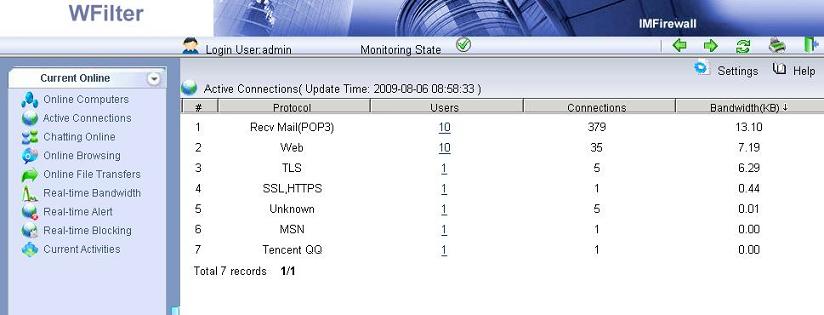
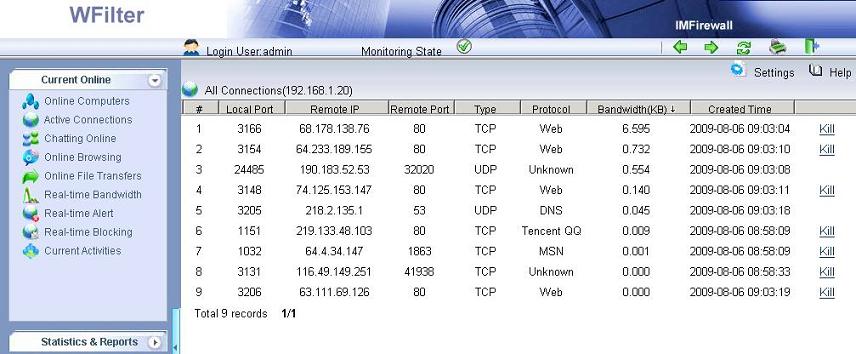
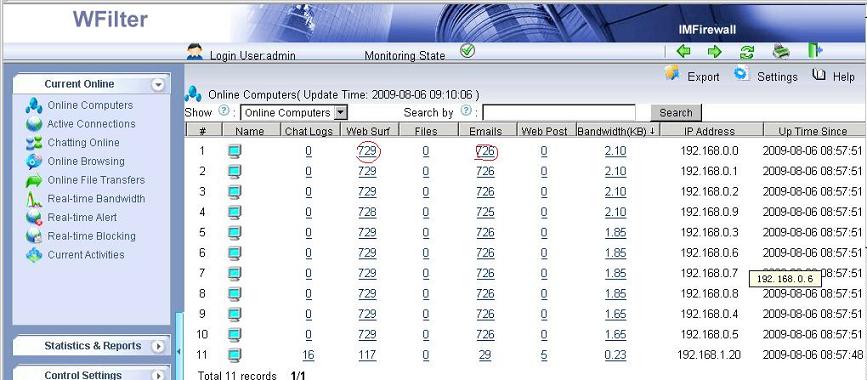
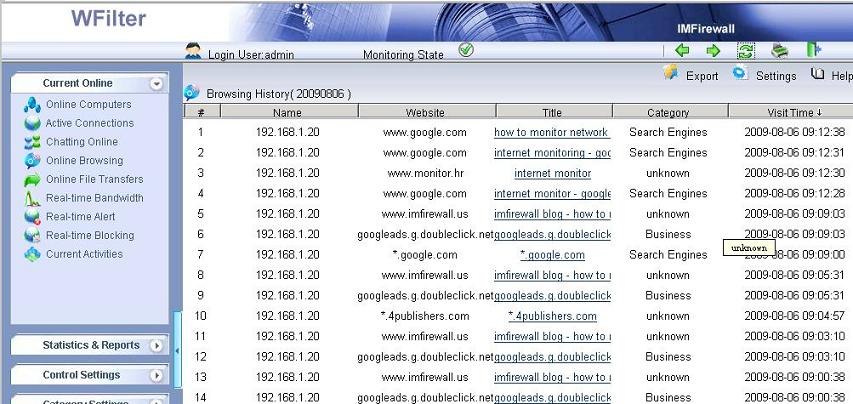
Introduction
WFilter supports various ways to filter web surfing activity:
- Block Web Surfing Completely
- Enable Website Black/White List
- Enable URL Keywords Filtering
- Enable Website Category Access Policy
- Websites Exception List
- Enable HTTPS Black/White List
When enabled, all HTTP web surfing will be blocked, except for domains in the “Websites Exception List”.
1.1 Add a new blocking level, as in the below figure:
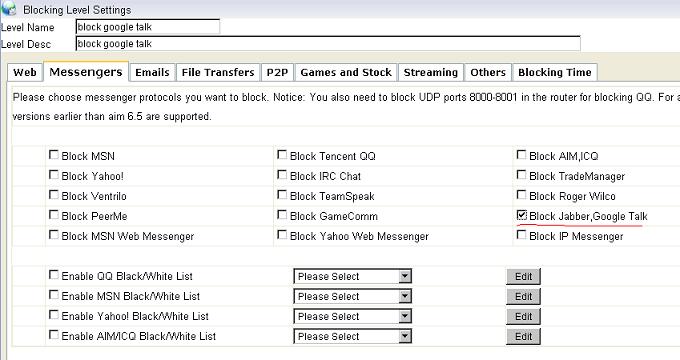
Figure 1 1.2 Set a proper “Level Name” and “Level Desc”, check the “Block Web Surfing”. If you want to display a blocking page when blocked, you need to enable “Display a Deny Page When Blocking”, as in Figure 2:
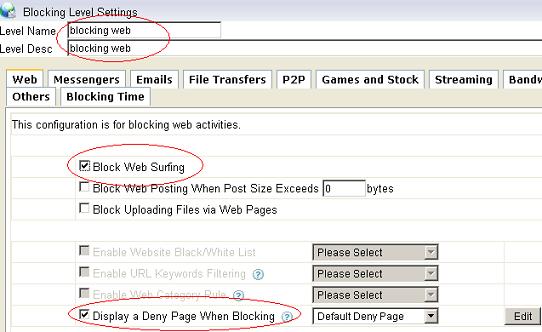
Figure 2 1.3 Apply this new blocking level to certain users in “User-computer Table”, as in the below figure:
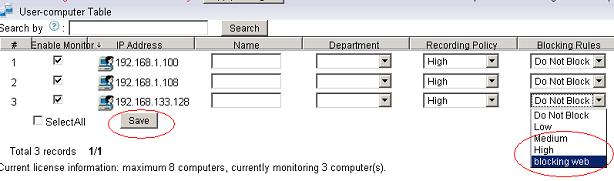
Figure 3 1.4 Websites will be blocked, as in Figure 4:
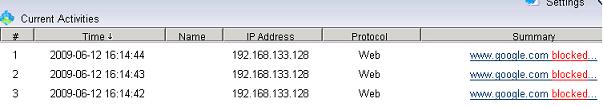
Figure 4 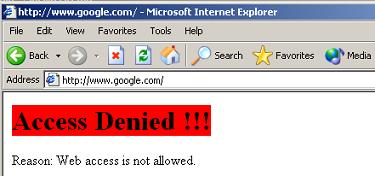
Figure 5 Website black/white list can set black list or white list for websites based on domain name.
When black list is enabled, websites in the black list will be blocked. When white list is enabled, only websites in the white list can be visited.
2.1 Add a new blocking level, as in the below figure:

