IntroductionWFilter supports various ways to filter web surfing activity:
1. Block Web Surfing CompletelyWhen enabled, all HTTP web surfing will be blocked, except for domains in the “Websites Exception List”. 1.1 Add a new blocking level, as in the below figure: 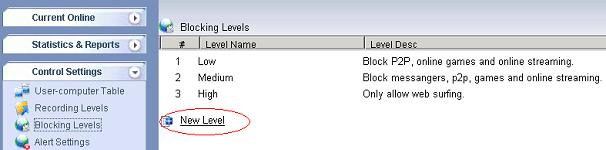
Figure 1 1.2 Set a proper “Level Name” and “Level Desc”, check the “Block Web Surfing”. If you want to display a blocking page when blocked, you need to enable “Display a Deny Page When Blocking”, as in Figure 2: 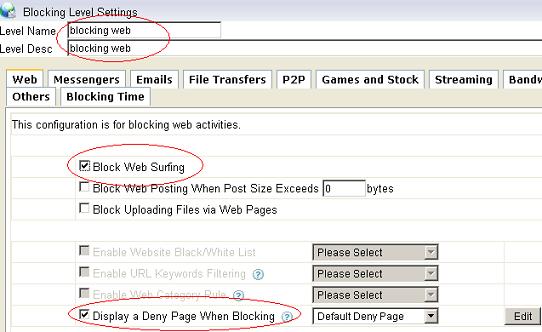
Figure 2 1.3 Apply this new blocking level to certain users in “User-computer Table”, as in the below figure: 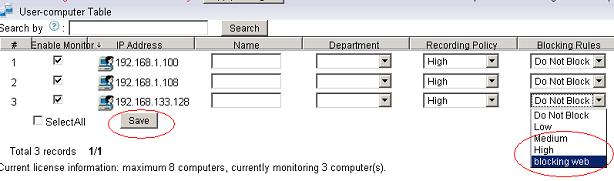
Figure 3 1.4 Websites will be blocked, as in Figure 4: 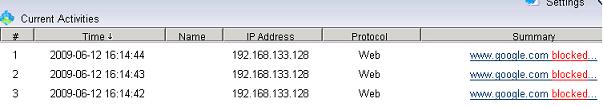
Figure 4 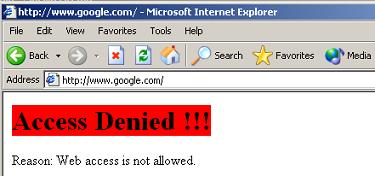
Figure 5 2. Enable Website Black/White ListWebsite black/white list can set black list or white list for websites based on domain name. 2.1 Add a new blocking level, as in the below figure: 
Figure 6 2.2 Set a proper “Level Name” and “Level Desc”, check the “Enable Website black/white list”, as in Figure 7: 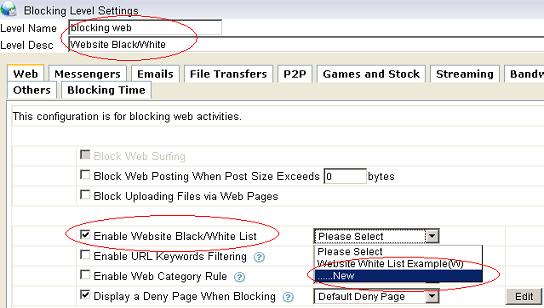
Figure 7 2.3 Add certain websites into a black list, as in Figure 8: 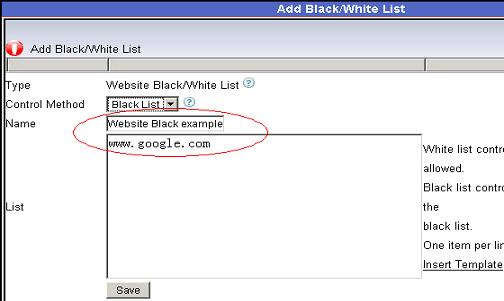
Figure 8 2.4 Apply this new blocking level to certain users in “User-computer Table”, as in the below figure: 
Figure 9 2.5 Websites in the black list will be blocked, as in Figure 10: 
Figure 10 
