It’s very simple to update your WFilter to the last version. This tutorial will guide you to update your WFilter manually.
Please follow below steps:
1. Download the last version from our website.
How to block sending emails with attachment on company network?
WFilter can be used to block sending/receiving emails, block sending attachments and filter email accounts. And you only need to install WFilter in one computer to monitor all computers in your network.
This tutorial will guide you to block outgoing emails with attachments.
1. Block outgoing emails with attachment(s)
This feature can block sending of emails with attachments via SMTP protocol.
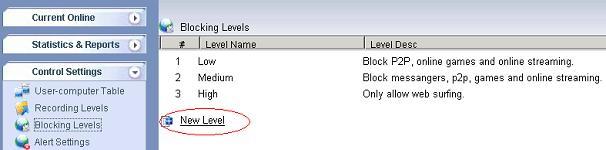
1.1 Add a new blocking level, as in the below figure:

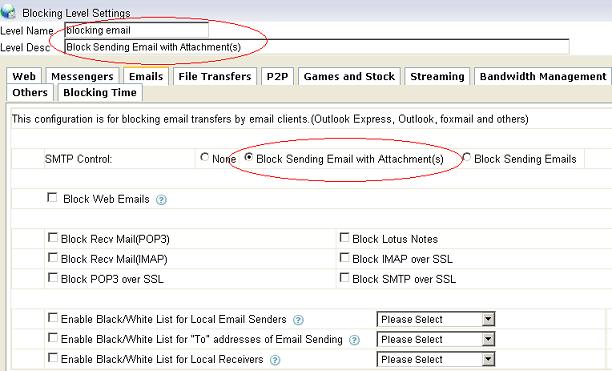
1.2 Set a proper “Level Name” and “Level Desc”, check “Block sending emails with attachment(s)”, as in Figure 2:
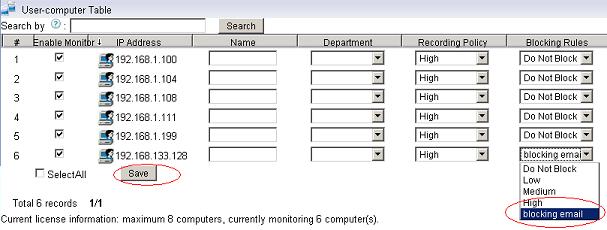
1.3 Apply this new blocking level to certain users in “User-computer Table”, as in the below figure:
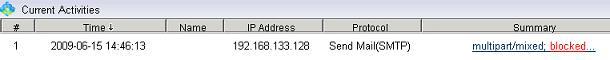
1.4 Emails with attachment(s) will be blocked, as in Figure 4:
Blocking adapter doesn’t work when using two network cards with WFilter.
Some switches does not allow outgoing traffic on a mirroring port. In this case, WFilter needs a separate blocking adapter to send blocking packets. And if you’re monitoring and filtering more than 100 computers, we recommend you to use a different blocking adapter as the monitoring adapter.
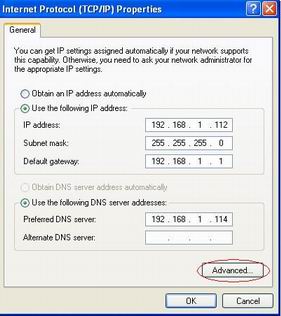
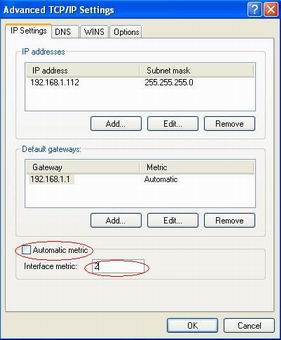
When the two network cards are installed, we will want the Windows system to use the blocking adapter to access your network. However, sometime the Windows system might pick up the monitoring adapter and fails to connect to your network. This problem can be resolved by the “Automatic Metric” setting in Windows.
A metric is a value that is assigned to an IP route for a particular
network interface that identifies the cost that is associated with
using that route. The Automatic Metric feature is configured independently for each network interface in the network. This feature is useful in situations where you have more than one
network interface of the same speed, for example, when each network
interface has been assigned a default gateway. In this situation, you
may want to manually configure the metric on one network interface, and
enable the Automatic Metric feature to configure the metric of the
other network interface. This setup can enable you to control the
network interface that is used first in the routing of IP traffic.
