhost:9090/image/yourlogo”.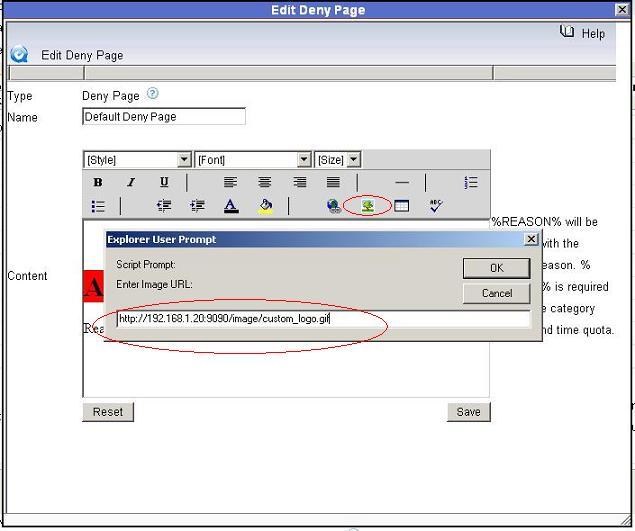
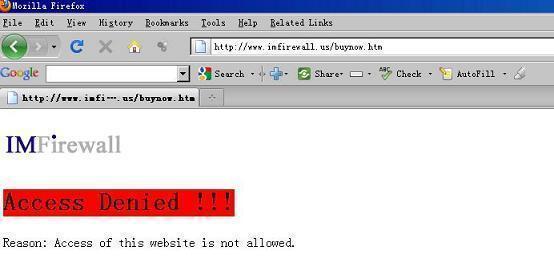
Webpage being blocked:
3. If you’re familiar with HTML code, you also can edit the
denial page source manually in “config/Denypage” directory of WFilter.
More information, please check “WFilter Enterprise”.
Other related links:
How to block internet downloading?
How to monitor internet usage on company network?
Internet monitoring software for business
How to filter web surfing?
How to block websites and restrict internet access?