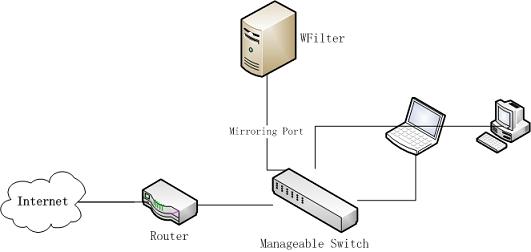
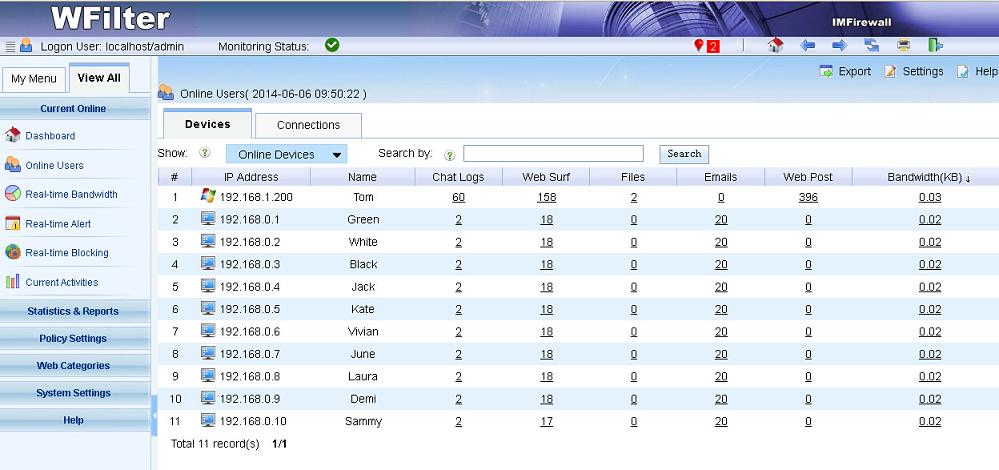
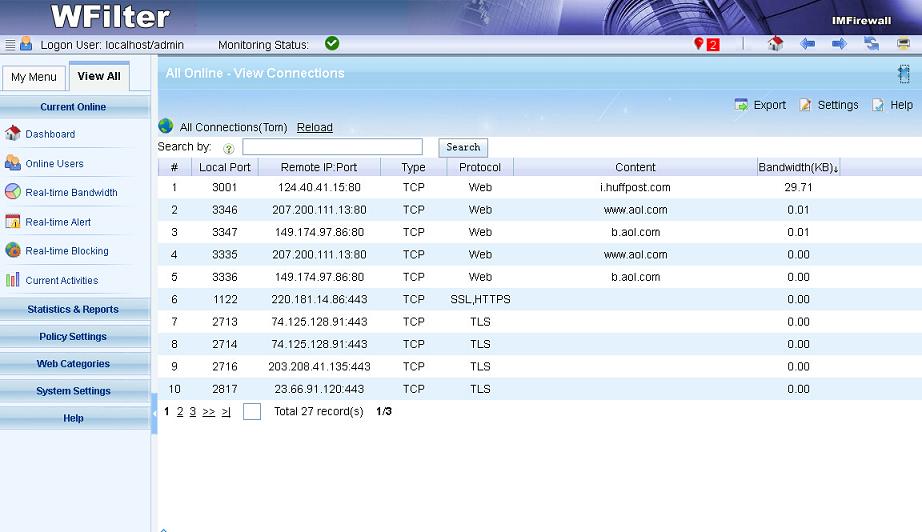
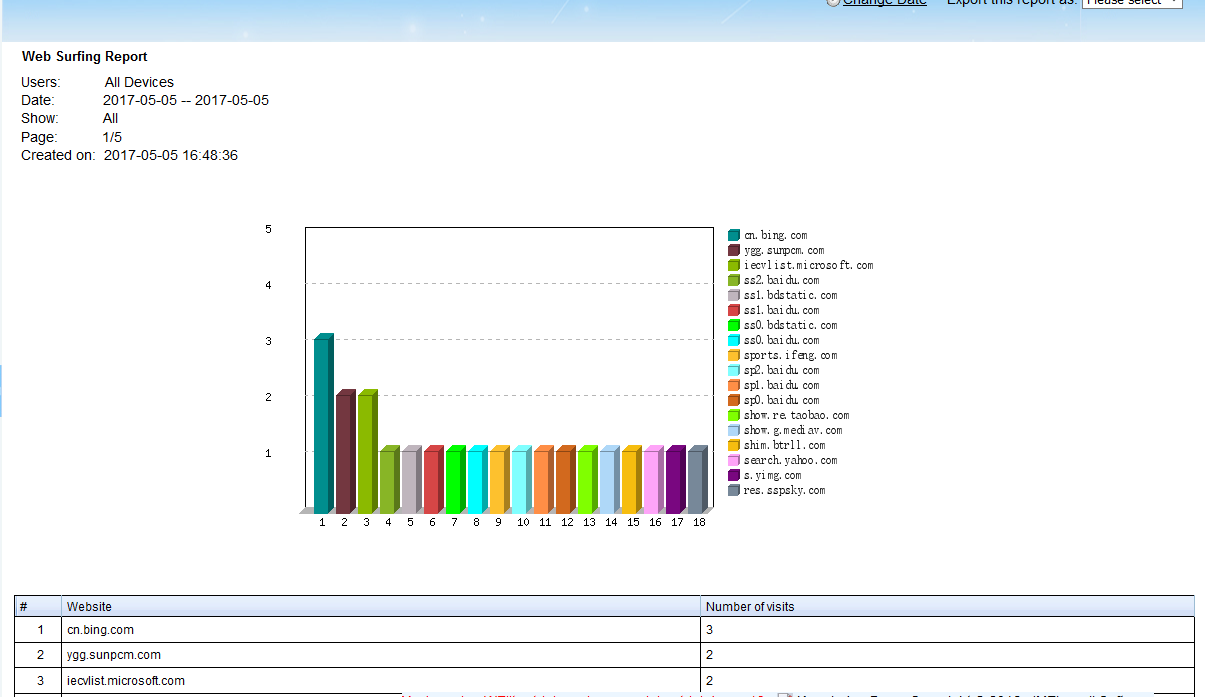
As a network professional, when things go wrong in your network, the