1. What is tor ?
Tor is a system intended to enable online anonymity, composed of client software and a network of servers which can mask information about users’ locations and other factors which might identify them. Use of this system makes it more difficult to trace internet traffic to the user, including visits to Web sites, online posts, instant messages, and other communication forms. It is intended to protect users’ personal freedom, privacy, and ability to conduct confidential business, by keeping their internet activities from being monitored. The software is open-source and the network is free of charge to use.
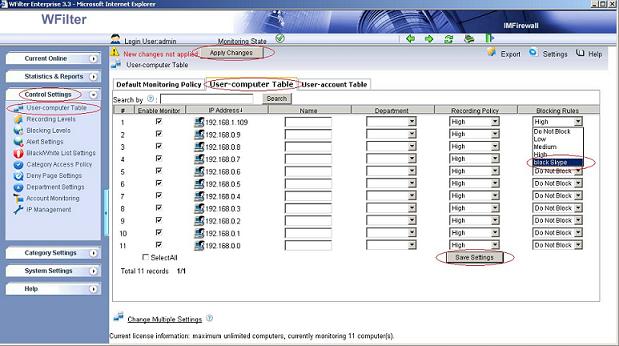
Since client workstations can use tor to bypass internet filtering, so you may want to block tor traffic in your network.
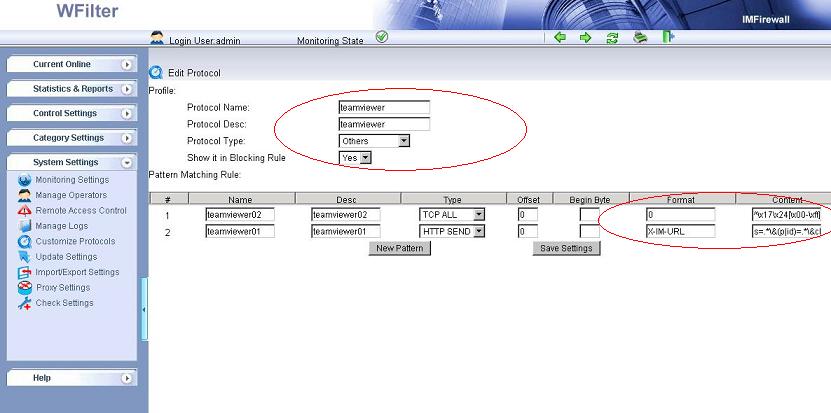
In this tutorial, we will guide you to block tor traffic with “WFilter
Enterprise 3.3″.
2. How to block tor with Wfilter?
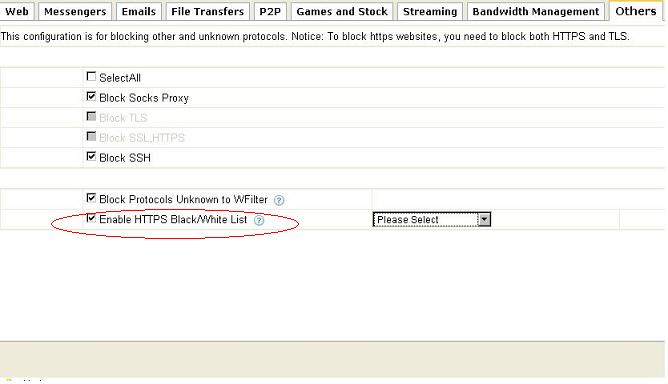
Because tor uses HTTP/TLS to encrypt its traffic, we need to use “HTTPS black/white list” feature of WFilter to filter HTTPS websites to block tor.
