Unmanaged websites surfing is killing your productivity. And your computer and network is open to attack when visiting harmful sites.
So it is important to block unwanted websites in your network. Blocking of websites can be done in many ways. These include using free software and windows settings. There are even many add-ons for browsers like Firefox which let you check and restrict websites.
This tutorial will guide you to filter and block websites access in 4 ways.
1. manually editing the “host” file.
In “Local Disk (C:) > WINDOWS > system32> drivers > etc”, you will find a file named “host”. The Hosts file contains the mappings of IP addresses to host names. This file is loaded into memory (cache) at startup, then Windows checks the Hosts file before it queries any DNS servers, which enables it to override addresses in the DNS. This prevents access to the listed sites by redirecting any connection attempts back to the local (your) machine.
You may use “notepad.exe” to edit this Hosts file.
Example – the following entry 127.0.0.1 ad.doubleclick.net blocks all files supplied by that DoubleClick Server to the web page you are viewing.
2. Opendns
OpenDNS offers DNS resolution for consumers and businesses as an alternative to using their Internet service provider’s DNS servers. By collecting a list of malicious sites, OpenDNS blocks access to these sites when a user tries to access them through their service.
OpenDNS enables you to block websites by 50+ categories. OpenDNS also provides whitelist and blacklist features to enable you to create exception cases (“always allow” and “always block”) to complement category-based filtering.
To use OpenDNS service, you need to change your DNS server settings manually.
More information, please visit http://www.opendns.com
3. Router, Firewall or UTM
If you have a powerful router or UTM device, you also can setup web filtering on it.
For more information about UTM solution, please visit http://www.astaro.com
4. Internet filtering products
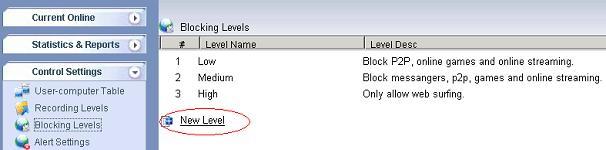
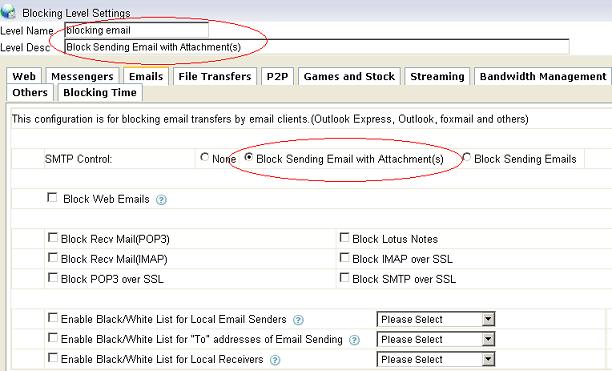
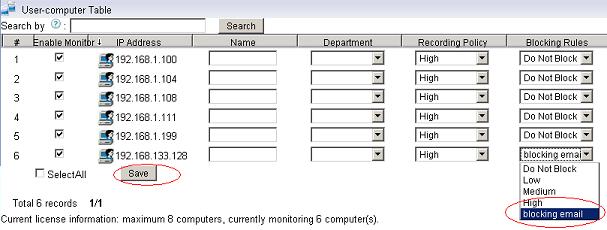
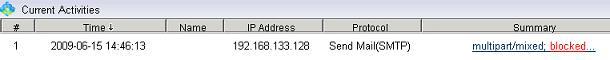
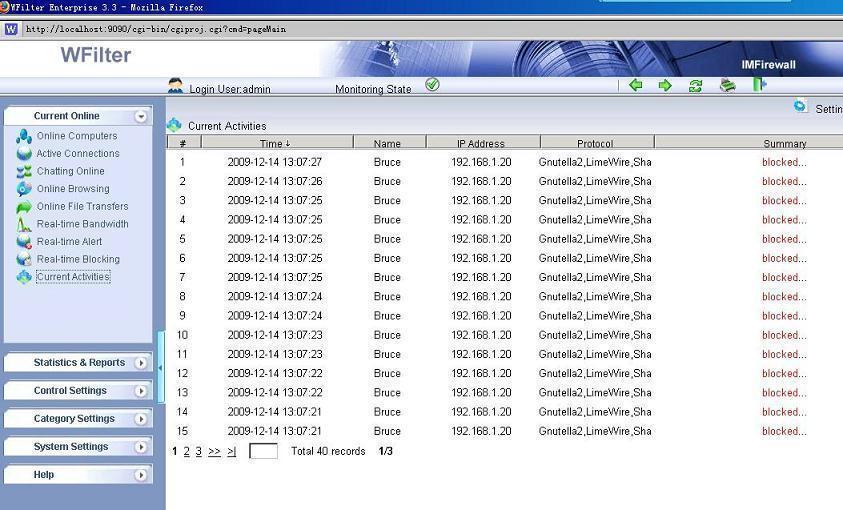
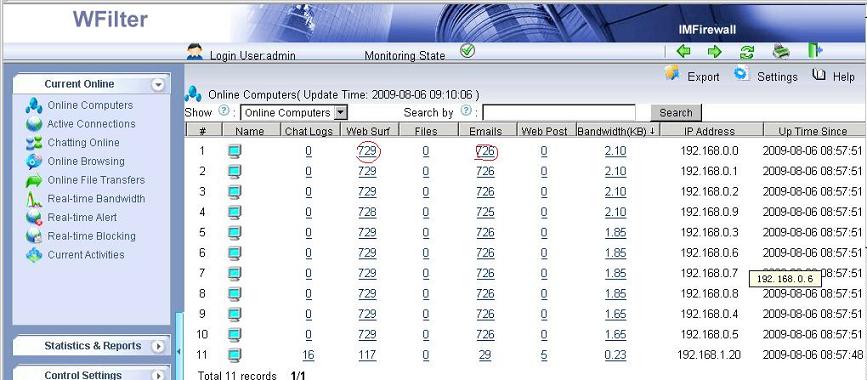
You also can use internet filtering products to do web filtering. An internet filtering product can be deployed in your network, and it enables you to monitor, filter and block internet activities of all computers from a mirroring port.
More than web filtering, internet filtering product can also block file downloading, block p2p traffic and block messenger.
For internet filtering software, you can try “WFilter Enterprise”, http://www.wfiltericf.com