right tools are required to minimize network downtime.
In this post, I will reveal you the extension system in WFilter, a powerful tool sets for networking issues.
At a first galance
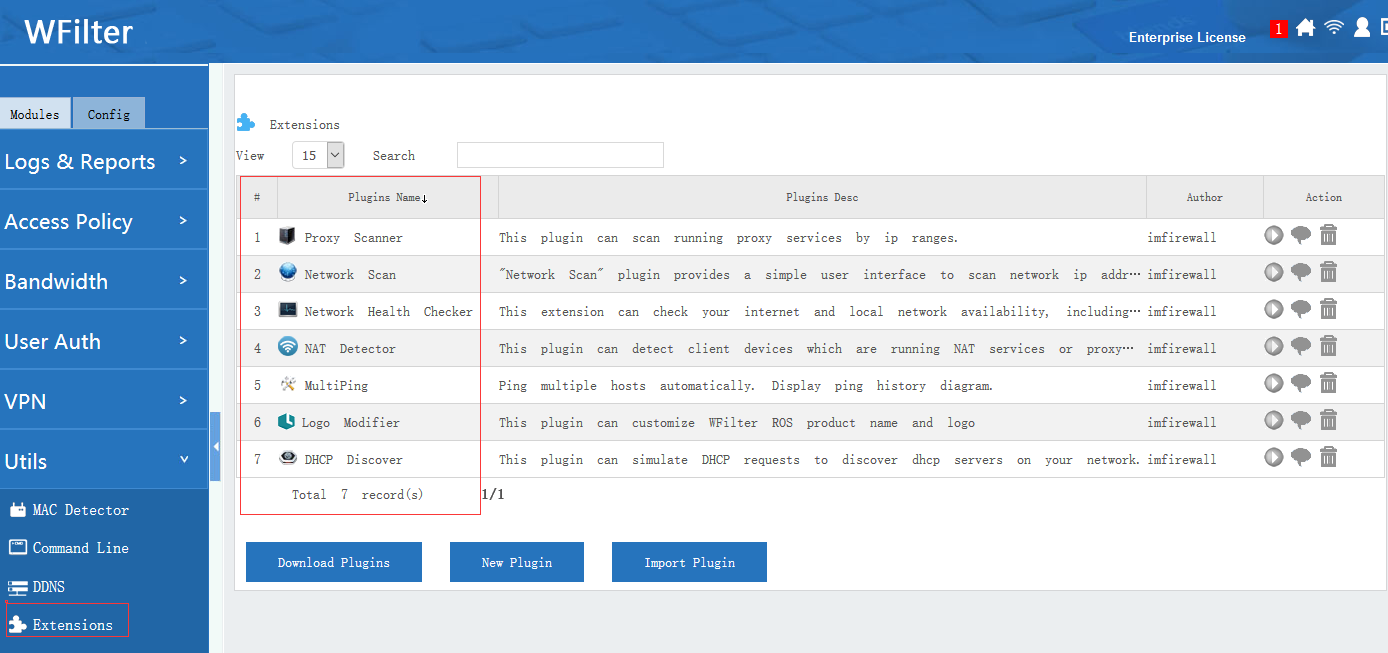
