There are a lot of products for you to manage your network: firewall, content filtering, web filtering proxy… Some users might get confused to choose them.
Since more and more customers had requested a comparison of WFilter to other similar products, I wrote this guide to list some important differences.
WFilter is a passby internet monitoring and filtering software program. It monitors network traffic from a mirroring port in your switch. When a TCP connection needs to be blocked, WFilter will send 1-2 RST packets to reset this connection. This is called “Passby Filtering”. More technical details of WFilter can be found at: WFilter Technologies
WFilter VS firewall program/appliance
Advantages:
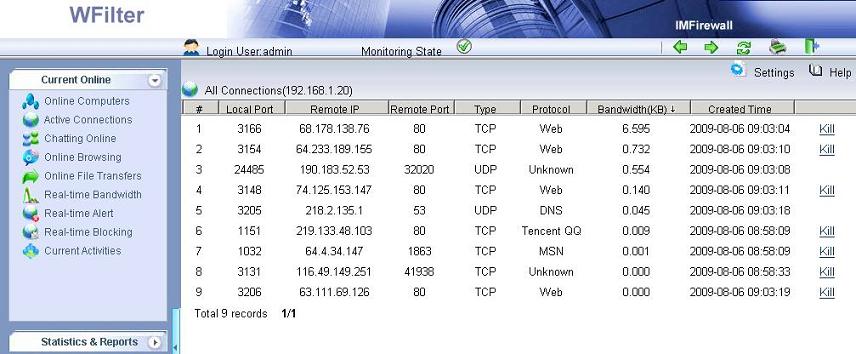
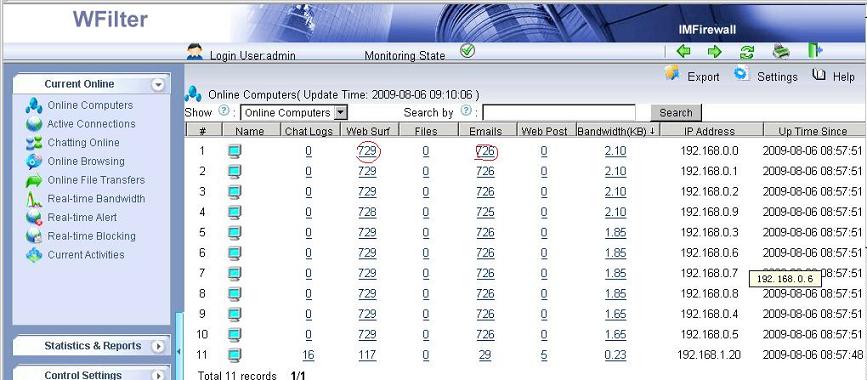
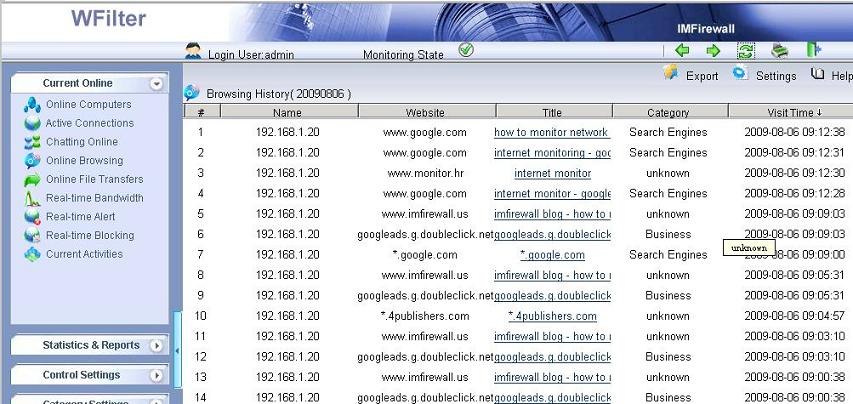
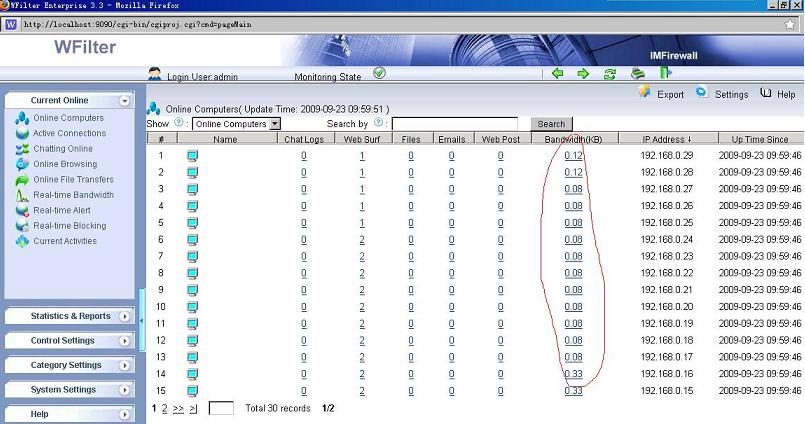
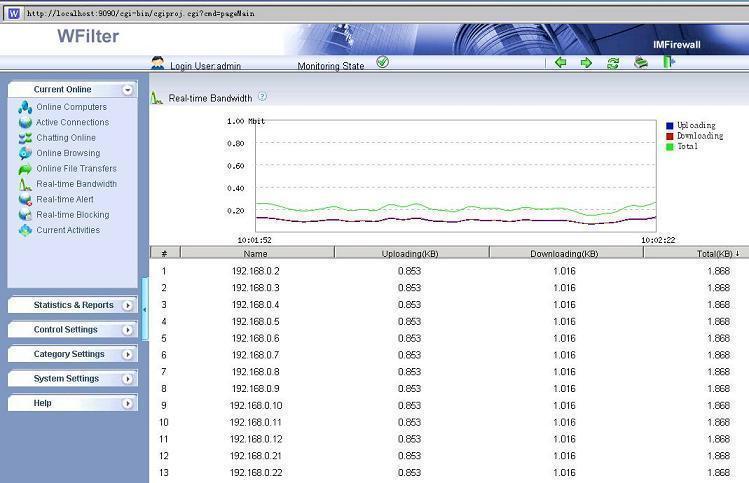
1. WFilter monitor and archive most internet activities, while firewalls don’t keep internet usage details.
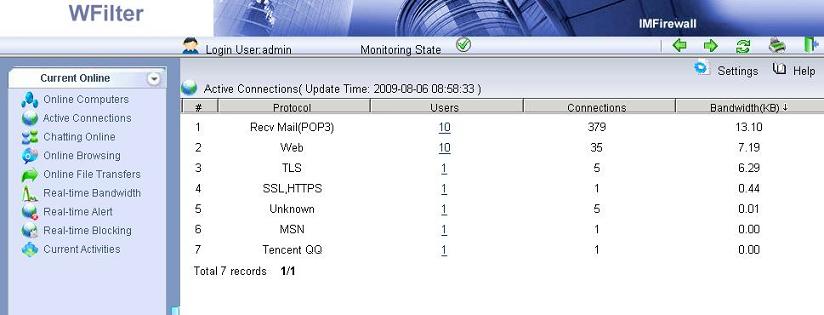
2. WFilter parses protocols at the application layer, it can recognize 100+ common protocols according to their signatures and behaviors. Most firewall program/application filters packets based on ports or ip addresses.
3. WFilter analyse copies of internet packets from a mirroring port of your switch. It is easy to be deployed, without any delay of your network. However, a firewall program/appliance needs to be deployed at the edge of your network. And since each packet goes through the firewall program/appliance, there will be a slight delay.