In our case, the “Automatic Metric” of the blocking adapter shall be smaller than the monitoring adapter. So by setting “Automatic Metric” of the blocking adapter to “1″, and the monitoring adapter to “2″, Windows system will use the blocking adapter to access your network.
Use dumpPacket.exe of WFilter to generate a packet dump file.
Sometimes, on an indeterminate problem of using WFilter, we might need a packet dump file for diagnosis. WFilter has a packet dump tool named “dumpPacket.exe”, which will dump packets on the monitoring adapter.
This tutorial will guide you to generate a packet dump file using “dumpPacket.exe”.
First, lauch “dumpPacket.exe” from “Start”->”IMFirewall WFilter”->”Tools”. If you didn’t install WFilter shortcuts, you can find this tool in WFilter directory.
It will ask you to enter a testing ip address. For example, if
you need to check a monitoring problem for ip “192.168.1.20″, you can
input “192.168.1.20″ here. If you just want to capture some packet
samples, you may just press “enter” here! Press “enter” means dumping
packets for all computers.
Close the dumping window. If you’re doing a certain test, you need to wait until the test is done. For example, sending an email message. If you’re dumping packets for all computers, you only need to wait for 3-5 seconds because the dump file can be very large. If the dumping file is too large, you can do the test again in a shorter time.
The dump.cap file can be found in “temp” directory of WFilter. The dump.cap file is pcap format, which can be opened by wireshark and other pcap applications.
How to check whether port mirroring settings are correct?
To make WFilter work, you need to setup port mirroring in your switch. However, sometimes you might still cannot monitor other computers even port mirroring is configured. It has several possibilities:
1. WFilter computer shall be connected directly to the mirroring port.
2. Configured ports does not match real ports.
3. Both outbound and inbound traffic is required by WFilter. If you only mirror one direction packets, WFilter can not work properly.
4. Incorrect WFilter settings. (wrong ip segment or monitoring adapter…)
5. Firewall/anti-virus programs blocks non-local packets. For example, nod32 will block non-local packets, so even port mirroring settings are correct, the mirrored traffic still can not reach WFilter. We recommend you to shutdown your firewall and anti-virus programs for checking.
To locate the problem, first we need to confirm whether packets are mirrored to WFilter computer. It can be checked in a simple way following below steps:
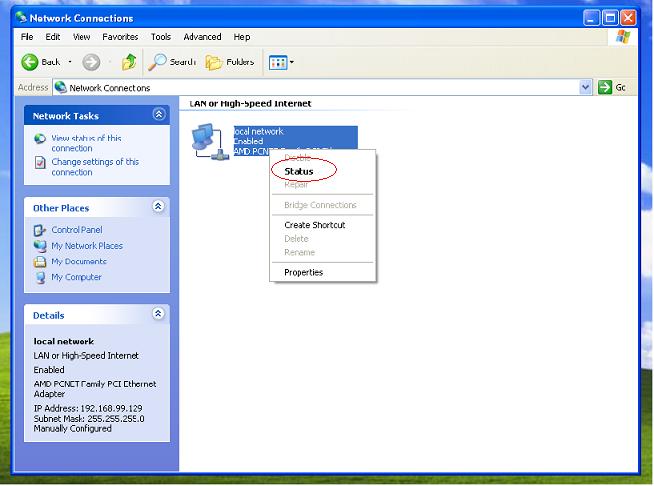
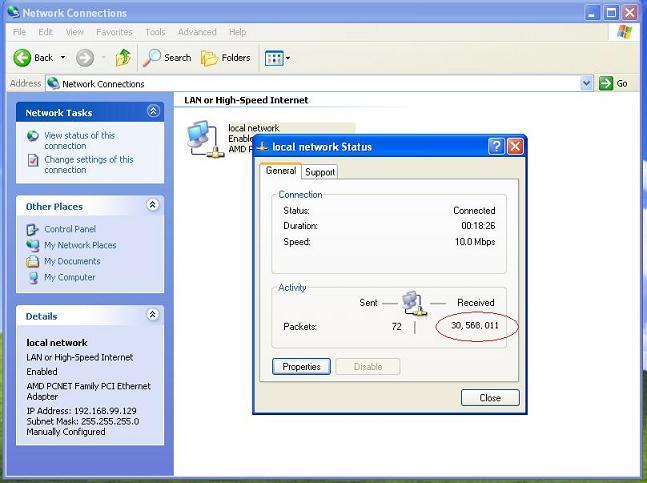
Upon successful mirroring, the “Received” packets number shall be much larger than the “Sent” packets. If not, you need to check certain mirroring settings or cable connections.
