What is port mirroring?
Usually, a computer connected to a switch or a router can only receive its own network packets. A switch with port mirroring function allows you to monitor network packets from a mirroring port.
With port mirroring is enabled, the switch sends a copy of all network packets seen on one port (or an entire VLAN) to another port, where the packets can be analyzed.
How to monitor network without a port mirroring switch?
There’re three methods to monitor your network without a manageable switch.
1. Using a broadcasted Hub
A broadcasted hub is a data packet repeater commonly used in broadcast networks.
Most broadcasted hubs provide a uplink port to connect with a up layer device. You shall connect the up layer device to the uplink port of the hub (Note: Do not use the port next to the uplink port).
However, most broadcasted hubs only work in 10Mb speed, and all the computers connected to the hub will share the bandwidth, which is not so fast as a switch. So we recommend you use a manageable switch instead.
2. Windows Gateway, Proxy Server or Bridge
Windows Gateway
If a port mirroring switch is unavailable, you can setup a windows gateway by your network edge. With an internet monitoring/filtering product in this windows gateway,
you will be able to monitor all internet traffic of network computers.
How to configure Windows 2008 Server IP Routing?
Proxy Sever
A Proxy Sever is a computer that offers a network service to allow clients to make indirect network connections to internet.
Like the gateway solution, you also can do monitoring/filtering in the proxy server. To make things simple, some proxy servers have monitoring/filtering modules integrated,
while some monitoring/filtering programs also have a proxy module integrated.
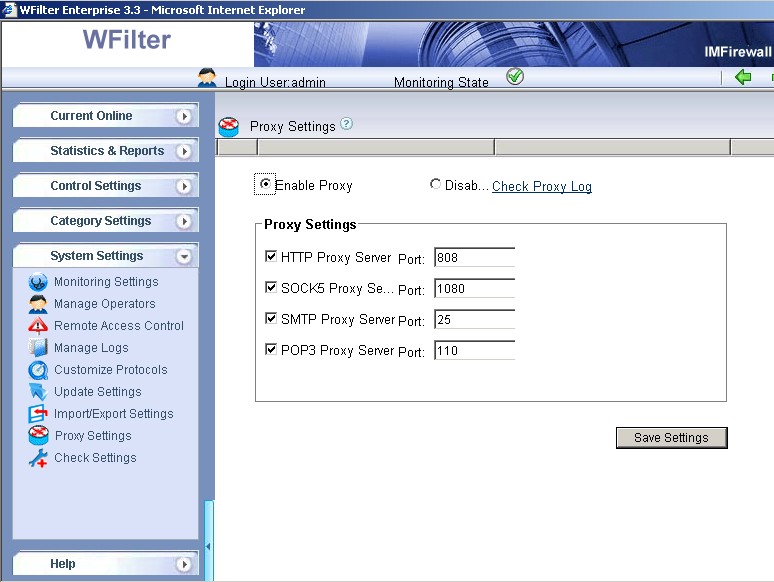
For example, you can easily enable the proxy server service in WFilter enterprise. For more details about WFilter proxy settings, please check:
http://www.wfiltericf.com/help/doc/deploy_proxy.htm
Bridge
Bridges (sometimes called “Transparent bridges”) work at OSI model Layer 2. Bridges just forward data depending on the destination address in the data packet.
By deploying a bridge in your internet entrance, you can setup a monitoring product in this bridge to monitor internet activities of your whole network.
3. ARP Spoofing
ARP spoofing, also called ARP Cache poisoning, is one of the hacking methods to spoof the contents of an ARP table on a remote computer on the LAN. With ARP spoofing,
you act as a relay server between client computers and the real gateway, so you will be able to monitor their traffic. However, as a hacking technology, ARP spoofing will make your network unstable.
So I recommend you not to use it unless necessary.