WFilter can monitor and filter computers internet activities in your network. In WFilter, two monitoring modes are available: “by ip address” and “by MAC address”. In “by ip address” monitoring mode, WFilter identifies a computer based on its ip address, while it identifies a computer based on its MAC address in “by mac address” monitoring mode.
However, if computers ip addresses are not fixed in your network. You might have trouble to identify a computer to set its monitoring/blocking policy.
This tutorial will introduce you several solutions to identify computers in your network in WFilter.
1. Monitor and block by AD users
Since WFilter can be integrated with Microsoft active directory, you don’t need to face the trouble of identifying computers if you have an available AD.
With “account monitoring” enabled, you can set blocking policy based on AD users, despite which computers they are using.
Please check this document for more details about “account monitoring”: How to do monitoring based on user accounts?
2. Identify computers by MAC addresses
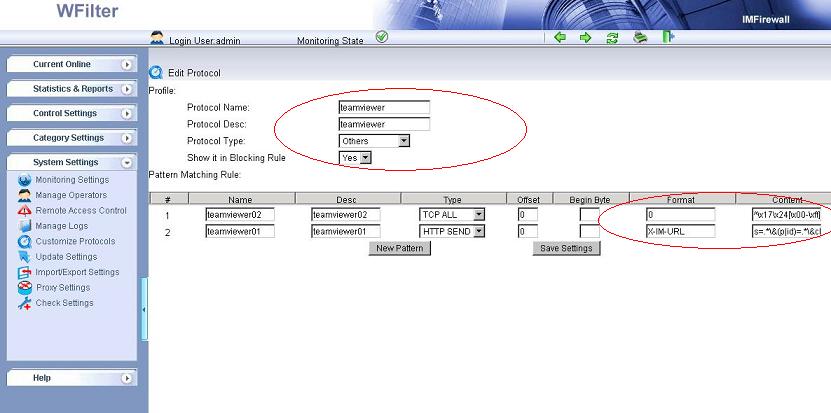
With “by mac address” monitoring mode, WFilter identifies a computer by its MAC address. MAC address is assigned by the manufacturer of a network interface card (NIC) and are stored in its hardware. It won’t change unless the NIC hardware is replaced.
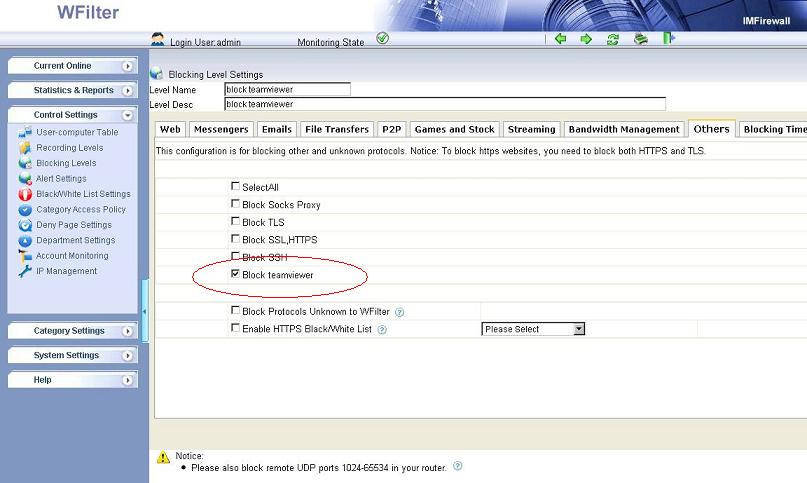
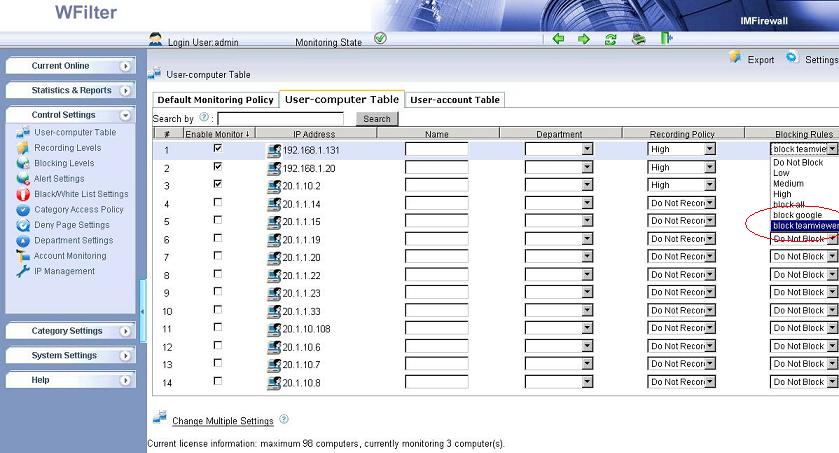
When you set a recording policy or blocking policy to one computer in “user-computer table”, certain settings will be bound to its mac address. Even its ip address is changed, certain settings will not be lost.
