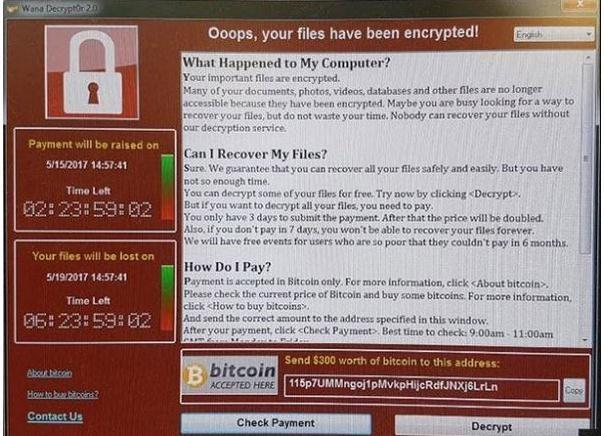
In this weekend, WannaCry swept Europe and Asia quickly, locking up critical systems like the UK’s National Health Service, a large telecom in Spain, several universities in China and other businesses and institutions around the world. Once infected, the infected computer denies access, and demands the equivalent of around $300 in bitcoin for decryption.
In this post, I would introduce the important tips to block WannaCry attack.
1. Install Security Patches. Microsoft has released security patches that fix SMB flaw currently being exploited by the WannaCry ransomware, with most version of Windows supported — including Windows XP, Vista, Windows 8, Server 2003 and 2008.
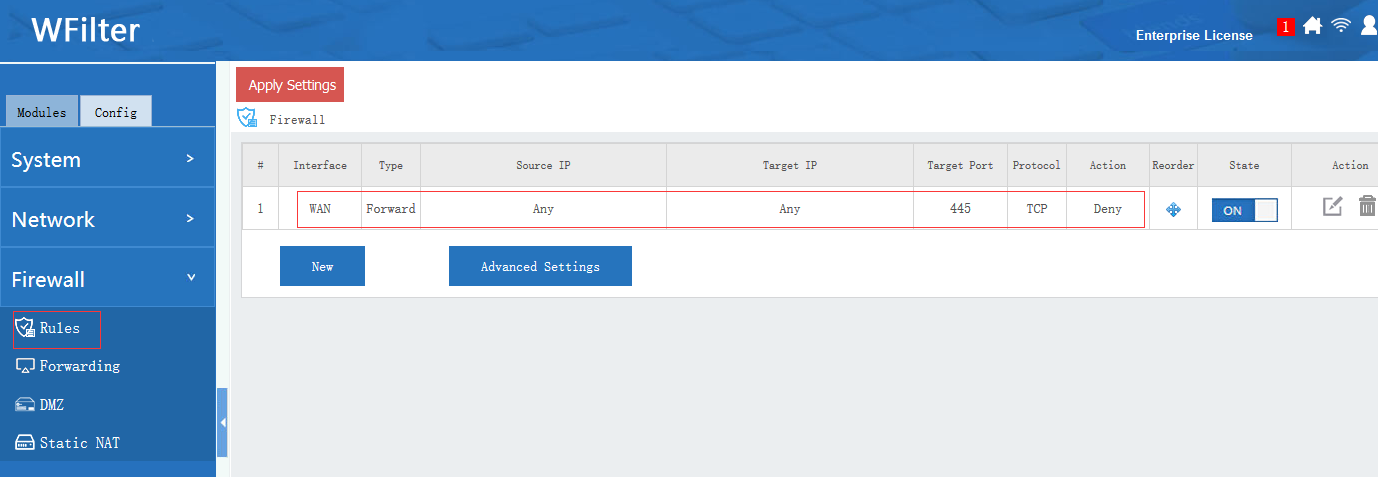
2. Block incoming connections on TCP port 445 in your router/firewall. This rule blocks attacks from internet.
3. For windows DMZ hosts, you also need to block TCP port 445 in firewall settings.
4. To protect VLANs being attacked by an infected VLAN, you can block TCP port 445 in VLAN ACL rules of your core switch.
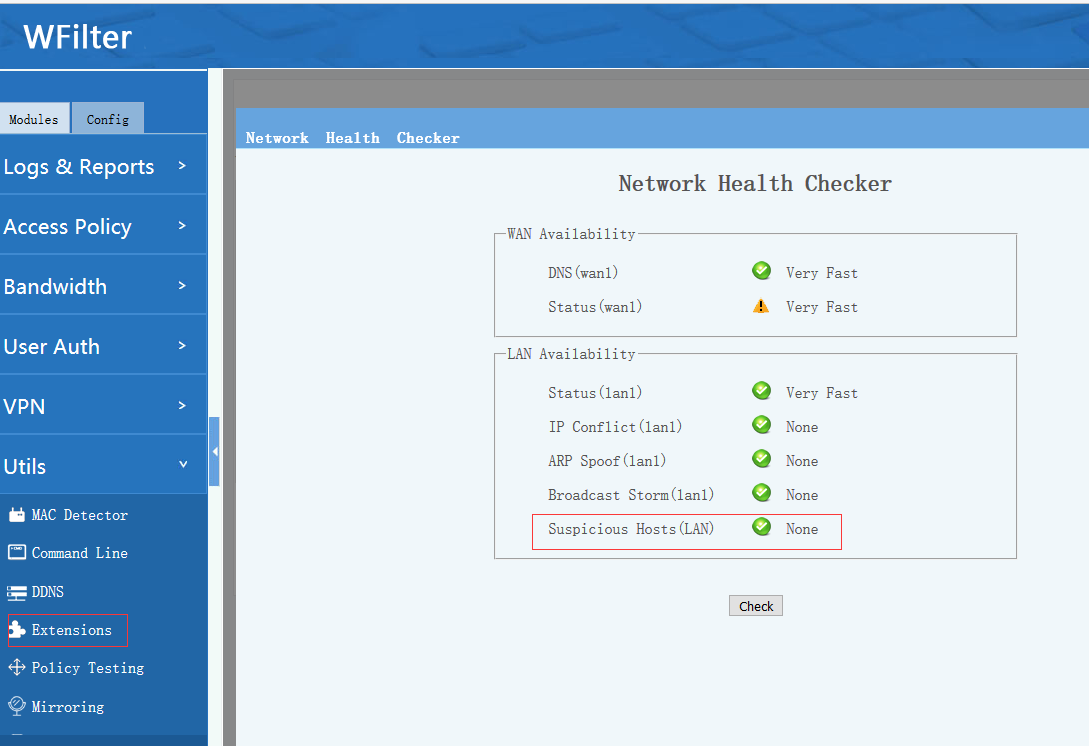
Using the “network health checker” extension of WFilter, you also can check whether there are “Suspicious Hosts ” in your LAN network. Hosts with massive connections will be identified as “Suspicious”.