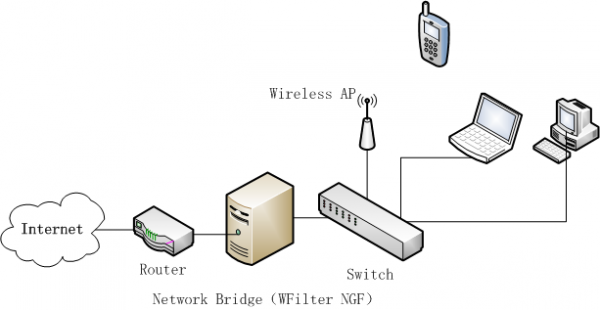
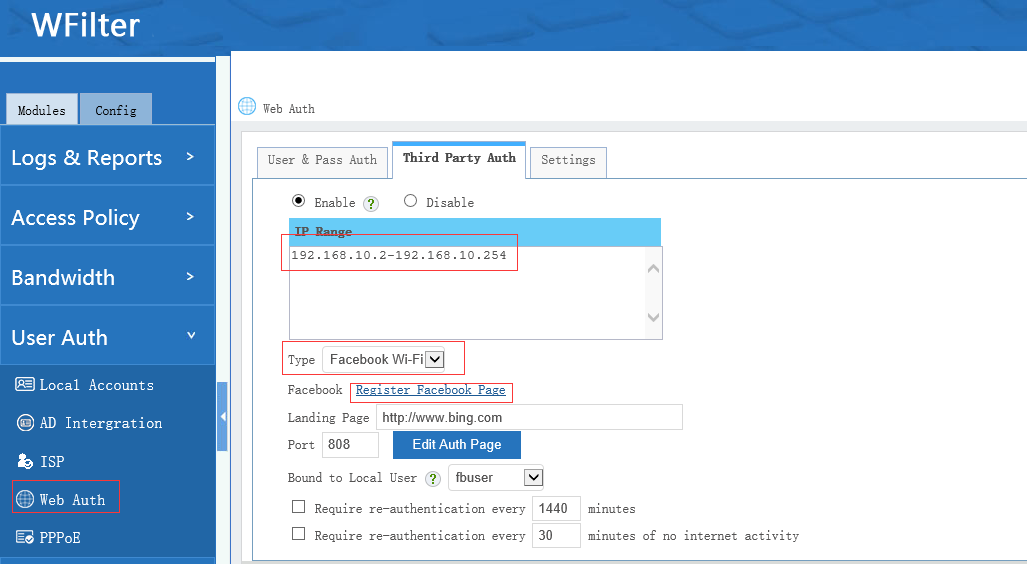
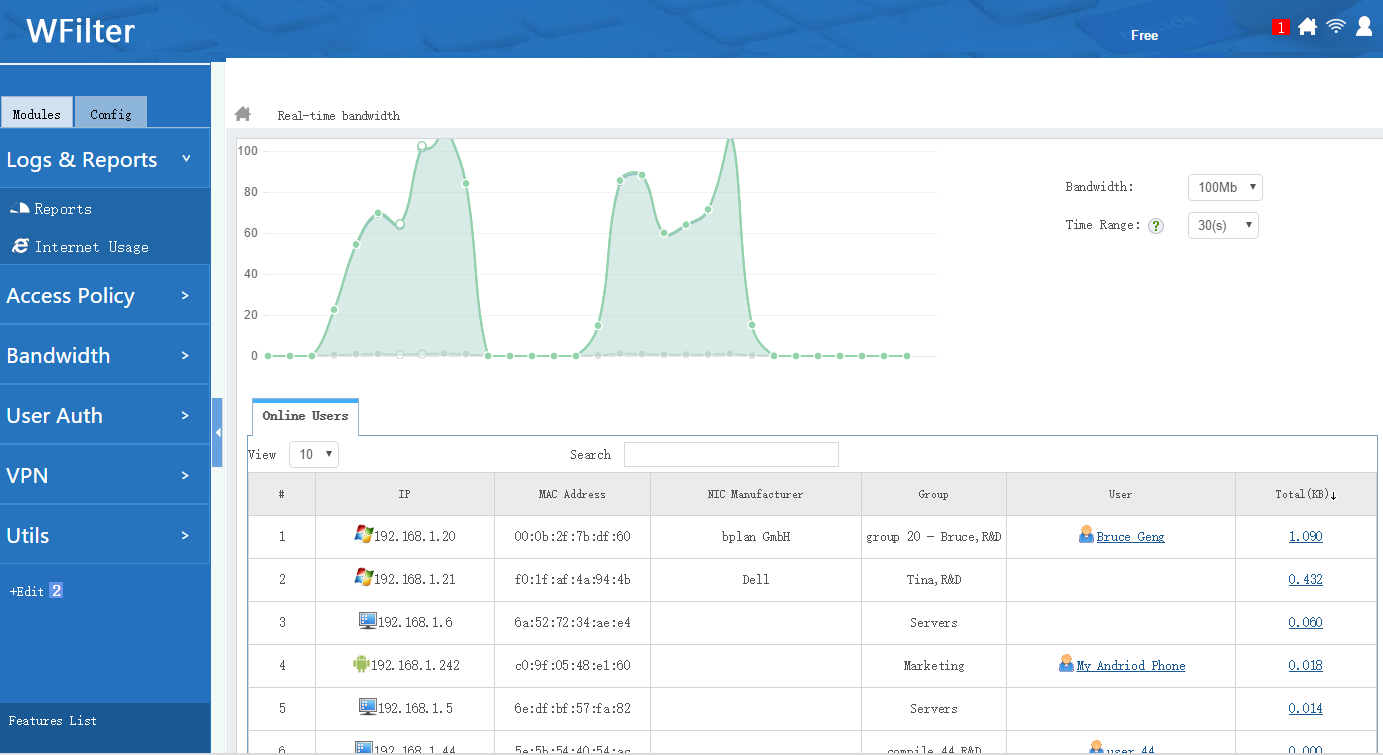
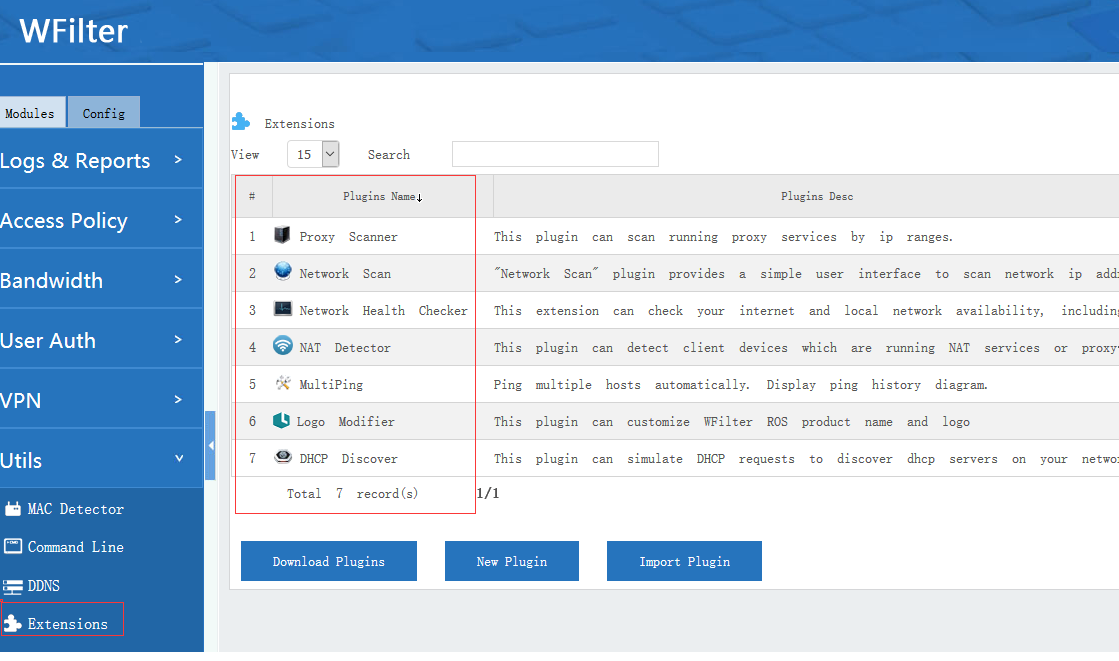
All WFilter systems have an “extension” library, which contains a powerful free tool