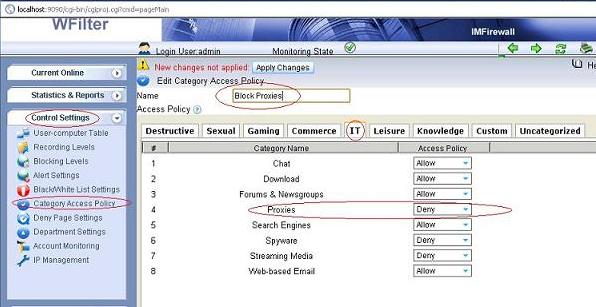
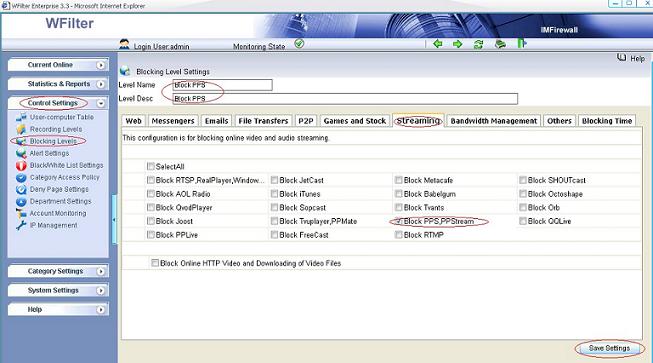
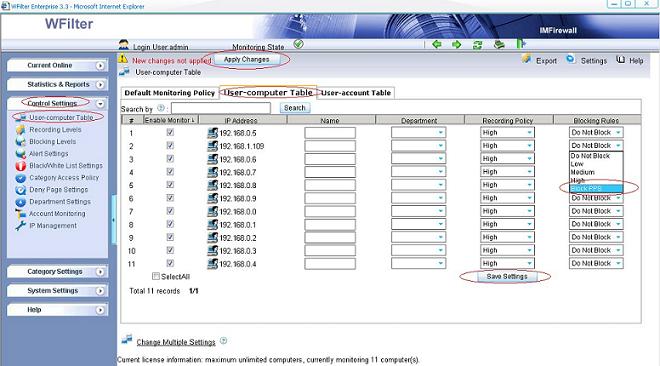
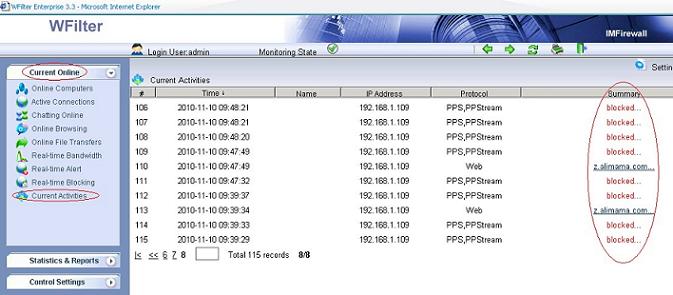
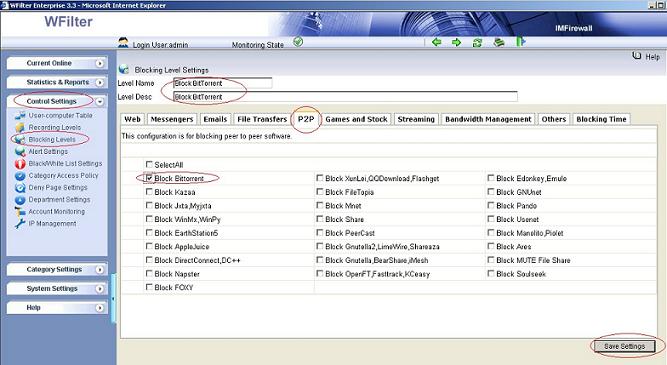
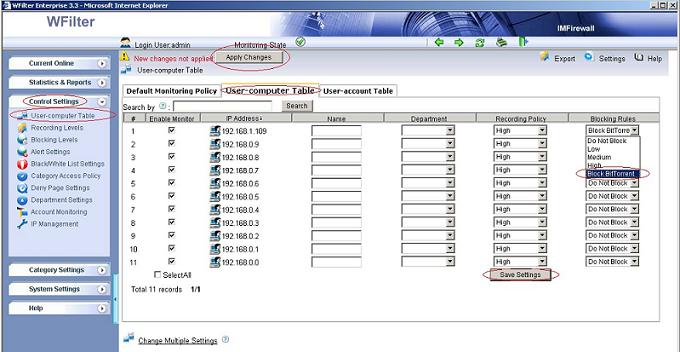
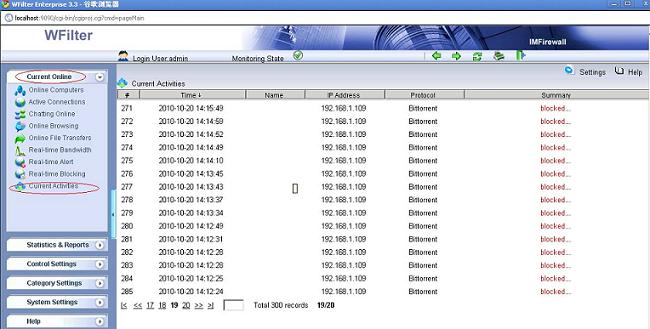
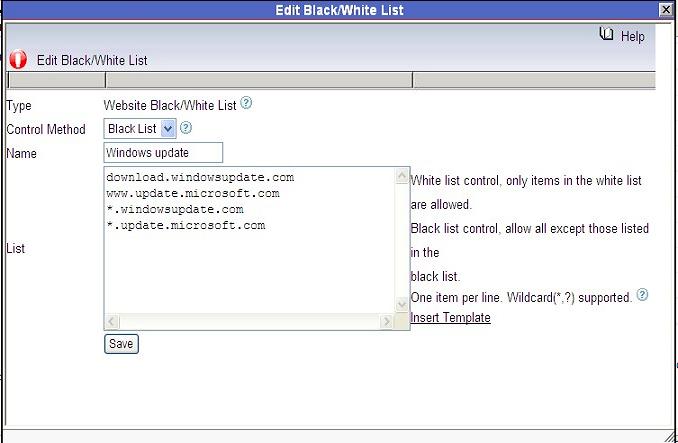
Though WFilter already has many reports by default, there has the chance that you need other report formats or data. In this case, you can directly query the database tables to get what you need.