How to block limewire downloading on company network?
LimeWire is a free peer-to-peer file sharing (P2P) client for Windows, Mac OS X, Linux, and other operating systems supported by the Java software platform. It uses the Gnutella network and also the BitTorrent protocol.
Using Limewire, users can easily download copies of copyrighted materials and illegal or objectionable content. In LimeWire versions prior to 5.0, users could accidentally configure the software to allow access to any file on their computer, including documents with personal information. Though recent versions of LimeWire do not allow unintentional sharing of documents or applications, it still opens a share directory to share downloaded files by default.
Therefore, to save your bandwidth and keep your network safe, you might want to block limewire program on your network.
However, though the default TCP port of Gnutella2 is 6346. You can not block limewire only by blocking this port in your router or firewall, because Limewire allow users to change its default port.
This tutorial will guide you to block limewire downloading using WFilter. WFilter blocks Limewire traffic based on signature matching despite which port it is using. Limewire can be blocked only by a single click.
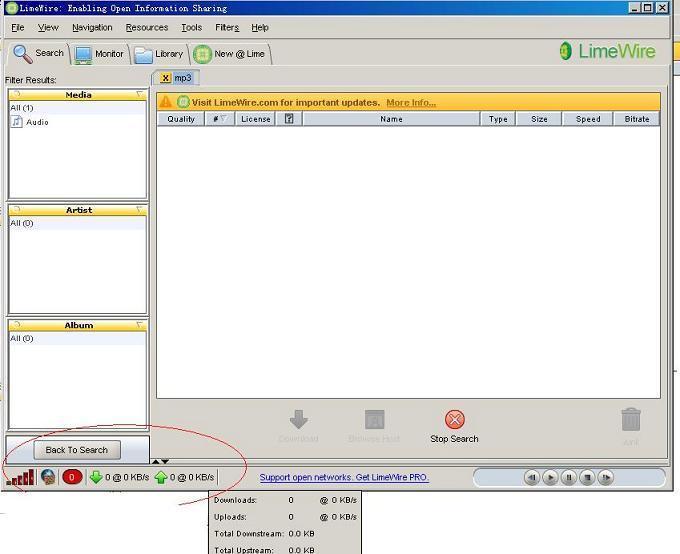
Blocked limewire:
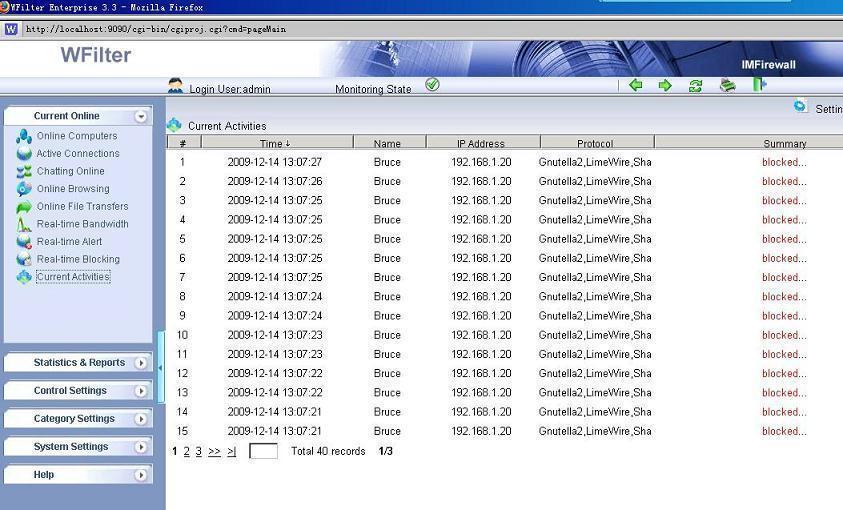
Blocking logs of limewire in WFilter:
WFilter homepage: http://www.wfiltericf.com/WFilter.htm
How to control internet bandwidth usage on network?