sets for IT administrators. Most extensions are free. Even supported in WFilter free, a freeware for network internet filtering and monitoring.
Now let’s see what we can do with WFilter extensions:
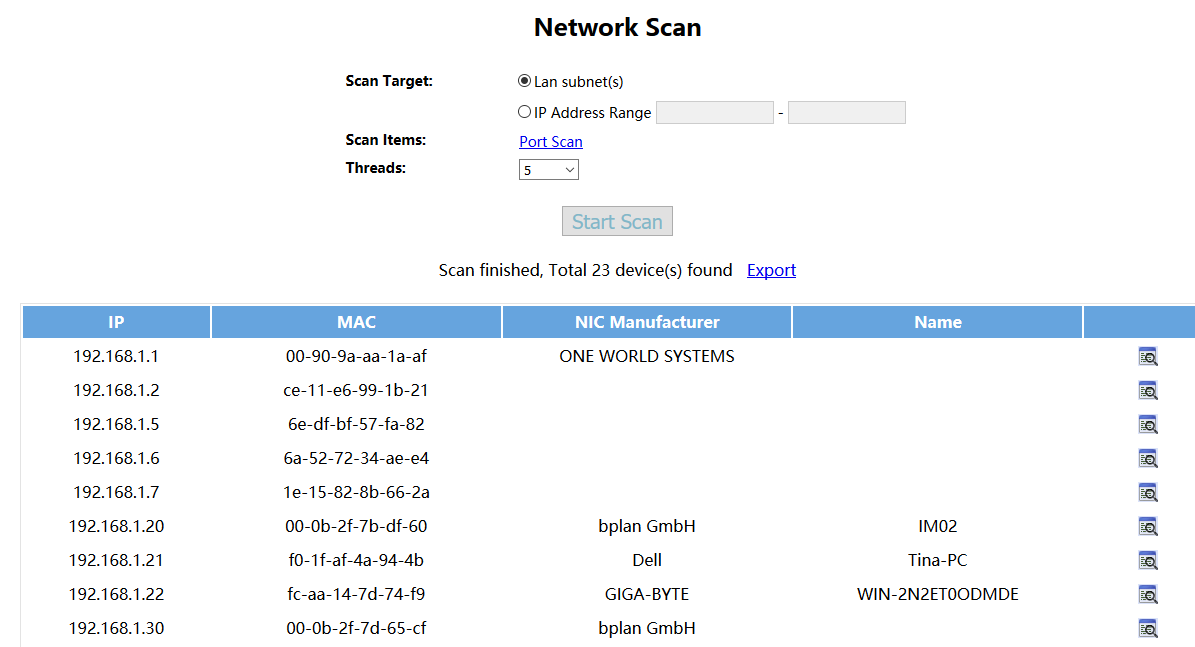