Figure 11 3.1 Enable URL Keywords FilteringURL keywords filtering can filter webpages by url address. Using this feature, you can block searching for certain keywords in search engines. 3.1 Add a new blocking level, as in the below figure: 
Figure 12 3.2 Set a proper “Level Name” and “Level Desc”, check the “Enable URL Keywords Filtering”, as in Figure 13: 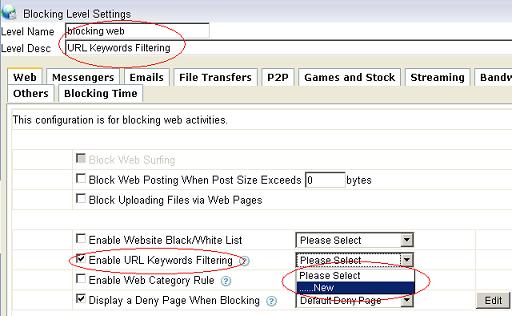
Figure 13 3.3 Check the keywords category to be blocked, as in Figure 14: 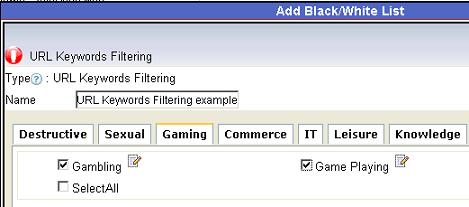
Figure 14 3.4 Apply this new blocking level to certain users in “User-computer Table”, as in the below figure: 
Figure 15 3.5 In this example, searching for “game” will be blocked, as in Figure 16 and Figure 17: 
Figure 16 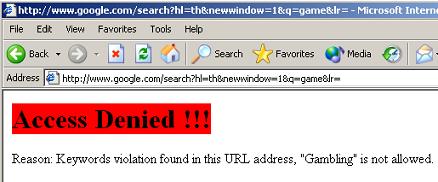
Figure 17 4. Enable Website Category Access PolicyWebsite category access rules can filter websites based on websites categories. Four filtering modes are supported: “Allow”, “Deny”, “Warn” and “Time Quota”. 4.1 Add a new blocking level, as in the below figure: 
Figure 18 4.2 Set a proper “Level Name” and “Level Desc”, check the “Enable web category rule”, as in Figure 19: 
Figure 19 4.3 Set certain filtering mode for certain categories, as in Figure 20: 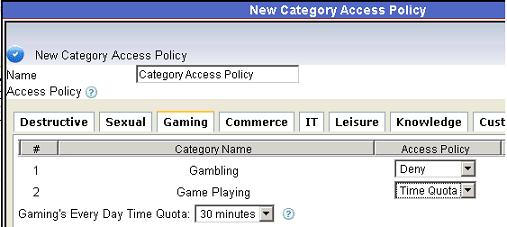
Figure 20 4.4 Apply this new blocking level to certain users in “User-computer Table”, as in the below figure: 
Figure 21 4.6 In this example, time quota is enabled for “Game” websites, as in Figure 22: 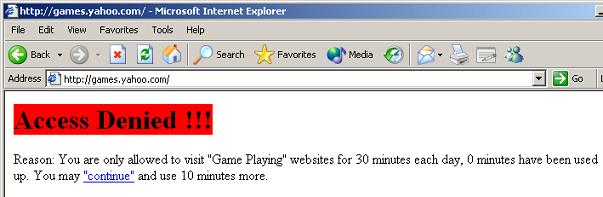
Figure 22 5. Websites Exception ListWebsites in the exception list will not be blocked by other rules. 