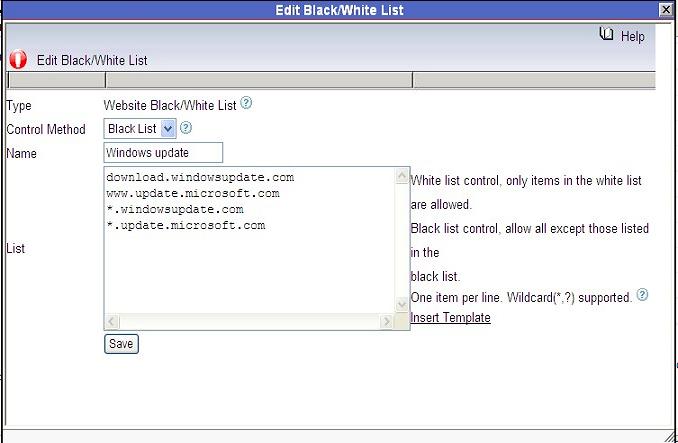
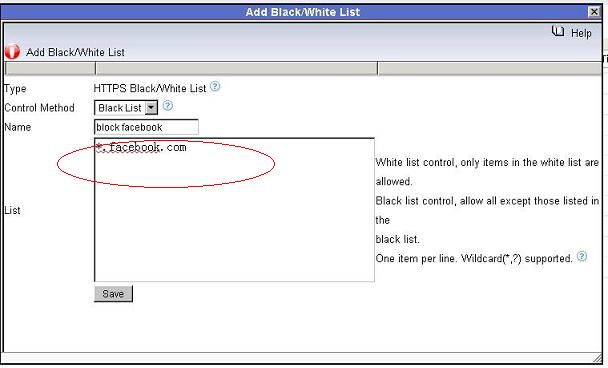
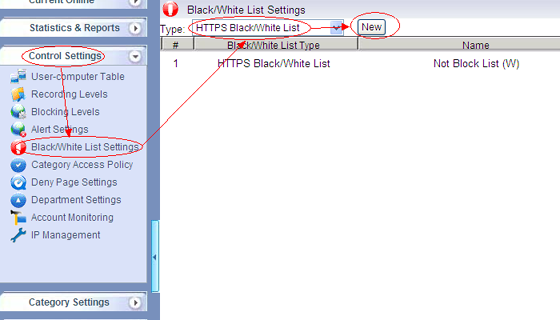
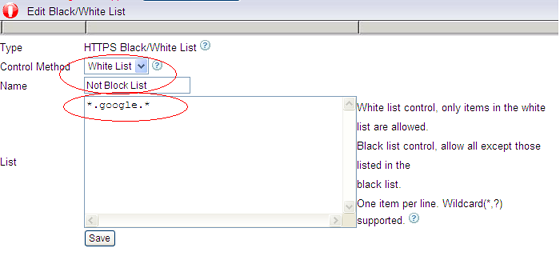
First, create a new “HTTPS White List” and add the allowed HTTPS domains in it. As in below figure:
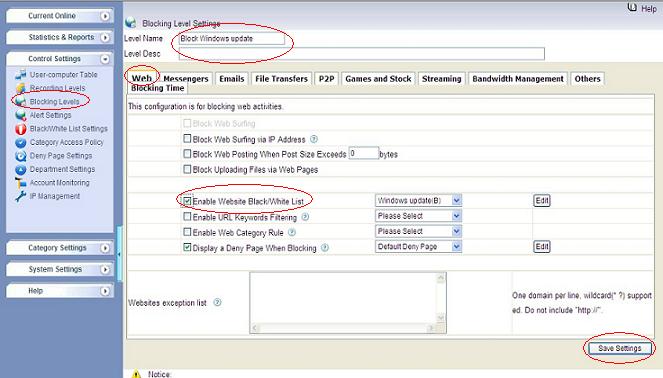
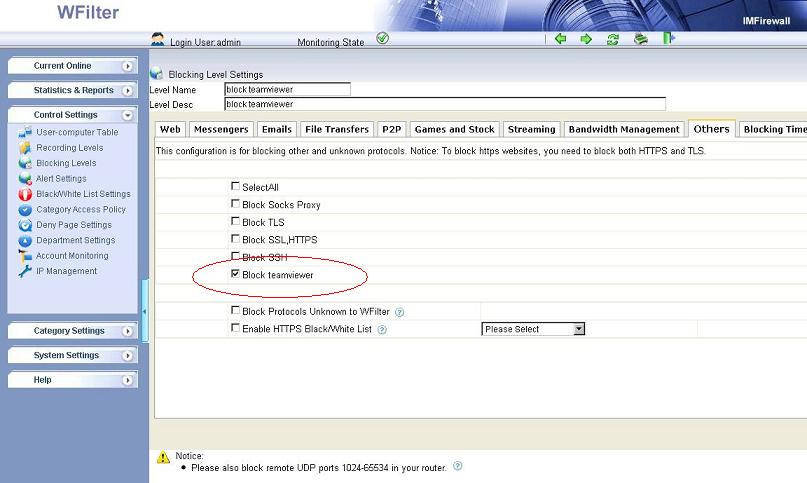
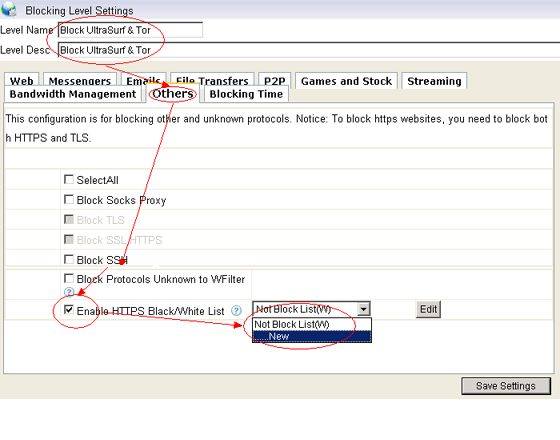
Enable “HTTPS black/white list” in certain blocking level settings.