Traffic Shaping and Prioritization is becoming more and more common in the corporate market. Most companies with remote offices are now connected via a WAN (Wide Area Network). Applications tend to become centrally hosted at the head office and remote offices are expected to pull data from central databases and server farms. As applications become more hungry in terms of bandwidth and prices of dedicated circuits being relatively high in most areas of the world, instead of increasing the size of their WAN circuits, companies feel the need to properly manage their circuits to make sure business-oriented traffic gets priority over best-effort traffic. Traffic shaping is thus a good means for companies to avoid purchasing additional bandwidth while properly managing these resources.
With a linux gateway, you have a very rich set of tools for managing and manipulating the transmission of packets. More details can be found at: http://linux-ip.net/articles/Traffic-Control-HOWTO/index.html, However, sometimes it might be difficult for you to deploy a linux gateway server.
This tutorial will guide to implement a passby bandwidth management solution, which enables you to manage internet bandwidth through a mirroring port on your switch. Port mirroring allows you to setup a port in the switch to receive packets of other ports. Setting up a mirror port does no change to your network topology, and it will not affect your network speed.
Let’s take WFilter as an example:
First, setup a mirroring port.
When the port mirroring is properly setup, WFilter will be able to monitor all computers internet activities. 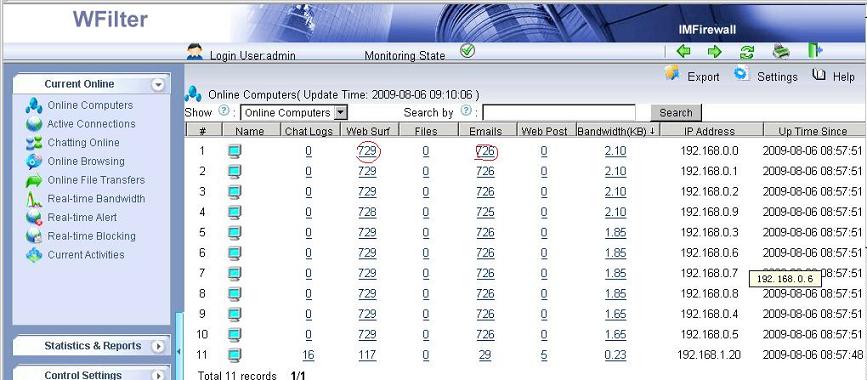
Bandwidth Management Settings
Using WFilter’s bandwidth management feature, you can set a maximum accumulating bandwidth of each computer for a period time. In this example, each user can have 200M internet bandwidth every day. Only messengers and emails are allowed when the bandwidth limit is reached.
You also can setup a policy to block certain users when available
internet bandwidth of the entire network is not enough. For example,
When entire network traffic exceeds 80% of available internet
bandwidth, p2p traffic will be blocked.
Bandwidth Alert Settings
And the bandwidth alert feature will send you an alert email when the accumulating bandwidth of a computer is too large.
More information, please check “WFilter Enterprise”.
Other related links:
How to block websites at work during working hours?
How to block video streaming on company network?
How to block internet downloading?
How to monitor internet bandwidth?
How to monitor internet usage on company network?
How to block instant messaging on company network?
How to filter websites and restrict website access?
How to setup ip-mac binding in WFilter?
You may assign static ip addresses to computers manually or in your DHCP server. However, it is difficult to prevent users from changing their ip addresses or mac addresses. Though it is more reasonable to setup ip-mac binding in routers or switches, software solution is also a good option, as it is easier to setup and manage.
This tutorial will guide you to bind ip addresses to mac addresses in WFilter, an internet filtering and monitoring software product.
First, you need to setup a mirror port in your switch to do monitoring.
For how to deploy internet monitoring and filtering, check this guide: How to monitor internet usage?
Second, in “Control Settings”->”IP Management” of WFilter, you can setup ip-mac binding just by a few clicks.i
When ip-mac binding is setup, internet access will be blocked when the user tries to change ip address or mac address.
Please notice: “ip-mac binding” feature of WFilter only works for single segment networks. It is because the real MAC addresses of computers can not be retrieved in a multiple-segments network.
How to activate WFilter?
WFilter supports online activation and Email activation.
If
you choose to activate your product over the Internet, upon your
submisson the activation wizard will detect your Internet connection
and connect to a secure server to transfer your register key to us. The
registration is passed back to you, automatically activating WFilter,
if the register key is valid.