Figure 6 2.2 Set a proper “Level Name” and “Level Desc”, check the “Enable Website black/white list”, as in Figure 7:
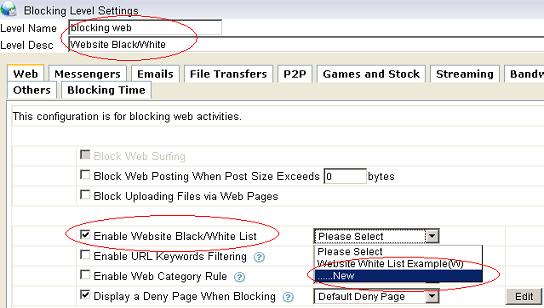
Figure 7 2.3 Add certain websites into a black list, as in Figure 8:
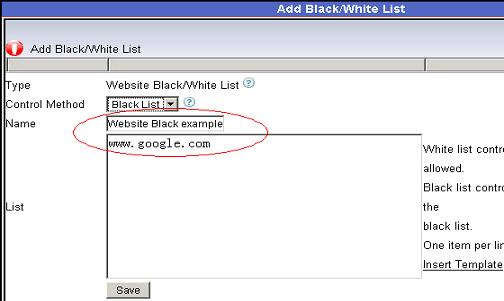
Figure 8 2.4 Apply this new blocking level to certain users in “User-computer Table”, as in the below figure:

Figure 9 2.5 Websites in the black list will be blocked, as in Figure 10:

Figure 10 
Figure 11 URL keywords filtering can filter webpages by url address. Using this feature, you can block searching for certain keywords in search engines.
3.1 Add a new blocking level, as in the below figure:

Figure 12 3.2 Set a proper “Level Name” and “Level Desc”, check the “Enable URL Keywords Filtering”, as in Figure 13:
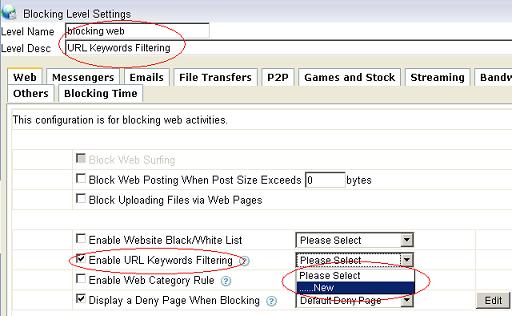
Figure 13 3.3 Check the keywords category to be blocked, as in Figure 14:
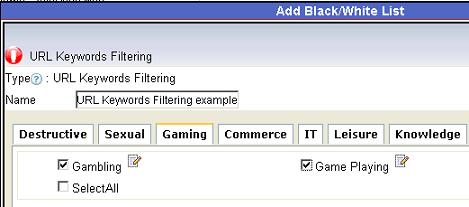
Figure 14 3.4 Apply this new blocking level to certain users in “User-computer Table”, as in the below figure:

Figure 15 3.5 In this example, searching for “game” will be blocked, as in Figure 16 and Figure 17:

Figure 16 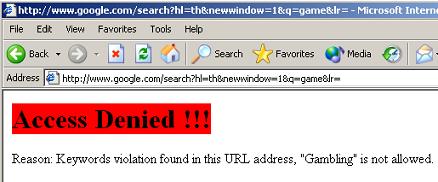
Figure 17 Website category access rules can filter websites based on websites categories. Four filtering modes are supported: “Allow”, “Deny”, “Warn” and “Time Quota”.
4.1 Add a new blocking level, as in the below figure:

Figure 18 4.2 Set a proper “Level Name” and “Level Desc”, check the “Enable web category rule”, as in Figure 19:

Figure 19 4.3 Set certain filtering mode for certain categories, as in Figure 20:
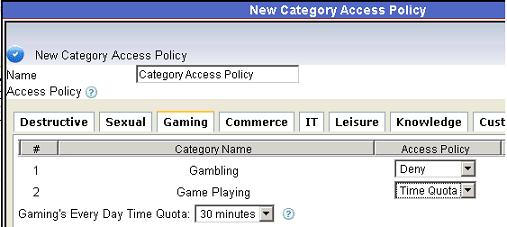
Figure 20 4.4 Apply this new blocking level to certain users in “User-computer Table”, as in the below figure:

Figure 21 4.6 In this example, time quota is enabled for “Game” websites, as in Figure 22:
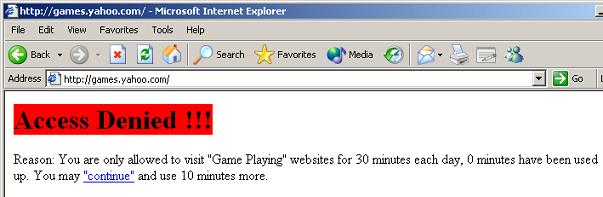
Figure 22 Websites in the exception list will not be blocked by other rules.

Figure 23 Above functions can only filter HTTP websites, to block HTTPS websites, you need to enable the “HTTPS Black/White List”.
6.1 Add a new blocking level, as in the below figure:

Figure 24 6.2 Set a proper “Level Name” and “Level Desc”, check the “Enable HTTPS Black/White List”, as in Figure 25:
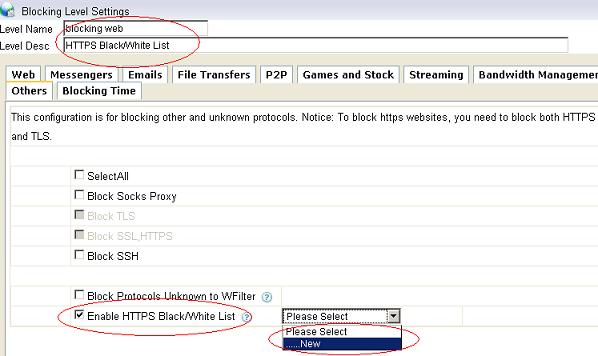
Figure 25 6.3 Add certain websites into a HTTPS Black list, as in Figure 26:
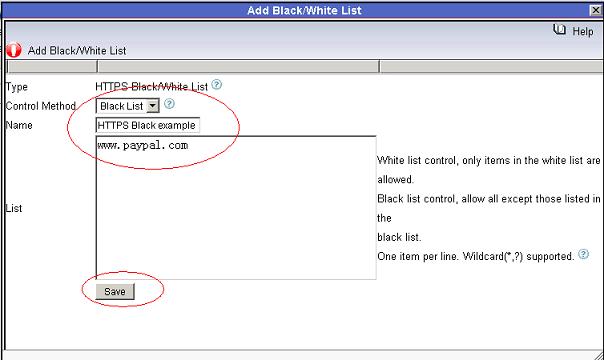
Figure 26 6.4 Apply this new blocking level to certain users in “User-computer Table”, as in the below figure:

Figure 27 6.5 As in Figure 28 and 29, certain HTTPS websites will be blocked.
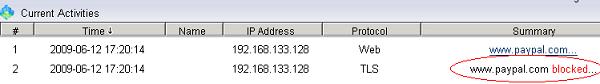
Figure 28 
Figure 29 |