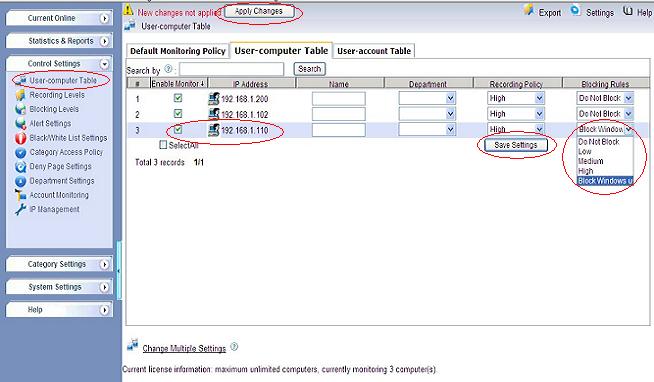
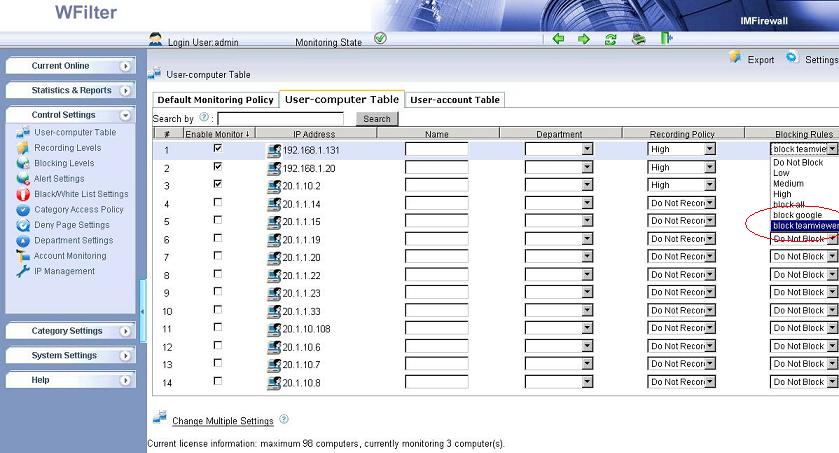
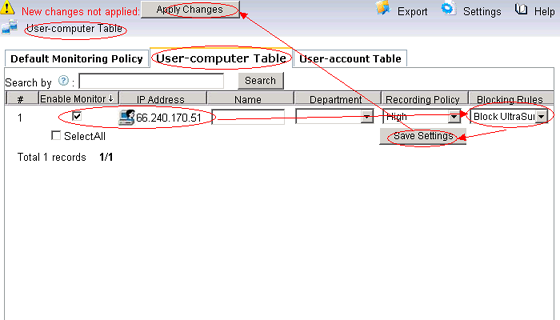
Finally, apply this blocking policy to certain computers.
