As a pass-by filtering product, WFilter only can block TCP traffic. For complete blocking of p2p traffic, you’re required to block UDP ports 1024-65534 in your router or firewall. For more information about pass-by filtering, please check: difference between Pass-by filtering and Pass-through filtering.
Since some networks use a windows server with “Routing and Remote Access Service”(RRAS) as the gateway, you also can configure the “IP Filter” in RRAS to block UDP ports. In this tutorial, we will guide you to block all UDP ports except DNS(53) in windows server 2003.
1. Open “Routing and Remote Access” in “Control Panel”->”Administrative Tools”.
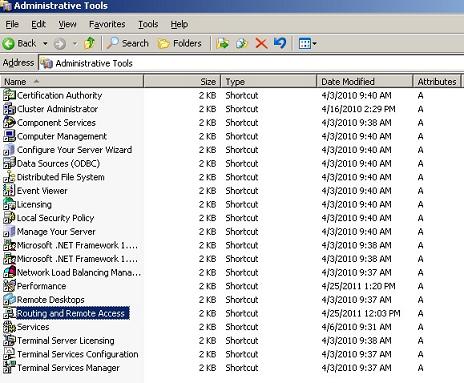
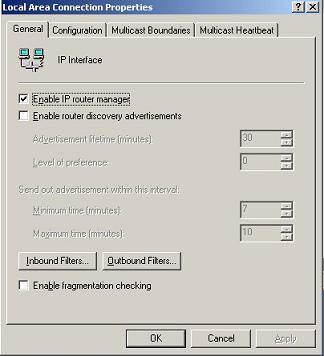
2. Choose the external adapter, Click “General”->”properties”.
3. Click “Inbound Filters”.
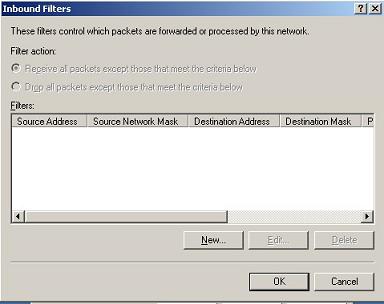
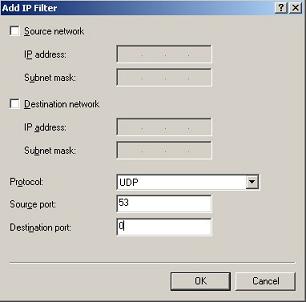
4. Add DNS port UDP 53 into the allow list
Click “New”->”Add IP Filter”, choose “Protocol” as “UDP”, “Sourceport” as “53″, “Destination port” as “0″(means all).
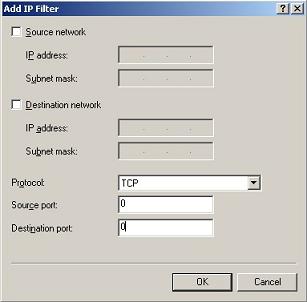
5. Add all TCP into the allow list
Click “New”->”Add IP Filter”, choose “Protocol” as “TCP”, “Sourceport” as “0″, “Destination port” as “0″.
6. Block others
Check “Drop all packets except those that meet the criteria below” to block other traffic.

By now, UDP ports are all blocked except UDP 53(DNS). And WFilter is now full functional to block p2p/IM/iptv traffic.
More information, please check “WFilter Enterprise”.
Other related links:
How to block internet downloading?
How to monitor internet usage on company network?
Internet monitoring software for business
How to filter web surfing?
How to block websites and restrict internet access?
How to block HTTPS websites on my network?