1. Scan client devices in network
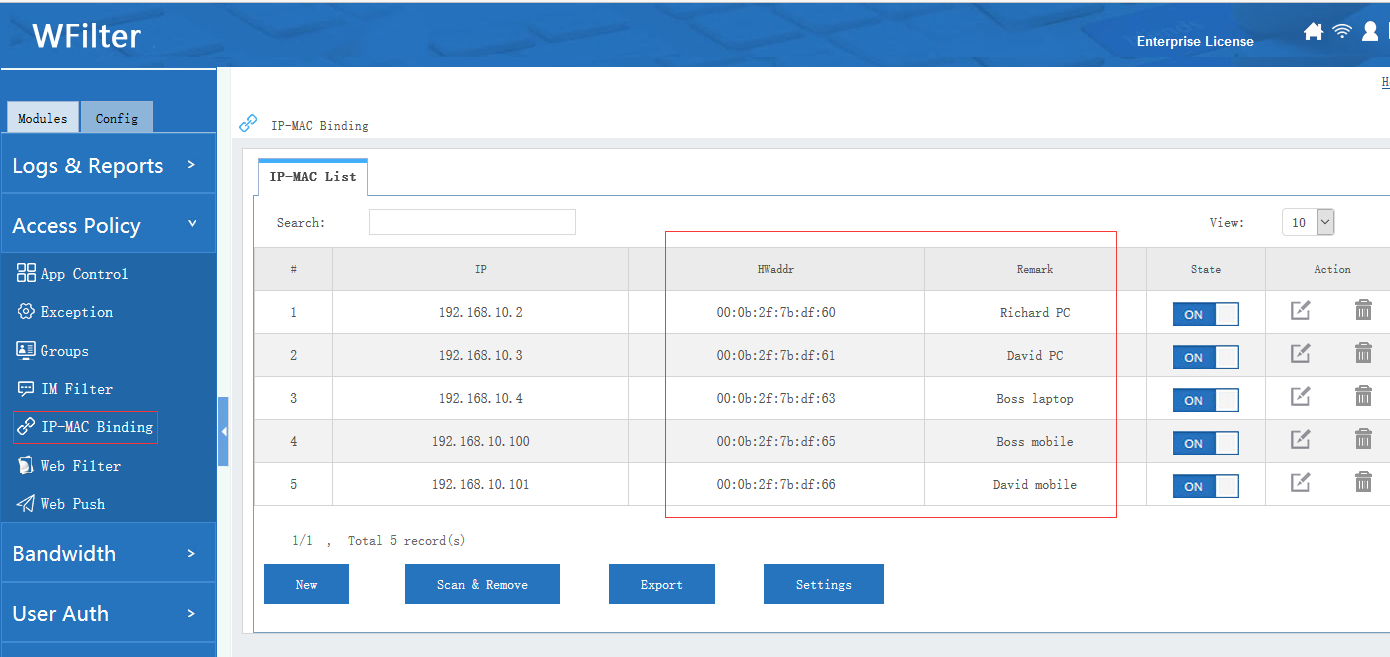
With “network scan” extension, you can get a complete list of network clients, including IP, MAC, manufactor and open ports…
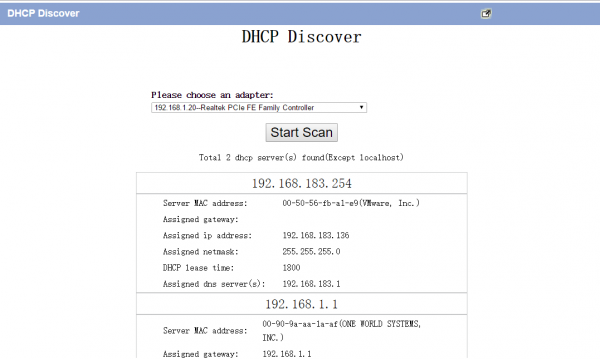
2. Discover and scan DHCP services in network
The “Network DHCP discover plugin” of WFilter can scan DHCP services in your network by a single click. It will list all dhcp servers ip addresses, MAC addresses and MAC manufactures.