4. If the WFilter server goes down, the Internet connection stays alive. If the firewall program/appliance hangs, you will not be able to access internet.
5. WFilter is a content filtering product. It is designed to monitor and filter internet usage of employees to raise your productivity. However, a firewall program/appliance is designed to filter network packets and protect your network.
Disadvantages:
1. WFilter can not block UDP packets. So you also need to block UDP ports in your router/firewall.
2. WFilter consumes more memory and disk space of your computer. If you archive all internet activity, it might consume 2-3M disk space for each monitored computer every day.
WFilter VS open source web filtering projects
Some open source projects, like “SQUID” and “dansguardian”, also provide web filtering solutions. Below I list some major differences:
1. Most open source projects work as a proxy server. It requires you to change your internet access to proxy mode.
2. Most open source projects are web filtering only. Blocking of p2p traffic, internet monitoring/archieving are not supported.
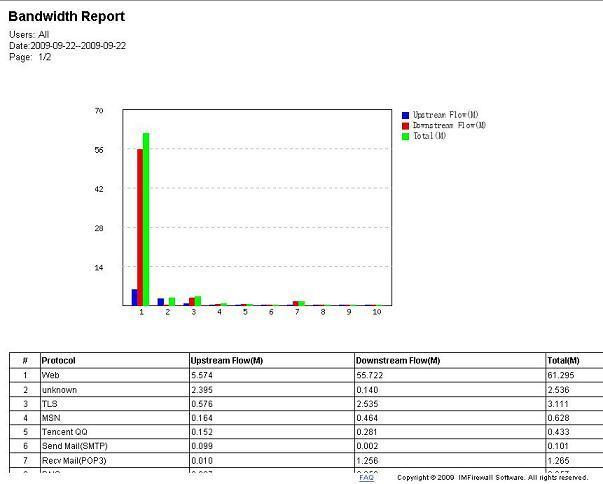
3. Lack of statistics and reports for open source projects.
4. Lack of support for open source projects. Since protocols are changing, live update/support is required to keep your pattern database up to date, while most open source projects don’t have such support. In IMFirewall protocol lab, to keep our pattern database up to date, we have a system to monitor most common internet products/protocols, so when a new version of certain product is released, our team will work on it immediately.
Try “WFilter Enterprise” by yourself: http://www.wfiltericf.com/WFilter.htm