Figure 23 6. Enable HTTPS Black/White ListAbove functions can only filter HTTP websites, to block HTTPS websites, you need to enable the “HTTPS Black/White List”. 6.1 Add a new blocking level, as in the below figure: 
Figure 24 6.2 Set a proper “Level Name” and “Level Desc”, check the “Enable HTTPS Black/White List”, as in Figure 25: 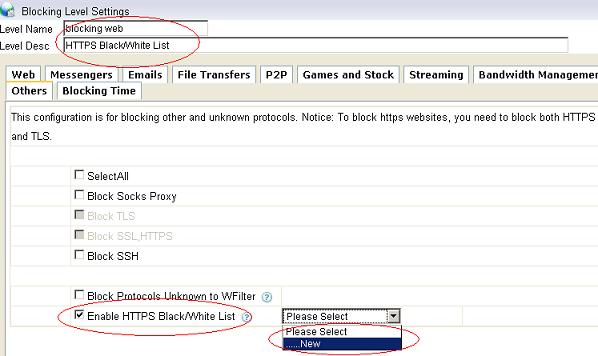
Figure 25 6.3 Add certain websites into a HTTPS Black list, as in Figure 26: 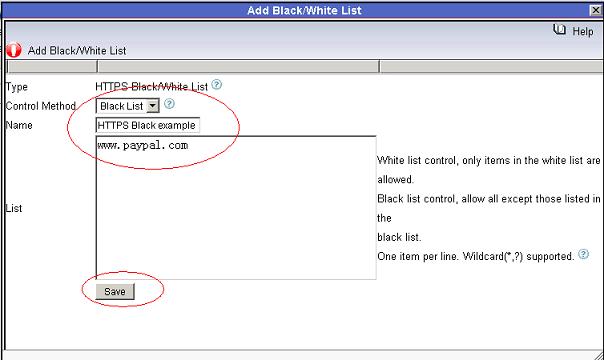
Figure 26 6.4 Apply this new blocking level to certain users in “User-computer Table”, as in the below figure: 
Figure 27 6.5 As in Figure 28 and 29, certain HTTPS websites will be blocked. 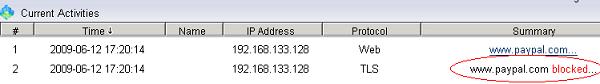
Figure 28 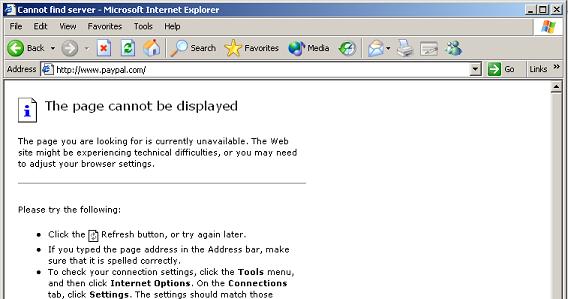
Figure 29 |
Category Archives: Deployment
Monitoring performance of WFilter.
WFilter Monitoring Performance
WFilter is designed to monitor a network with no more than 1000 computers, and the available internet bandwidth of the entire network shall be no more than 100Mbit/s.
Since WFilter is software, the performance depends a lot on the hardware performance. Higher bandwidth requires faster CPU, and more monitored computers require more RAM. Therefore, we recommend you to provide 1M available RAM for each monitored computer.
Below is a performance test result for HTTP request of WFilter 3.3 file-based version:
| # | Computers | Bandwidth | Total HTTP Requests | Recorded Percent | CPU | Memory |
|---|---|---|---|---|---|---|
| 1 | 50 | 37.2M | 16000 | 100% | 35% | 260,298K |
| 2 | 100 | 35M | 20000 | 100% | 38% | 280,576K |
| 3 | 200 | 31M | 40000 | 100% | 58% | 294,561K |
| 4 | 400 | 33M | 80000 | 100% | 68% | 372,786K |
| 5 | 600 | 32.3M | 120000 | 100% | 80% | 540,151K |
| 6 | 1000 | 32.6M | 200000 | 60% | 99% | 540,664K |
As we can see from the above table, when monitored computers number reachs 1000, the “recorded percent” decreased to 60% suddenly. And we noticed the memory only slightly increased, so it shall because lack of memory. Therefore we added the monitoring computer RAM to 2G, and do the test again:
| # | Computers | Bandwidth | Total HTTP Requests | Recorded Percent | CPU | Memory |
|---|---|---|---|---|---|---|
| 7 | 1000 | 32.7M | 200000 | 100% | 90% | 820,640K |
And the test of WFilter 3.3 database version(SQL Server) performance has the similar result:
| # | Computers | Bandwidth | Total HTTP Requests | Recorded Percent | CPU | Memory |
|---|---|---|---|---|---|---|
| 1 | 50 | 34.9M | 10000 | 100% | 45% | 197,392K |
| 2 | 100 | 34.9M | 20000 | 100% | 45% | 210,196K |
| 3 | 200 | 31M | 40000 | 100% | 45% | 270,960K |
| 4 | 400 | 32.9M | 80000 | 100% | 45% | 364,234K |
| 5 | 1000 | 28.6M | 200000 | 58.84% | 100% | 540,664K |
The performance of 1000-user can also be improved by adding RAM of the monitoring computer.