It’s complicated to customize reports for WFilter file-based version. So you need to install WFilter database version first. For steps to install WFilter database version, please check: WFilter Database Version Installation Guide
There has a “web surfing time report” in “Detailed Reports”->”Web Report”, you can generate this report “by name” or “by website” in WFilter user interface. Now if you need to get a report of web surfing time both “by name” and “by website”, you need to customize a sql query. The data is stored in table “webreport” with below structure:
create table webreport
(
| mac |
char(12) NOT NULL |
/* MAC address */ |
| ip |
varchar(20) |
/* ip address */ |
| acct |
varchar(200) |
/* domain username */ |
| happendate |
varchar(10) |
/* date */ |
| method |
char(1) |
/* 0 – get, 1 – post */ |
| categoryid |
varchar(10) |
/* website category id */ |
| host |
varchar(100) |
/* website domain name*/ |
| visitcnt |
varchar(20) |
/* visits number */ |
| duration |
varchar(20) |
/* surfing time in seconds*/ |
)
1. Web surfing time report by ip address
To get a report by ip address and websites for a certain date, you can execute a sql like:
select ip, host, sum(convert(int, duration)) cnt from webreport where happendate>=’20120803′ and happendate<’20120804′ and ip is not null group by ip, host order by ip, cnt desc
You will get such kind of data:
| 192.168.1.131 |
www.google.com |
226 |
| 192.168.1.131 |
forum.imfirewall.us |
192 |
| 192.168.1.131 |
ct1.addthis.com |
180 |
| 192.168.1.131 |
l.yimg.com |
180 |
| 192.168.1.131 |
sports.yahoo.com |
153 |
| 192.168.1.20 |
m614.mail.qq.com |
266 |
| 192.168.1.20 |
share.baidu.com |
254 |
| 192.168.1.20 |
forum.imfirewall.us |
200 |
| 192.168.1.20 |
hm.l.qq.com |
180 |
| 192.168.1.20 |
info.iet.unipi.it |
180 |
2. Web surfing time report by user
If you have “Account Monioring” enabled, you also can generate reports based on AD usernames. The sql will be:
select acct, host, sum(convert(int, duration)) cnt from webreport where happendate>=’20120803′ and happendate<’20120804′ and acct is not null group by acct, host order by acct, cnt desc
You will get such kind of data:
| CN=Users%2cDC=demo%2cDC=com%2fBruce_Geng |
www.google.com |
226 |
| CN=Users%2cDC=demo%2cDC=com%2fBruce_Geng |
forum.imfirewall.us |
192 |
| CN=Users%2cDC=demo%2cDC=com%2fBruce_Geng |
l.yimg.com |
180 |
| CN=Users%2cDC=demo%2cDC=com%2fBruce_Geng |
ct1.addthis.com |
180 |
| CN=Users%2cDC=demo%2cDC=com%2fBruce_Geng |
sports.yahoo.com |
153 |
| CN=Users%2cDC=demo%2cDC=com%2fBruce_Geng |
test.org.uk |
96 |
| CN=Users%2cDC=demo%2cDC=com%2fBruce_Geng |
www.yahoo.com |
72 |
| CN=Users%2cDC=demo%2cDC=com%2fBruce_Geng |
*.bc.yahoo.com |
67 |
| CN=Users%2cDC=demo%2cDC=com%2fBruce_Geng |
*.websense.com |
59 |
| CN=Users%2cDC=demo%2cDC=com%2fBruce_Geng |
*.g.doubleclick.net |
34 |
| CN=Users%2cDC=demo%2cDC=com%2fBruce_Geng |
www.google.com.hk |
31 |
Please notice, the “acct” column is urlencoded. You need to urldecode it to get a readable username.
Online urldecode.