However, “By MAC address” monitoring mode is only available for single-segment networks, because a computer’s mac address can not be retrieved when it’s located behind a router.
Therefore, in a single-segment network, “by mac addresses” will be a good choice if your ip addresses are dynamic.
3. Identify computers by IP addresses
If your network is multi-segments, you only can use “by ip address” monitoring mode. Therefore, we recommend you to make ip addresses static in a multi-segments network. If you want to leave the ip addresses as dynamic, the only solution left is “Monitor and block by AD users” as discussed above.
More information, please check “WFilter Enterprise”.
Other related links:
How to block internet
downloading?
How to monitor
internet usage on company networks?
Internet monitoring
software for business
How to
filter web surfing?
How to block
websites and restrict internet access?
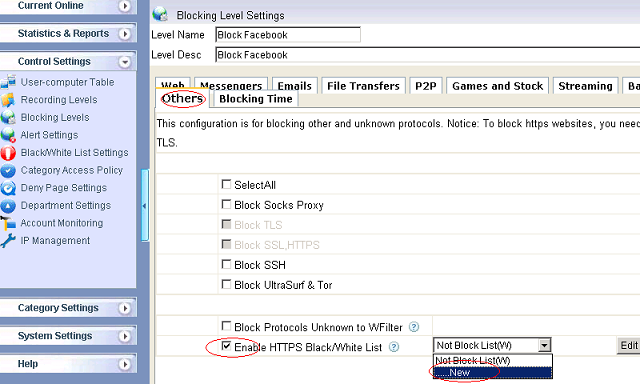
How to block HTTPS
websites on my network?
How to setup ip-mac binding in WFilter?
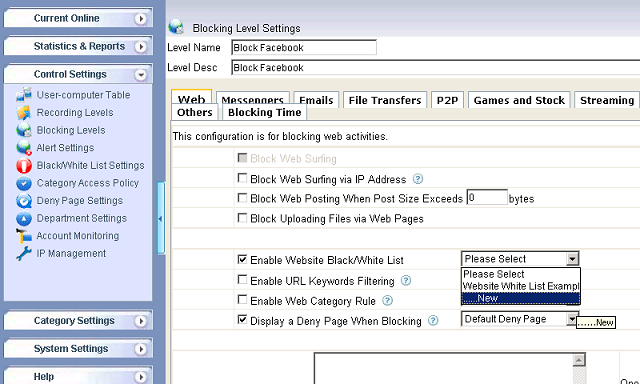
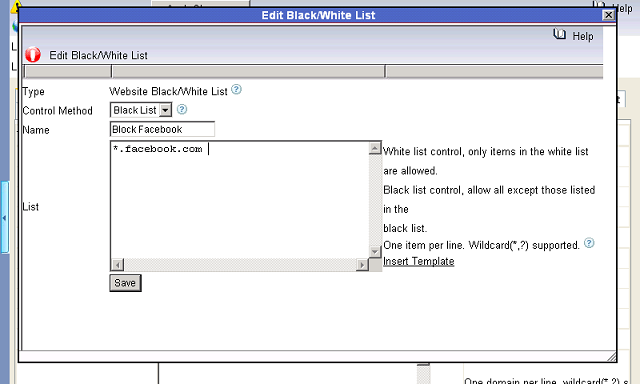
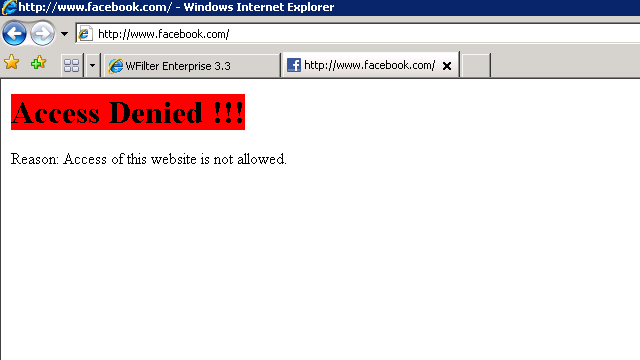
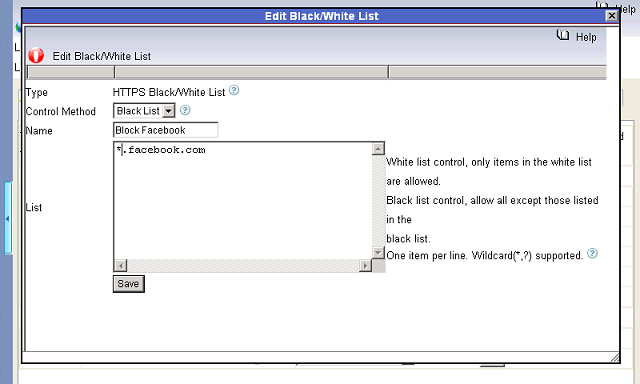
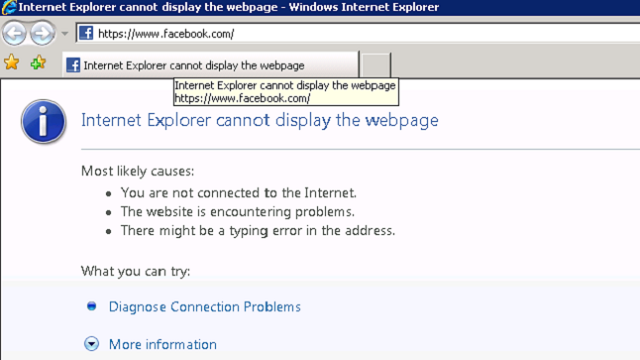
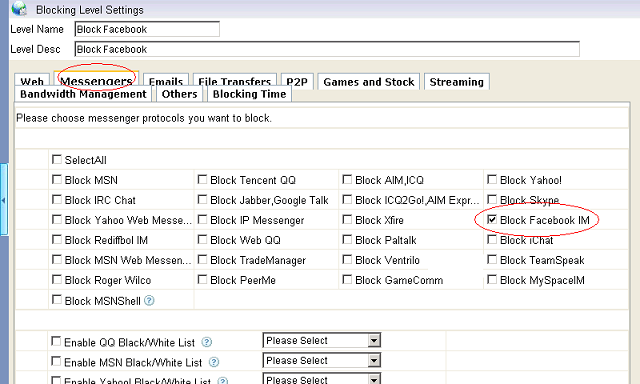
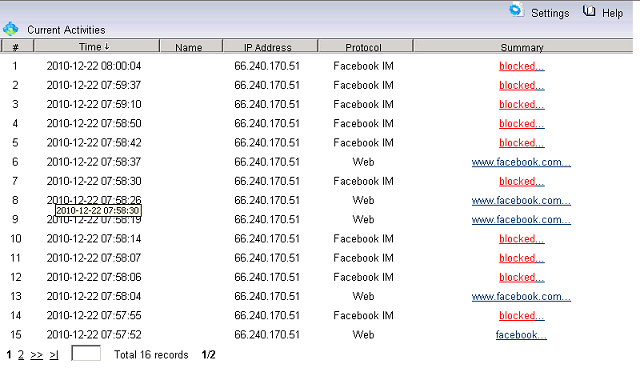
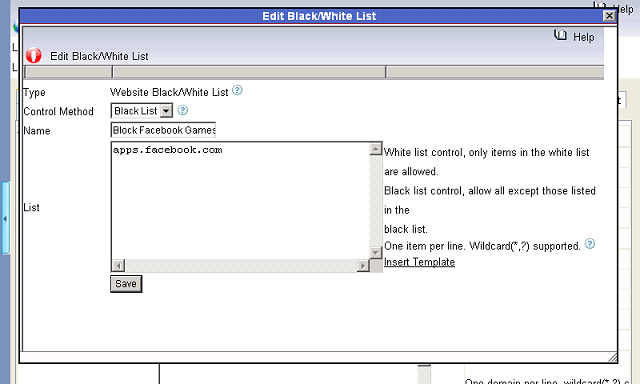
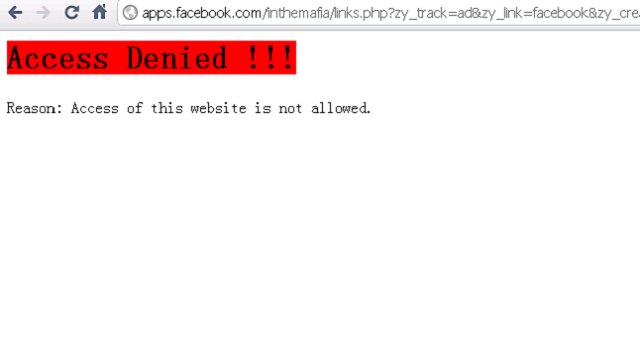
How to block facebook at work of network computers?