Test Environment
| 1 | Network | 100M ethernet |
| 2 | Test Client | Intel(R) pentium(R) Dual 1.80+1.80GHz , 1G RAM |
| 3 | Test Monitoring Server | Intel(R) Celeron(R) 2.66GHz, 1G RAM |
| 4 | WFilter Version | WFilter 3.3 |
| 5 | Switch | Tplink TL-SF1008 |
WFilter 3.3 will come soon.
WFilter 3.3 is under alpha testing now. The new version will add “Bandwidth limit”, “Url keywords blocking”, “Website visit quota” and other exciting features.
1. “Bandwidth limit”. You can set bandwidth limit for each computer, or blocking certain internet traffic when internet bandwidth is too high. This feature can help you to manage company bandwidth flexibly.
2. “Url Keywords Blocking”, blocking url/webpage by keywords category. You may use this feature to block certain keywords from being searched in search engines.
3. “Website visit quota”, by this feature, you are able to set visit time quota for each website category. For example, “news” websites can be limited to “1 hour” for each day.
WFilter deployment examples.
We’ve added some wfilter deployment examples in pratice.
| # | Title | Description |
|---|---|---|
| Deploy WFilter using Dlink2366 | Using Dlink2366 port mirror switch to deploy WFilter. | |
| Deploy WFilter using Quidway S5012p | Using Huawei QuidwayS5012p to deploy WFilter. | |
| Wireless Network Monitoring Example | Example of wireless network monitoring | |
| Deploy WFilter using cisco 2950 | Example of deploy WFilter using cisco 2950 with ISA Server. |
Wireless network monitoring example
Wireless communication brings fundamental changes to data networking and telecommunications. Now days, more and more organizations and home users build up wireless networks. And in many situations, wired networks and wireless networks exist together. This topic demonstrates a solution to monitor wireless networks internet activities.
A typical network contains both wired and wireless networks:
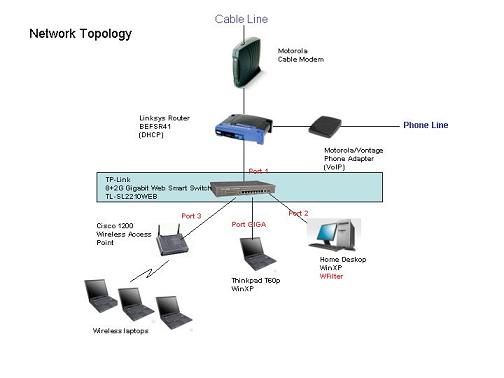
To monitor both the wired network and the wireless network, we add a tplink port mirror switch TL-SL2210WEB here.
Port1 of it is connected to the router, port2 connected to WFilter and port3 connected to the wireless Access Point.
The port mirror configuration is as below:
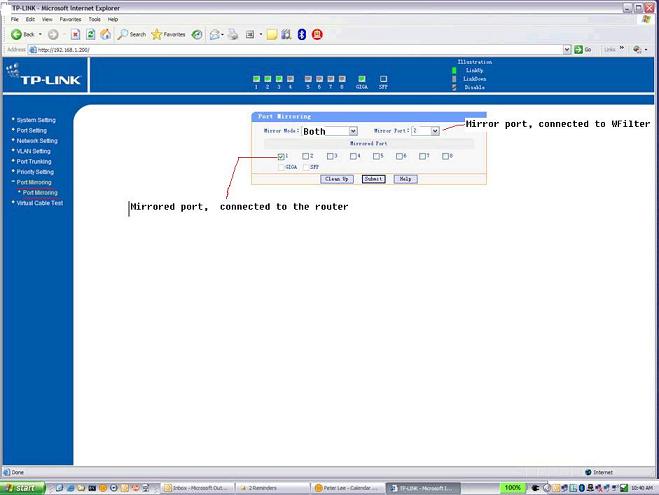
By now, you can monitor all the wireless computers.
WFilter deployment using dlink2366
WFilter Deployment
—-Using Dlink2366
A company use a router connected to internet. A Dlink2366 as the central switch.