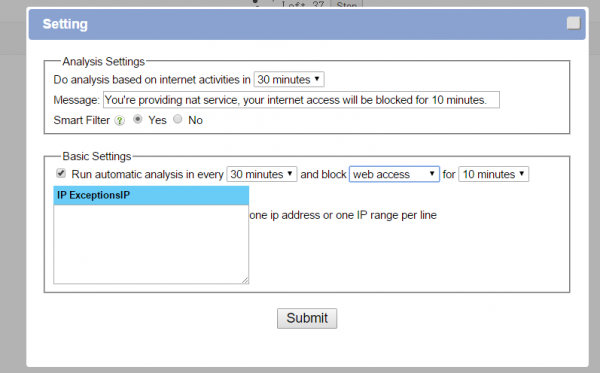
3. Detect NAT sharing services in network
Detect illegal NAT sharing in network.
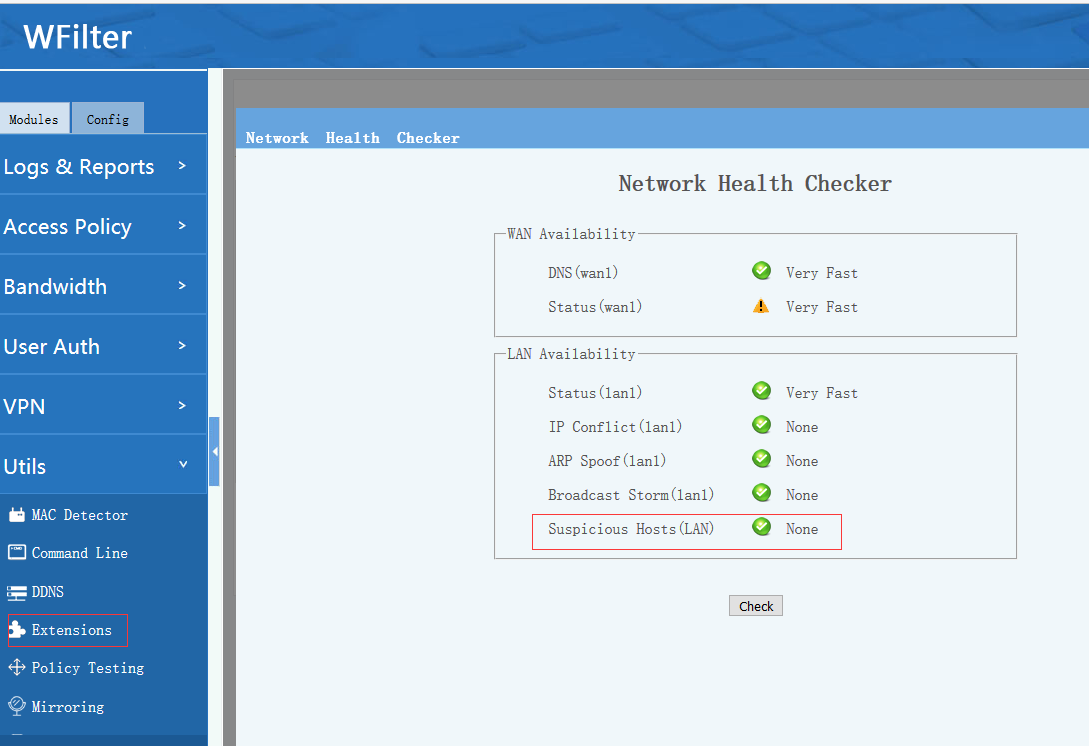
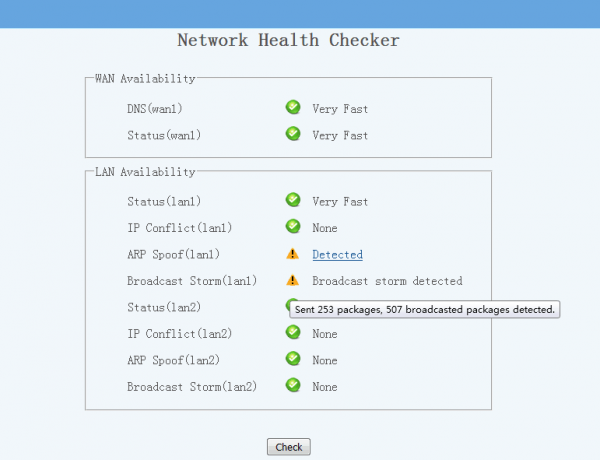
4. Check network health of availability, IP conflict, ARP spoof and broadcast storm
This extension can:
- check availability and ping performance of dns servers.
- check availability and ping performance of internet sites.
- check availability and ping performance of local network hosts.
- check whether there is ip conflict in local network.
- check whether there is arp spoof running in local network.