If you choose to activate your
product by email activation, you should input the register key in text
box and click the “confirm”. You will get an activation code. Please
send them to the support email box. The validation code will be sent
back to you within 24 hours. Please copy them in the valiation code
textbox to activate your product.
1. Steps of Online Activation
Online activation requires an available internet connection to connect to WFilter activation server.
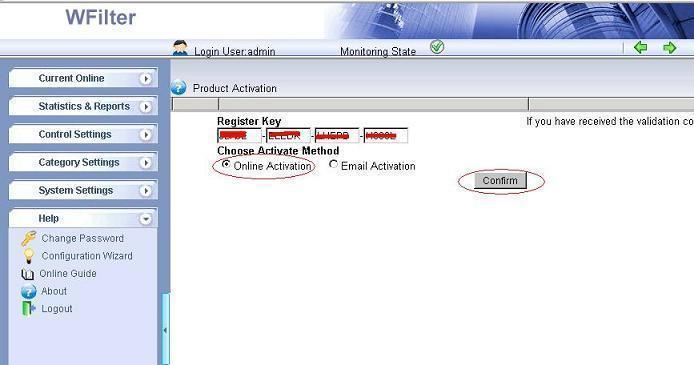
1). In “Help”->”About” of WFilter, click “Product Activation”.
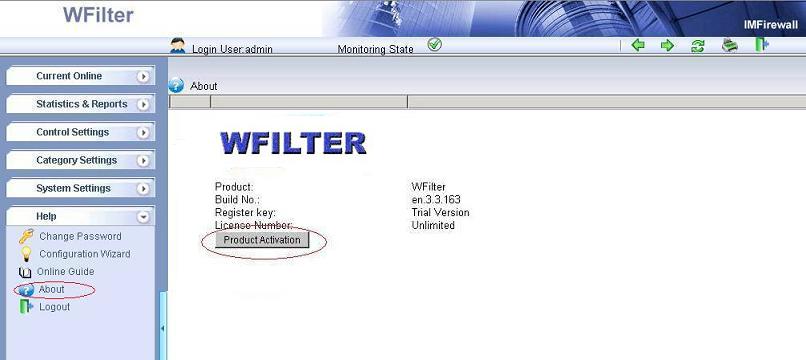
2). Input your key number and use “online activation” to do online activation.
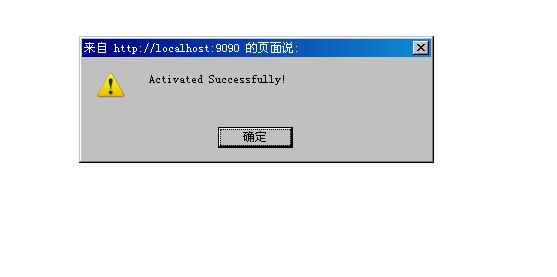
3). Successful activation.
2. Steps of Email Activation
Online activation requires an available internet connection. If you can not connect to WFilter activation server, you also can use “Email Activation”.
1). Input your key number and use “email activation” to do online activation.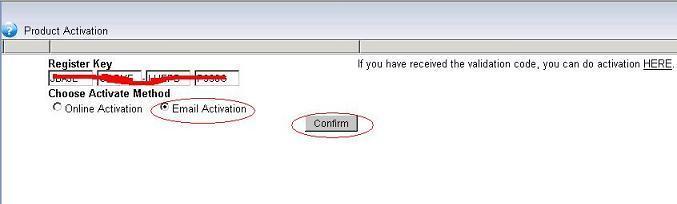
2). In “Email Activation”, copy the activation code and send to support email address.
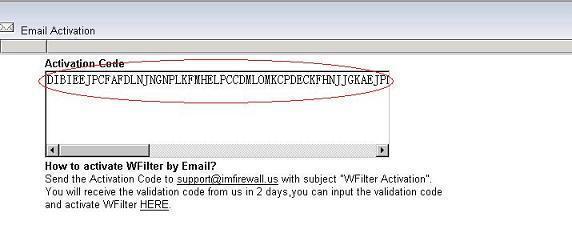
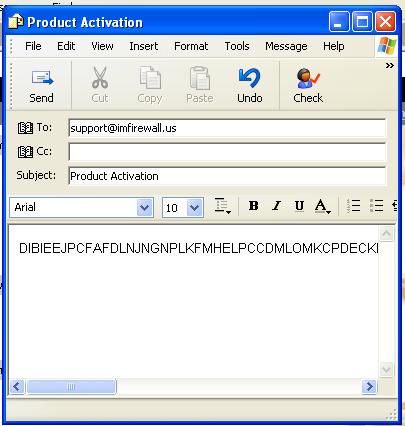
3) It might take several hours to receive the reply email since the response email is sent manually.