The network topology diagram:
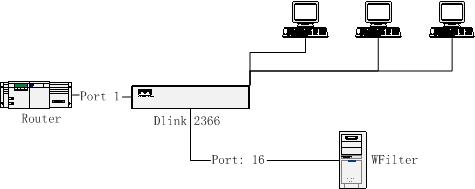
In this issue, we only need to do port mirroring in the Dlink2366 to do monitoring.
Dlink 2366 port mirror configuration:
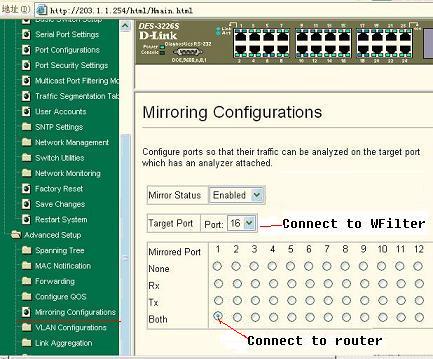
As in the diagram above, port 16 is connected with the router and port 1 is connected to the computer with WFilter installed on.
WFilter related features:
Chat Monitor, Monitor employees, internet monitor, msn chat monitor, aim monitor, yahoo monitor, block p2p, block msn, block aim, block yahoo, block messenger, filter internet.
WFilter deployment using CISCO2950 + ISA2004
WFilter Deployment
—- CISCO2950 + ISA2004
Company A use ISA server 2004 as the proxy server, a cisco 2950 switch as the central switch.
The topology diagram:
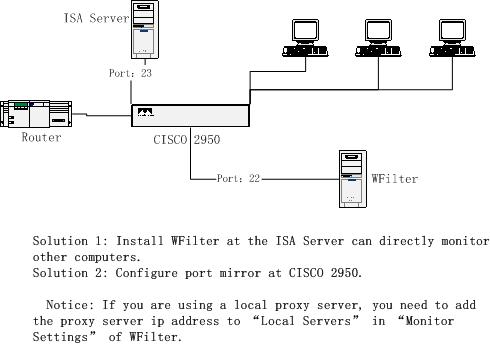
For this kind of topology, we have two solutions:
Solution 1: Install WFilter at the ISA server computer can directly monitor all computers.
Solution 2: Install WFilter at another computer and configure port mirror at cisco 2950.
Notice: By default, WFilter only analysis traffic between local network and the internet. So if you are using a local proxy server, WFilter will not analysis the traffic between the proxy server and the client computers by default. You need to add the proxy server ip address to “Local Servers” in “Monitor Settings” of WFilter to make WFilter work.
How to configure port mirror of CISCO 2950?
As indicated in the above diagram, the ISA server is connected to port 23 of the switch and WFilter is connected to port 22. To make WFilter work, you only need to mirror port 23′s traffic to port 22.
Syntax:
monitor session session_number {destination {interface interface-id [, | -] [encapsulation {dot1q}] [ingress vlan vlan id] | remote vlan vlan-id reflector-port interface-id} | {source {interface interface-id [, | -] [both | rx | tx] | remote vlan vlan-id}}
In this example:
1. Set port 23 as the source mirror port
monitor session 1 source interface Fa0/23
2. Set port 22 as the destination port
monitor session 1 destination interface Fa0/22 ingress vlan 1
Notice: By default, the mirror port of cisco 2950 is recv-only. However, WFilter shall be able to send packages to implement block features. So in this example, we add “ingress vlan 1″ to enable send of port 22.
Some cisco switch do not support ingress syntax, if your switch does not support ingress, you can set a different “blocking adaptor”. Please follow below steps:
1. Set port 23 as the source mirror port.
monitor session 1 source interface Fa0/23
2. Set port 22 as the target mirror port(recv-only)
monitor session 1 destination interface Fa0/22
3. Add a network card in the computer with WFilter install on, connected to a normal port of the switch.
4. Change the “blocking adatpor” to the new added adaptor in “Monitor Settings” of WFilter.
WFilter related features:
Chat Monitor, Monitor employees, internet monitor, msn chat monitor, aim monitor, yahoo monitor, block p2p, block msn, block aim, block yahoo, block messenger, filter internet.