- check whether there is broadcast storm in local network.
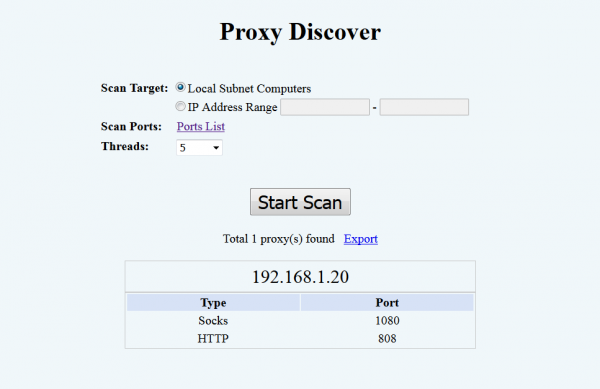
5. Scan proxy servers in network
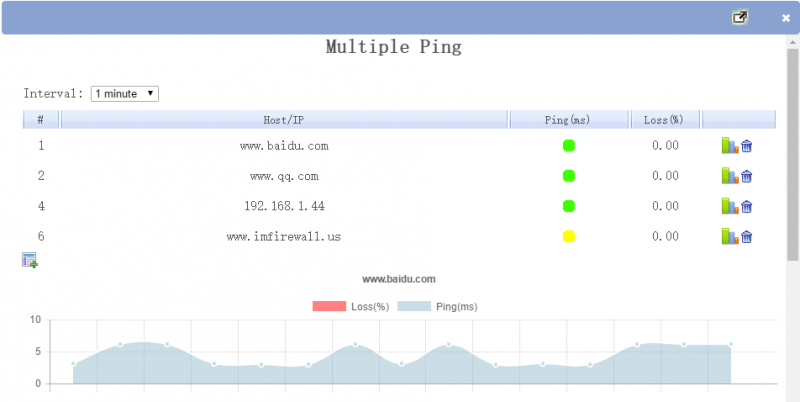
6. Graph ping performance of multiple hosts
With this plugin, you can get ping performance and graph reports for multiple hosts in a period of time.
A complete extesions list can be found at here: WFilter extensions. And more will come. The most important thing is that most extension are free, supported in “WFilter internet content filter(commercial)”, “WFilter NG firewall” and “WFilter Free”.
Isn’t it exicting? Download WFilter Now!