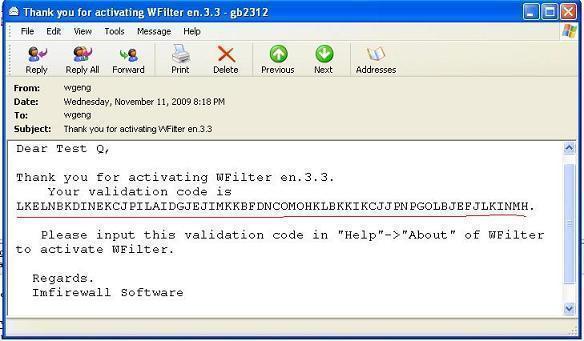
4). In “Help”->”About” of WFilter, you need to enter the received validation code into WFilter.
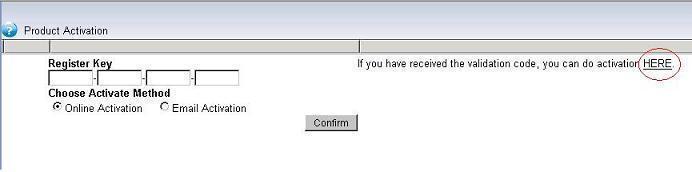

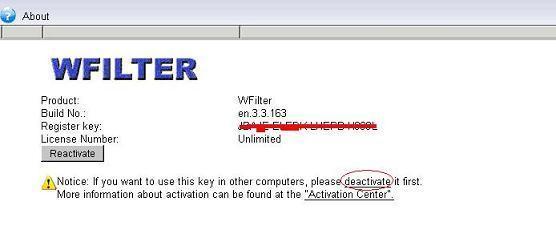
3. De-activation
Sometimes, you might want to move the key to another computer. You need to de-activate this key first.
Click “deactivate” in “Help”->”About” to de-activate the key.
How to filter websites and restrict website access?
Unmanaged websites surfing is killing your productivity. And your computer and network is open to attack when visiting harmful sites.
So it is important to block unwanted websites in your network. Blocking of websites can be done in many ways. These include using free software and windows settings. There are even many add-ons for browsers like Firefox which let you check and restrict websites.
This tutorial will guide you to filter and block websites access in 4 ways.
1. manually editing the “host” file.
In “Local Disk (C:) > WINDOWS > system32> drivers > etc”, you will find a file named “host”. The Hosts file contains the mappings of IP addresses to host names. This file is loaded into memory (cache) at startup, then Windows checks the Hosts file before it queries any DNS servers, which enables it to override addresses in the DNS. This prevents access to the listed sites by redirecting any connection attempts back to the local (your) machine.
You may use “notepad.exe” to edit this Hosts file.
Example – the following entry 127.0.0.1 ad.doubleclick.net blocks all files supplied by that DoubleClick Server to the web page you are viewing.
2. Opendns
OpenDNS offers DNS resolution for consumers and businesses as an alternative to using their Internet service provider’s DNS servers. By collecting a list of malicious sites, OpenDNS blocks access to these sites when a user tries to access them through their service.
OpenDNS enables you to block websites by 50+ categories. OpenDNS also provides whitelist and blacklist features to enable you to create exception cases (“always allow” and “always block”) to complement category-based filtering.
To use OpenDNS service, you need to change your DNS server settings manually.
More information, please visit http://www.opendns.com
3. Router, Firewall or UTM
If you have a powerful router or UTM device, you also can setup web filtering on it.
For more information about UTM solution, please visit http://www.astaro.com
4. Internet filtering products
You also can use internet filtering products to do web filtering. An internet filtering product can be deployed in your network, and it enables you to monitor, filter and block internet activities of all computers from a mirroring port.
More than web filtering, internet filtering product can also block file downloading, block p2p traffic and block messenger.
For internet filtering software, you can try “WFilter Enterprise”, http://www.wfiltericf.com