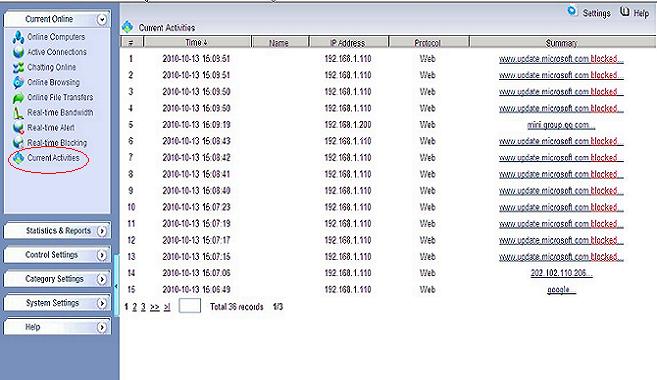
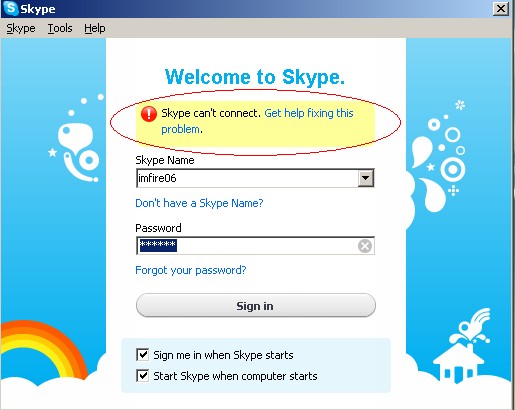
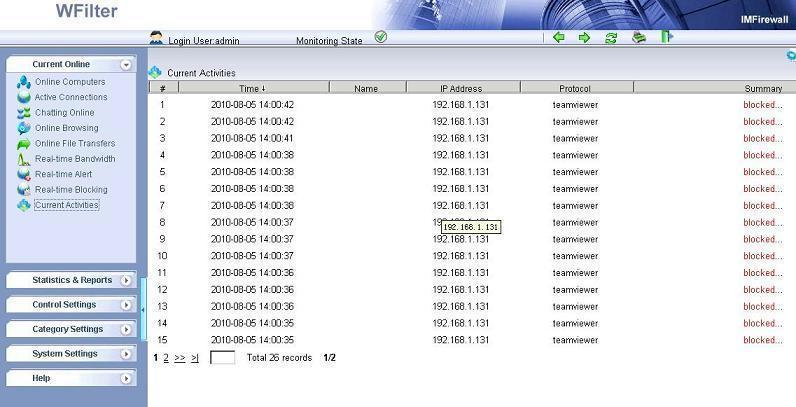
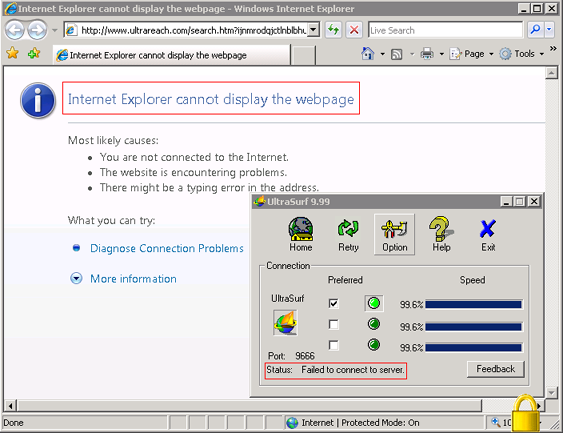
3. Now tor will be completely blocked.
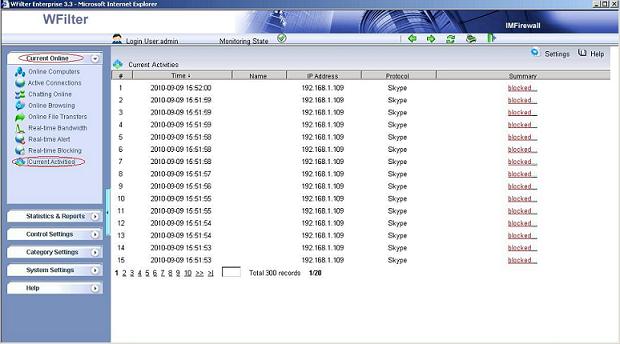
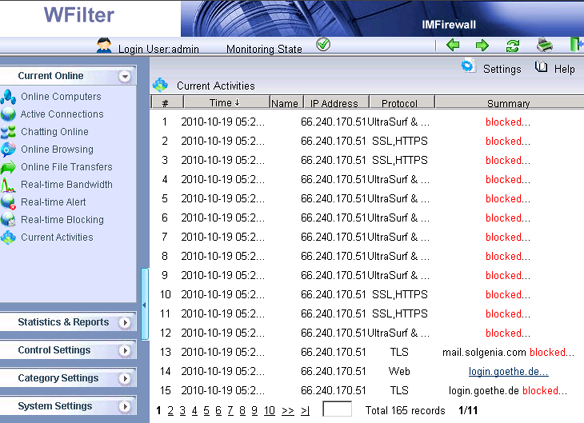
Blocking events in WFilter:
More information, please check “WFilter Enterprise”.
Other related links:
How to block
internet downloading?
How
to monitor internet usage on company network?
Internet
monitoring software for business
How to filter web
surfing?
How to block websites and restrict internet access?
How to block HTTPS websites on my network?